A ransomware group has hit at least one water company in the United Kingdom, but there is some confusion over whose systems were actually breached.
The Cl0p ransomware group has claimed on its Tor-based leak website that it has breached the systems of Thames Water, which advertises itself as the UK’s largest water and wastewater company, serving 15 million people.
However, cybersecurity experts have pointed out that while Cl0p names Thames Water on its site, the files leaked as proof of the breach actually appear to belong to a different water company named South Staffordshire, whose subsidiaries, South Staffs Water and Cambridge Water, serve 1.6 million people and tens of thousands of businesses in the UK.
On its website, Cl0p names Thames Water with the company’s address and revenue, but a phone number and a second address shown on the same page belong to South Staffs Water. Some leaked documents also reference South Staffordshire and South Staffs Water.
At least one local British news website posted an alarmist headline — now removed — warning about possible water contamination resulting from the alleged Thames Water hack.
Thames Water issued a statement on Tuesday saying that the media reports are false. Also on Tuesday, South Staffordshire confirmed being targeted by cybercriminals.
South Staffordshire provided few details, but said the incident disrupted its corporate IT network and claimed that its ability to supply safe water has not been affected “thanks to the robust systems and controls over water supply and quality we have in place at all times”.
South Staffordshire reassuring customers about the safety of the water supply and the alarmist headlines are related to the hackers claiming to have gained access to all of the company’s systems, including SCADA (supervisory control and data acquisition) systems that, according to the cybercriminals, “control chemicals in water”.
“It would be easy to change chemical composition for their water but it is important to note we are not interested in causing harm to people,” the cybercriminals said.
Two of the screenshots they published do show human-machine interface (HMI) systems that could potentially allow someone to tamper with industrial control systems (ICS), but some HMIs are only used for monitoring purposes. One of the screenshots shows HMIs that seem to relate to wastewater treatment.
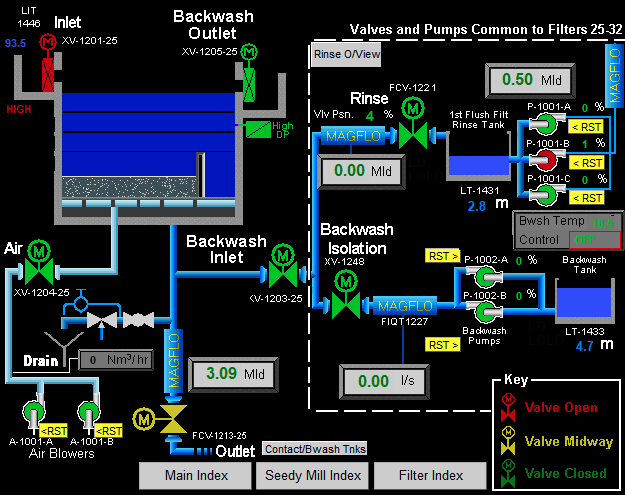
Ilan Barda, CEO of OT cybersecurity firm Radiflow, has confirmed for SecurityWeek that the screenshots are from a real HMI system and that they can be used to control the chemicals in the water purification process.
“However, such chemical processes are non-linear – minor changes can quickly drift the desired pH level out of safety ranges. So to maintain a usable pH level, it is required to have a real-time managed control loop which is done in the PLC level. As such configuration changes via the HMI will be detected and alerted at the PLC level and are unlikely to cause damage to the output water supply,” Barda explained.
“Note however that when an attacker gains access to such an internal OT computer they can also install a hidden malware that will further spread in the internal OT network and might eventually reach assets in which it can cause real damage,” he added. “So even though the site might remain operational it is highly recommended to perform an in-depth cyber inspection of all the assets for such additional dormant malwares.”
The cybercriminals claim to have stolen more than 5 Tb of information after spending months in the company’s networks. They also claim that files have not been encrypted — as in many other attacks — and that the victim did offer to pay a ransom, but the amount was too low.
Hundreds of companies have been targeted by the Cl0p ransomware and NCC Group reported recently that many of its victims are in the industrial sector. Several people accused of having some type of role in the Cl0p operation have been arrested, but that does not appear to have had a big impact.
It’s not uncommon for threat actors to target companies in the water sector, and ransomware groups have been known to access SCADA systems in these organizations. While in some cases the attackers might not know too much about how the compromised ICS works, there are some threat actors that know exactly what they are doing.
*updated with information from Ilan Barda
Related: US Says National Water Supply ‘Absolutely’ Vulnerable to Hackers
Related: Kansas Man Admits Hacking Public Water Facility
Related: Probe Into Florida Water Plant Hack Led to Discovery of Watering Hole Attack















