Several months after a researcher issued a warning about over 1,200 Phoenix Contact programmable logic controllers (PLCs) being exposed to remote attacks from the internet, many organizations still haven’t taken any measures to secure their systems.
In a blog post published on Medium in early February, cybersecurity researcher Sergiu Sechel warned that two types of Phoenix Contact PLCs that should normally be deployed only on closed networks were easily accessible from the internet. The PC Worx communication protocol used by these products for management and configuration does not include any authentication mechanisms.
The configuration interface of some Phoenix Contact ILC and AXC controllers can be accessed remotely without any authentication over TCP port 1962. This configuration interface can be used to obtain information about the device, change its IP address and other settings, start or stop the PLC, create a backup for its entire configuration, update or modify the firmware, and enable or disable firmware services.
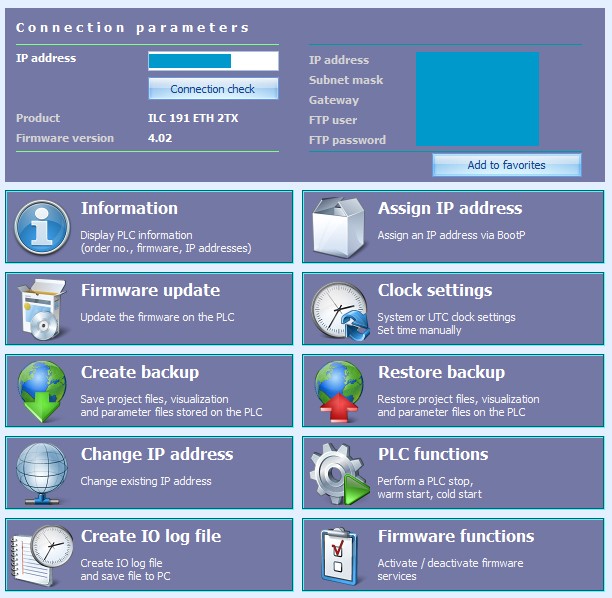
In a simple attack, malicious actors could gain access to the admin interface and turn off the device, Sechel told SecurityWeek.
“A complex attack would require the update of a modified firmware on the device that would enable the attacker to execute arbitrary commands on the controller,” the researcher explained. “This would require the purchase of a ILC controller and the software to reverse engineer or modify the firmware. By abusing the create backup feature an attacker can obtain knowledge on what type of infrastructure is managed by the ILC controller.”
The vulnerability, tracked as CVE-2019-9201 and classified as “critical” with a CVSS score of 9.8, impacts ILC1x0 and ILC1x1 controllers, and AXIOLINE AXC1050 and AXC3050 controllers.
The ILC devices are inline controllers often used to transmit information over long distances, including by utilities, power plants and manufacturing facilities. The AXC modular controllers are designed for the Axioline I/O system and they provide performance and easy handling in harsh industrial environments.
Learn More About Flaws in Industrial Products at SecurityWeek’s 2019 ICS Cyber Security Conference
When he publicly disclosed his findings in February, Sechel reported that a Shodan search had identified over 1,200 exposed ILC controllers, mainly in Italy, Germany, the Netherlands, Turkey and Spain. A search for AXC 1050 devices revealed 66 instances. The same Shodan searches conducted now show that there are still roughly 1,000 ILC and 50 AXC controllers that can be accessed directly from the web.
While the researcher disclosed his findings several months ago, the Germany-based industrial automation solutions provider Phoenix Contact and Germany’s VDE CERT agency only released an advisory roughly one week ago, in late June. Sechel, who has Global Industrial Cyber Security Professional (GICSP) certification, reported the vulnerability through MITRE.
The researcher told SecurityWeek that all the devices visible on Shodan should be considered vulnerable to hacker attacks from the internet.
Moreover, the expert has warned that the actual number of vulnerable devices is likely higher as he says Shodan does not have full visibility into the IPv4 address space. Scans conducted using NMAP can reveal additional vulnerable systems.
“There are different subnets that block Shodan scans,” Sechel noted. “In a specific assessment, one can try to detect if an organization has ILC/AXC controllers by issuing NMAP scans, even if there are no search results on Shodan. For example, if we are assessing the security of a critical infrastructure provider we will use NMAP (where possible and if permitted — ICS devices are very delicate) to try to detect different ICS which for example are not visible from the internet.”
Phoenix Contact has told customers that the impacted devices are designed for use only in closed networks or they should be protected with firewalls.
“If the use of an affected controller in an unprotected open network cannot be avoided, the affected communication protocols should be disabled by using the CPU services via console,” Phoenix said in its advisory, which has also been published by VDE CERT.
Sechel pointed out that one of the simplest and most effective mitigations for this vulnerability would be to use a VPN to ensure that only authorized users are able to access the PLCs remotely. However, in reality, that only limits the risk to internal attackers, which could still compromise the devices.
Related: Flaws Expose Phoenix Contact Industrial Switches to Attacks
Related: Flaws in Phoenix Contact Automationworx Allow Code Execution via Malicious Files
Related: Serious Flaws Found in Phoenix Contact Industrial Switches













