As new IPv4 addresses are more and more difficult to come by, spammers are increasingly hijacking existing IP address ranges for their nefarious purposes, Spamhaus researchers warn.
The issue, researchers explain, is that spammers need a constant flow of fresh IP addresses, because those they use get a bad reputation of being sources of spam quite fast. This issue isn’t new, and spammers are constantly looking for new means of getting fresh IP addresses.
Back in January, researchers accused Verizon of routing over 4 million IP addresses that were in the hands of cybercriminals. At the time, the Internet Service Provider (ISP) was accused of not looking closely at the routing requests, which allowed cybercriminals to use their stolen addresses unhindered.
Now, Spamhaus reveals that spammers are “hijacking existing IP address ranges from under the noses of the legitimate owners and ARIN (American Registry for Internet Numbers),” and that Legacy IP address ranges are most targeted by cybercriminals. These addresses, issued before ARIN’s inception in 1997, can’t be revoked even if the yearly fees aren’t paid, meaning that they can lie dormant, sometimes forgotten by the legitimate owners.
One of the first incidents where hijacked legacy IP address ranges were used for spam was observed in 2012, when cybercriminals were abusing the 147.50.0.0/16 ranges, owned by Chemstress Consultant Company. The original record is dated in 1991, but hijackers started their abuse in 2011 by registering a domain to “Timothy Tausch,” the name from the original ARIN records.
After that, the hijackers tricked ARIN into updating Timothy Tausch’s contact information with an email address they were in control of. Next, the 147.50.0.0/16 IP addresses started being announced on behalf of the hijacker. The nefarious activity was rapidly shut down by the ISP for non-payment, researchers say.
In recent years, hijacking incidents have been getting worse, researchers say. Below, you can see a chart of the network BGP announcements of ranges believed to be hijacked (only ranges with “live” SBL listings are included – nobody has claimed legitimate ownership yet).
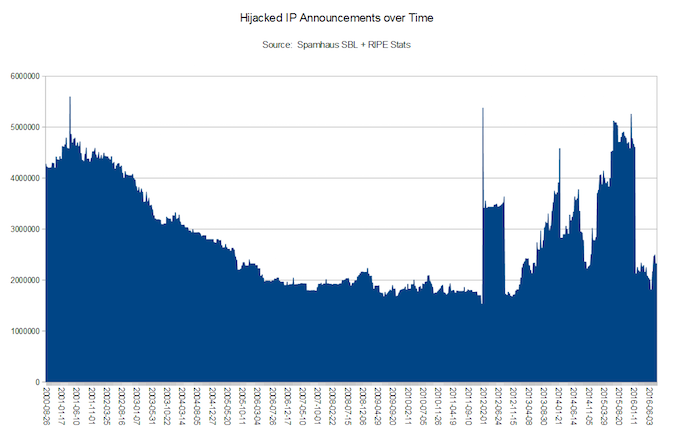
According to Spamhaus, while the announcements on the left-hand side of the chart are mainly legitimate, they slowly decrease as more companies that become defunct stop using their IP address ranges.
“Then, in recent years, these ranges start being hijacked by spammers, at times, announcements of up to 5 million IP addresses,” Spamhaus researchers explain. “Sending email through hijacked IP address ranges is of course one of the few criminal provisions of the U.S. CAN-SPAM Act. And hijacking usually involves other serious crimes such as wire fraud, forgery, and identity theft.”
According to Spamhaus, it appears that this type of malicious activity might continue until law enforcement begins prosecuting the criminal hijacking gangs and the spammers they work with. They also explain that ARIN’s ability to take action is sometimes limited, because it must abide by procedures defined via its Policy Development Process, and might not be able to take action even when notified of false information being added to its records.















