A sophisticated Zeus campaign stole an estimated €36 million, or $47 million, from over 30,000 customers across more than 30 banks in Europe this summer.
The Eurograbber campaign, as it has been named, used custom versions of Zeus and Zeus in the mobile (ZITMO) Trojans to bypass the two-factor authentication measures to compromise customer bank accounts, Darrell Burkey, director of IPS products at Check Point Software Technologies, told SecurityWeek. The attack intercepted SMS messages sent to customers to confirm financial transactions.
 Israel-based Versafe learned about the campaign after some of its customers were affected in early August, and analyzed the attack with the team from Check Point, Eyal Gruner, a security engineer at Versafe, told SecurityWeek. Check Point and Versafe worked with European law enforcement and various Internet Service Providers to shut down the command-and-control servers in mid-October. The researchers jointly published a report detailing their findings on Wednesday.
Israel-based Versafe learned about the campaign after some of its customers were affected in early August, and analyzed the attack with the team from Check Point, Eyal Gruner, a security engineer at Versafe, told SecurityWeek. Check Point and Versafe worked with European law enforcement and various Internet Service Providers to shut down the command-and-control servers in mid-October. The researchers jointly published a report detailing their findings on Wednesday.
The attack hit all the “key buzzwords, as it was sophisticated, multi-dimensional, stealthy, and successful,” Burkey said.
Victims were tricked into downloading a custom version of the Zeus Trojan, either by clicking on a link in an email or by being redirected to a malicious page while browsing online, Burkey said. Once the computer was infected, the malware could steal login credentials for online banking and intercept banking sessions.
However, Eurograbber didn’t just stop with infecting the computer. When the customer logged into online banking for the first time after being infected, the malware prompted the customer to enter the mobile phone number in order to “upgrade the security of the online banking system.” The user then received a link in an SMS message to a “banking software security upgrade,” which was actually a variant of Zeus in the mobile. Zeus in the mobile can target Android, BlackBerry, and Symbian phones, as well as jailbroken iPhones.
What made Eurograbber different from past Zeus campaigns, other than the sheer amount of money stolen, was the fact that it successfully compromised both the user’s computer and mobile device to bypass the bank’s two-factor authentication mechanisms, Burkey said.
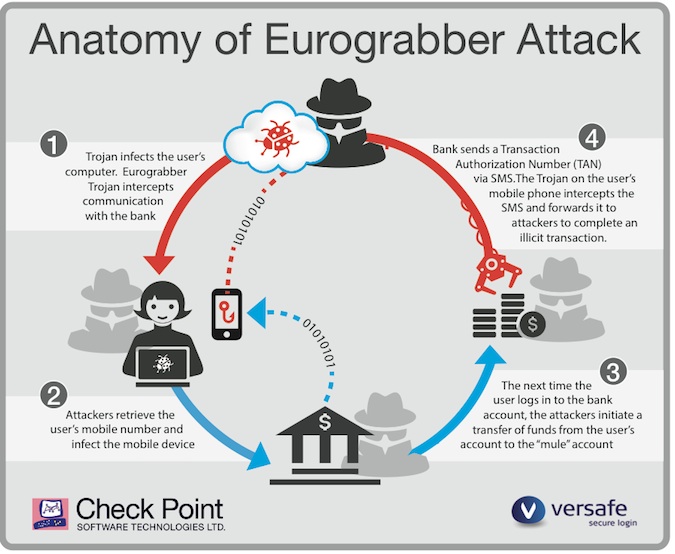
Many European banks have rolled out two-factor authentication schemes that rely on the customer having a mobile phone. When users set up financial transactions, the bank sends a “transaction authentication number” to the registered mobile phone. The customer has to enter that unique code back on the Website to complete the transaction. The idea being, of course, that if the user has access to the physical device to see the code, then the transaction request must be legitimate.
“Eurograbber was designed to work within that banking system,” Burkey said.
With the account number, password, and the SMS messages containing the TAN, Eurograbber criminals were able to set up automatic transfers from €500 to €250,000 from victim accounts to those belonging to a network of money mules. The initial victims were in Italy, but the operation also spread to Germany, Holland, and Spain, Burkey said.
While it is very difficult to definitively determine the attack origin, the Eurograbber gang was most likely based out of Eastern Europe, Burkey said. The operation had command-and-control infrastructure all over the world. Check Point and Versafe worked with European law enforcement and ISPs to shut down the C&C servers in October, Gruner said.
The researchers have not detected additional outbreaks or seen a recurrence of the campaign, leading them to believe it has been successfully dismantled. However, Gruner was cautious, pointing out that unless users had detected and removed the Zeus malware from their computers and mobile phones, they were still vulnerable to future operations. Since the gang remains at large, it is very possible they can start over in a new location, set up the infrastructure and launch a new campaign, Gruner said.
“This iteration is finished, but it can be resurrected again,” Burkey agreed.















