Private equity giant Symphony Technology Group (STG) on Tuesday announced the launch of a new security service edge (SSE) company named Skyhigh Security.
STG in January announced the launch of Trellix, an extended detection and response (XDR) solutions provider created following the merger of McAfee Enterprise and FireEye. At the time, STG noted that McAfee Enterprise would be split into two organizations: one of them is Trellix and the second company is Skyhigh Security.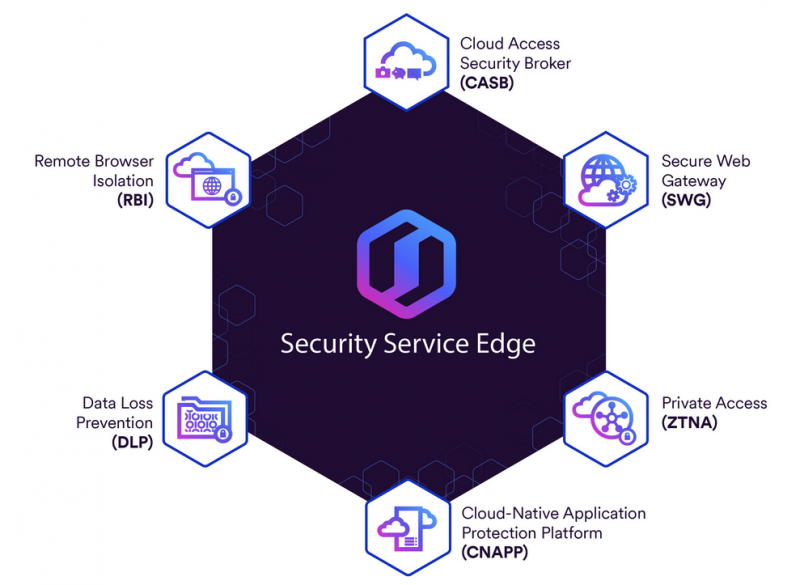
Skyhigh Security combines resources from McAfee Enterprise with technologies acquired in the past from Skyhigh Networks, Light Point Security, NanoSec and Secure Computing.
Skyhigh Security’s SSE portfolio includes Secure Web Gateway (SWG), Cloud Access Security Broker (CASB), Zero Trust Access Network (ZTNA), Cloud Data Loss Prevention (DLP), Remote Browser Isolation, Cloud Firewall, and Cloud Native Application Protection Platform (CNAPP) solutions.
STG said the new company was created to “satisfy the growing cloud security requirements for large and small organizations.”
Gee Rittenhouse, who previously led Cisco’s cybersecurity business, will serve as Skyhigh Security’s CEO.
“Skyhigh Security has created a comprehensive security platform to secure both data access and data use via unified policies and data awareness,” Rittenhouse said. “Organizations can now have complete visibility and control and seamlessly monitor and mitigate security risks—achieving lower associated costs, driving greater efficiencies and keeping pace with the speed of innovation.”
Related: FireEye, Mandiant Split Apart in $1.2B Private Equity Deal
Related: McAfee Sheds Enterprise Business in $4 Billion Deal
Related: High-Severity Vulnerabilities Patched in McAfee Enterprise Product














