The COVID-19 pandemic has apparently resulted in industrial systems being increasingly targeted by malicious actors through brute-force attacks on the Remote Desktop Protocol (RDP), Kaspersky reported on Thursday.
Kaspersky’s report on the industrial threat landscape for the first half of 2020 reveals that the number of attacks aimed at RDP on industrial computers increased steadily between February and May.
The cybersecurity firm has seen brute-force attacks against RDP passwords on 0.16% of the industrial control systems (ICS) it protected in February and 0.33% in May. The percentage dropped slightly in June, but still remained at an above average level.
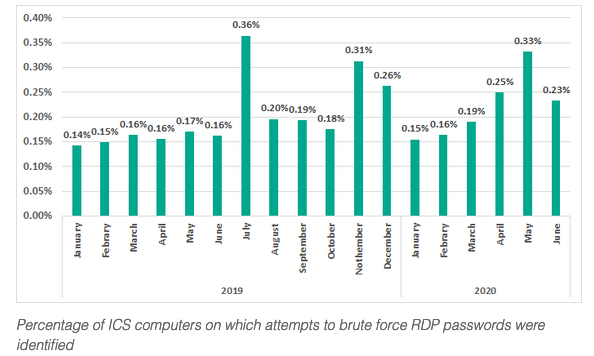
The higher number of attacks on RDP coincides with more industrial organizations using RDP during the COVID-19 pandemic to enable their employees to remotely access and manage resources.
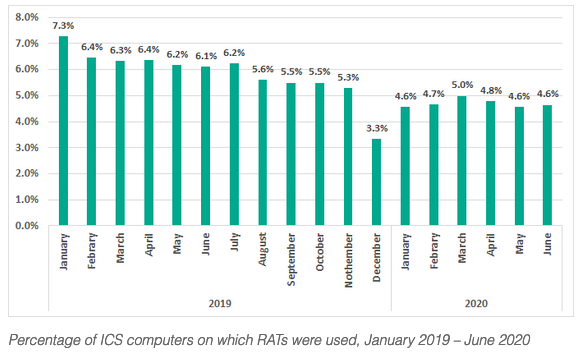
Kaspersky last year observed that the use of remote administration tools (RATs) by industrial organizations decreased steadily, until February 2020, when it started to stabilize, which experts believe could also be a result of the pandemic as organizations needed to maintain the ability to remotely access systems.
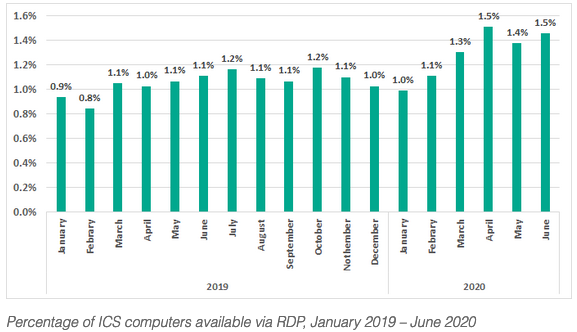
“We believe that the increase in the percentage of ICS computers on which RDP is used could be an indication that most new RDP sessions were authorized by IT and information security services. In fact, all other things being equal, it may be easier to configure and control the secure operation of RDP services than that of any other RAT applications. It would seem that allowing new RDP installations was a compromise caused by the objective need to perform production-related tasks remotely in a pandemic,” Kaspersky noted in its report.
Learn more about threats to industrial systems at SecurityWeek’s 2020 ICS Cyber Security Conference and SecurityWeek’s Security Summits virtual event series
It added, “The increase in the percentage of attacked ICS computers on which attempts to brute force the RDP password were detected (and prevented) may seem insignificant, but it should be remembered that any such attack, if successful, would immediately have provided the attackers with remote access to engineering computers and ICS systems. The danger posed by such attacks should not be underestimated.”
Kaspersky said it blocked attacks on 32.6% of the ICS devices it protected in the first half of 2020, a decrease of 6.6 percentage points compared to the second half of 2019.
Industrial systems from which the cybersecurity firm collected threat data include SCADA servers, historians, OPC systems, engineering and operator workstations, HMIs, computers used to manage industrial networks, and computers used to develop industrial automation software.
The company said its products blocked over 19,000 malware variants belonging to over 4,100 families. The main source of these threats was the internet, followed by removable devices and email.
As for regional statistics, Kaspersky said Asia and Africa saw the highest percentage of attacks. Australia, Europe, the US and Canada are at the other end of the chart.
Related: Industrial Systems Can Be Hacked Remotely via VPN Vulnerabilities
Related: Over 70% of ICS Vulnerabilities Disclosed in First Half of 2020 Remotely Exploitable















