ATLANTA — SECURITYWEEK 2019 ICS CYBER SECURITY CONFERENCE — Outdated and unsupported operating systems are still present and they still pose a serious risk in many industrial organizations, according to a new report from industrial cybersecurity firm CyberX.
The company’s 2020 Global IoT/ICS Risk Report is based on data passively collected by CyberX from over 1,800 networks around the world between October 2018 and October 2019. It’s worth mentioning that the previous annual risk report from CyberX was based on information from roughly 850 networks.
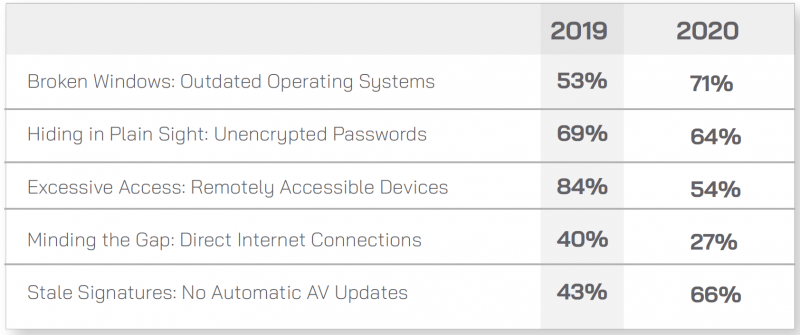
According to the latest data from CyberX, 62% of analyzed sites house devices running outdated and unsupported versions of Windows, such as Windows XP and 2000, and the percentage jumps to 71% if Windows 7, which reaches end of support in January 2020, is also included.
The use of Windows versions that no longer receive security updates poses a serious risk as it allows attackers to compromise systems using vulnerabilities for which details and PoC exploits are often publicly available. Moreover, the company pointed out, even if Microsoft releases patches for unsupported versions of Windows to address high-risk flaws, as it did in the case of the BlueKeep vulnerability, it may not be easy for an organization to deploy the patch on industrial systems.
CyberX says it frequently finds malware on production networks, and unsupported or unpatched Windows devices significantly contribute to this.
The company identified suspicious activity in 22% of the sites it monitored. Suspicious activity can include scans, abnormal HTTP headers, known malware, and an excessive number of connections between devices. Some of this activity might not be malicious, but CyberX pointed out that without proper monitoring systems in place it can be difficult to differentiate malicious from legitimate activity.
Allowing remote access to devices can pose serious risks. CyberX found that over half of the sites it analyzed had devices that could be accessed remotely via RDP, SSH or VNC. A related problem involves allowing devices to be directly accessed from the internet, an issue identified in 27% of cases.
CyberX also found that in 64% of cases unencrypted passwords traverse an organization’s networks. This makes it easier for attackers to intercept passwords, which can be highly problematic due to the fact that passwords are rarely, if ever, changed in IoT and ICS environments.
Finally, the company learned that in two-thirds of cases automatic updates are not enabled for security software.
Compared to last year, the percentage of organizations with remotely accessible and internet-exposed devices has decreased significantly.
On the other hand, the percentage of sites housing devices running outdated operating systems has increased, and so has the percentage of sites where automatic updates are not enabled for security software.
CyberX noticed that organizations in the oil and gas and energy utilities sectors appear more secure compared to organizations in other sectors, such as manufacturing, pharmaceutical, chemical and transportation. This isn’t surprising considering that the oil and gas and energy utilities are regulated industries, which, the company notes, are “typically much more locked down.”
While it may seem that there have been significant improvements in some areas, particularly when it comes to remote access, CyberX has pointed out that the improved metrics are mainly the result of a higher percentage of customers from regulated industries (i.e. oil and gas and energy utilities).
“The data clearly illustrates that IoT/ICS networks continue to be soft targets for adversaries,” CyberX said.















