A researcher has detailed several new variants of an attack named HTTP request smuggling, and he has proposed some new defenses against such attacks.
HTTP request smuggling, also known as HTTP desyncing, has been known since 2005, but Amit Klein, VP of security research at SafeBreach, believes the method has not been fully analyzed, which is why he has decided to conduct a research project focusing on this attack technique.
HTTP request smuggling leverages the way HTTP devices handle a stream of requests, specifically how the stream is divided into individual requests. An attacker can abuse this to “smuggle” a malicious HTTP request to a server through an HTTP device (i.e. a proxy) by leveraging the discrepancy in how the server interprets the stream and how the HTTP device views the stream.
Specifically, an HTTP request smuggling attack, which can be launched remotely over the internet, can allow a hacker to bypass security controls, gain access to sensitive data, and compromise other users of the targeted app.
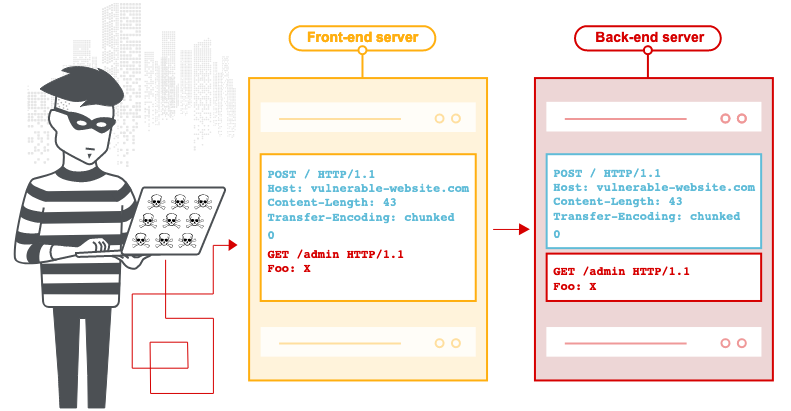
While the attack method has been known for more than a decade, it still hasn’t been fully mitigated.
Klein has managed to identify five new attack variants and he has released proof-of-concept (PoC) exploits. He demonstrated his findings using the Abyss X1 web server from Aprelium and the Squid caching and forwarding HTTP web proxy.
The developers of Abyss and Squid have been notified of the vulnerabilities exploited by Klein during his research, and they have released patches and mitigations.
One of the attacks bypasses the OWASP ModSecurity Core Rule Set (CRS), which provides generic attack detection rules for ModSecurity or other web application firewalls. OWASP has also released fixes after being notified.
Klein told SecurityWeek ahead of his talk on HTTP request smuggling at the Black Hat conference that an attacker needs to find combinations of web servers and proxy servers with “matching” vulnerabilities in order to launch an attack, which makes it difficult to determine exactly how many servers are impacted. However, an attacker can simply try to launch an attack to determine if a system is vulnerable. “The attack is not demanding resource-wise, so there’s no downside to simply trying it,” Klein said.
In his research, he demonstrated a web cache poisoning attack, in which the attacker forces the proxy server to cache the content of one URL for a request of a different URL.
He says attacks can be launched en-masse through a proxy server against multiple different web servers or against multiple proxy servers.
“I don’t think it’s a good idea to launch an attack en-masse through a single proxy server to a single web server as there may be interference (due to the proxy keeping a small pool of connections to the web server),” he explained.
While there haven’t been any reports of HTTP request smuggling being used in the wild, Klein has pointed out that attacks may have been launched but were not detected by the target.
“The actual impact of the attack happens (at least for web cache poisoning) at the caching proxy server, which can be off the premises of the organization managing the web server. As such, I suspect that the attack can go unnoticed (and the artifacts overwritten when the cached page expires or evicted from the cache),” he told SecurityWeek.
The researcher has proposed some new defenses against HTTP request smuggling attacks, and during his tests he identified some interesting behavior in the case of some payloads, which could pave the way for future research in this area.
Related: New Ransomware Process Leverages Native Windows Features
Related: Common Infiltration, Exfiltration Methods Still Successful
Related: Vulnerability in McAfee Antivirus Products Allows DLL Hijacking














