Adobe’s product security incident response team (PSIRT) accidentally published a private PGP key on its blog. The compromised key was quickly revoked and a new key was generated after the incident came to light.
Adobe PSIRT updated its PGP key on Friday and published the new public key, which should have been valid until September 2018, on its blog. However, Finland-based security researcher Juho Nurminen noticed that scrolling down in the blog post also revealed the private PGP key, which Adobe, obviously, should have kept private.
Pretty Good Privacy (PGP), which relies on the OpenPGP standard, allows users to protect information sent over the Internet, typically via email. Confidential data is encrypted using a public key, which users share with anyone who wants to communicate with them, and decrypted using a private key, which should be kept secret.
In Adobe’s case, the accidental disclosure of the private key could have allowed anyone to decrypt encrypted emails that normally only the company would be able to read.
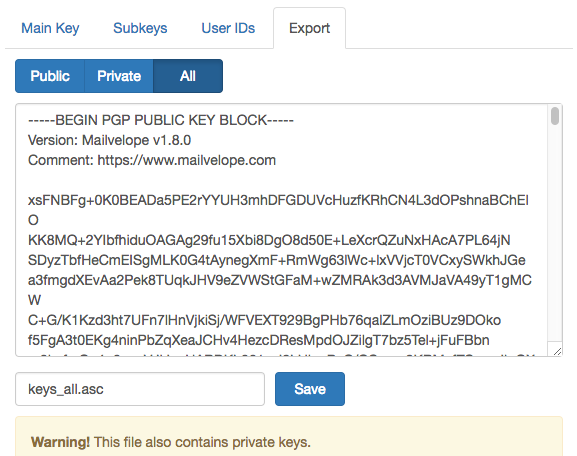
The key accidentally published on Adobe’s blog was generated using Mailvelope, an open source browser extension for OpenPGP. Some security experts pointed out that the mistake made by Adobe was likely due to the way the Mailvelope interface is designed.
When users want to export a key, they can export either the public key, the private key, or both by selecting the “All” option. The Adobe employee responsible for the leak likely selected the “All” option and copied the generated data without realizing that it contained the private key as well.
However, it’s worth noting that the Mailvelope interface does display a warning when private keys are exported.
Adobe has removed the blog post and revoked the compromised private key, but users captured screenshots and a copy of the post still exists on websites such as Archive.is. The company has generated a new key pair, this time using GPGTools.
SecurityWeek has reached out to Adobe for comment and will update this article if the company responds.
“If you let your your PGP/GPG private key slip, your leak cuts both ways, potentially affecting both you and the other person in the communication, for messages in either direction,” said Sophos’ Paul Ducklin.
“Don’t make this mistake yourself if you use public-key cryptography tools,” the expert added. “It’s an easy mistake to make when you’re copying text – so, to borrow a saying from carpentry, measure twice, cut once.”
UPDATE. Adobe sent SecurityWeek the following statement:
“Adobe is aware of the issue and has revoked the PGP key in question and published a new public and private key. The PGP key in question was used exclusively for email correspondence between external security researchers and the Adobe security team, and there is no impact to Adobe customers.”
Related: PGP Email Encryption Fundamentally Broken
Related: Side-Channel Attack on Libgcrypt Allows RSA Key Recovery
Related: Google Hands Over Email Encryption App to Community














