Researchers at Trusteer have discovered a variant of Zeus with a P2P component that is targeting high profile sites such as Facebook, Google, Hotmail, and Yahoo in order to compromise debit and credit card data.
The attacks being carried out by the P2P version of Zeus use a basic form of social engineering. Depending on the service being targeted at the time, users are presented with offers for additional security measures and rebates.
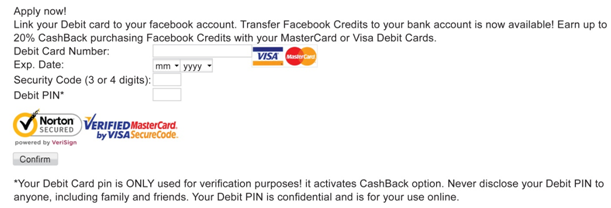
In the case of Facebook, malware injects the necessary code so that an offer of 20% cash back is displayed. All the user has to do is link their Visa or MasterCard debit card to their Facebook account. Of course that offer is completely fraudulent, but that won’t prevent some people from trying to save a buck unfortunately. The cash back bonus is awarded when the victim purchases Facebook points. The order form will require the card number, expiration, CVV (security code), and PIN.
For Google and Yahoo users, the Zeus variant injects the needed form data and presents an offer of additional security. During this scam, users are told they can opt to authenticate to the 3D Secure service used by the Verified by Visa and MasterCard SecureCode programs. In order to participate, the victims will need to link their debit cards to their webmail account, and all future 3D Secure authentication sessions will be performed via Google Checkout or Yahoo Checkout.
“The attack is not compromising the 3D Secure service or authentication mechanism, but rather leveraging the Verified by Visa and MasterCard SecureCode brands to make the scam more credible,” Trusteer explains in a blog post.
As for Hotmail, the scam is similar to the one used against Google and Yahoo. Only this time, a 3D Secure-like service is offered. As in the previous attacks, the victim will need to link their debit card to their webmail account.
“This attack is a clever example of how fraudsters are using trusted brands, social network/email service providers and debit card providers, to get victim’s to put down their guard and surrender their debit card information,” the blog post concluded.
“These web injects are well crafted both from a visual and content perspective, making it difficult to identify them as a fraud. It’s also ironic how in the Google Mail, Hotmail and Yahoo scams, the fraudsters are using the fear of the very cybercrime they are committing to prey on their victims.”















