Cyber threat intelligence comes in many different flavors that address different problems and different roles within the organization. At the end of the day, however, as with any cyber security-related capability, you need to answer the “so what” question. What does any of this intelligence mean? And does it help us achieve the desired outcome(s)?
In my last CISO role, “so what” was the threshold used in internal and external discussions to either keep the conversation moving forward or stopping it dead in its tracks. This litmus test was something I learned when briefing senior brass in the DoD on cyber security and budgetary issues – justification was always needed. Every conversation I had on those topics with senior leaders always had a “so what” context to them – if you wanted to “pass go and collect $200” you better have had a well-researched and measured answer. If you weren’t prepared to answer the ‘“so what” question, you were sure to quickly lose a seat at the table.
From an internal justification perspective, here are some examples of the “so what” line of questioning:
• So what organizational risk does this effort reduce or give us more context around?
• So what manual tasks does this help automate?
• So what cost does this reduce?
• So what level of labor and material will this take to get done?
From an external perspective, the questions go down a slightly different, but similar path:
• So what new tasks will my team have after your solution is deployed on top of what we already have to get done?
• So what new information are you bringing my team beyond what I already have?
• So what is the cost of this new information?
• So what problem does this capability solve for me?
• So what? Why do I care?
Now let’s put this more specifically in the context of threat intelligence. When we build out cyber risk profiles for our customers, we usually start with the following types of “so what” questions that drive further context and value to the threat intelligence we ultimately deliver:
• So what is the organization’s level of “presence” out in the wild?
o What is our fraud footprint?
o What are the threats to our Infrastructure?
o What are the threats to our Employees?
o What are the threats to our Brand and Reputation?
o What are the threats to our Customers?
• So what types of threats are occurring in the industry?
• So what threats are changing over time?
• So what threats affect our partners, suppliers or competitors?
• So what are the threat actors’ capabilities, opportunities and intent?
• So what controls mitigate that vulnerability or threat? Are we applying the right resources to the right controls?
• So what control failures would impact the business?
• So what threats could directly impact our organization?
Think about how most businesses are dependent on the digital world. As such, cyber risk is expanding well beyond the traditional nuts and bolts of the IT Infrastructure. To conduct business in today’s marketplaces, organizations must leverage a cyber infrastructure in some way, shape or form. Because of this, organizations ultimately extend their “presence” into multiple environments and with that presence comes threats to the products and services delivered.
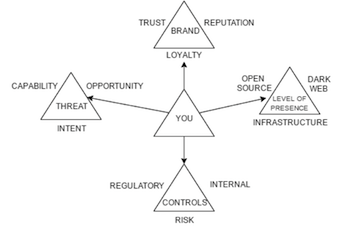 To tie the business, the extended level of presence, threats and controls altogether, I created this diagram that further expands on the Threat Triangle concept I wrote about in my last article.
To tie the business, the extended level of presence, threats and controls altogether, I created this diagram that further expands on the Threat Triangle concept I wrote about in my last article.
The business ecosystem has become much more complex with the growing level of presence. Digital interaction with customers is standard practice. Data is shared with your partners and suppliers digitally, and orders are fulfilled digitally. You must manage your social media, brand and reputation digitally. You’re tracking every move your customers make, what they bought, what they like and what they are doing digitally. Your employees and customers are communicating on Twitter, Facebook, Linkedin, Reddit and many other social platforms right now.
Adversaries spend their time researching and understanding the ins and outs of your ecosystem to find the hole(s) they can exploit. And oftentimes they end up knowing your ecosystem better than you. Adversaries are:
• Peeling back layers and probing your network for weak spots
• Collecting information on what you do, how you communicate and what information you have that is valuable
• Learning what your company culture looks like
• Learning how to leverage your infrastructure for monetary gain
• Calling your help desk to reset a credential posing as a legitimate user
• Spear-phishing your departments with ransomware
• Selling stolen corporate credentials on the black market
• Researching who your suppliers are and probing them for weaknesses in order to gain access to your systems
These types of threats occur every single day across the globe, impacting brands, reputations, customers, revenue, spend, and infrastructure.
How do you keep situational awareness of what is going out there and how much of a presence your organization has? How do you know what resources to apply to the most important probl
em areas?
Strategic and operational cyber threat intelligence provides the guidance to grow and mature the level of cyber risk awareness across the organization. Threat intelligence can be for cybersecurity what business intelligence does for sales, finance, marketing, etc. In order to quickly and effectively pivot, in order to get situational awareness of a problem area, in order to understand your level of “presence” within a given problem area – you must run an intelligence-driven security approach. As with any cyber security-related effort, threat intelligence also must pass the “so what” test. Hopefully these ideas can help you pass it with flying colors.














