The threat actor behind the cyberespionage campaign dubbed Machete continues to be active and some of its most recent attacks targeted the military in Venezuela and Ecuador, ESET reported on Monday.
Attacks launched by the Machete group were first analyzed by Kaspersky in 2014. The hackers have been active since at least 2010, focusing on Spanish-speaking countries, particularly in Latin America. Some targets have also been identified in Russia (the embassies of Spanish-speaking countries), the United States, Sweden, China, Korea, the United Kingdom, Canada, Germany and Ukraine.
Both Kaspersky’s 2014 report and ESET’s new research suggest that the attackers are native Spanish speakers, but research published in 2017 by Cylance noted that the attacks may originate from Brazil, particularly due to the fact that no victims had been spotted in this country and the most heavily targeted countries share a land border with Brazil. The official language in Brazil is Portuguese, but recent estimates said roughly 460,000 Brazilians, representing 0.23% of the population, speak Spanish fluently.
The recent Machete operations observed by ESET mostly targeted Venezuela (75%), followed by Ecuador (16%), Colombia (7%), and Nicaragua (2%). In the case of Venezuela, over half of the compromised machines belong to the country’s military, while others belong to police, education, foreign affairs and other organizations. Ecuador’s military has also been targeted in recent attacks.
According to ESET, over 50 compromised machines communicated with Machete command and control (C&C) servers between March and May 2019, and the hackers managed to steal hundreds of gigabytes of confidential documents each week.
ESET researchers have noticed that the attackers have used spear-phishing emails tailored to each victim, in some cases delivering their Python-based malware using previously stolen documents.
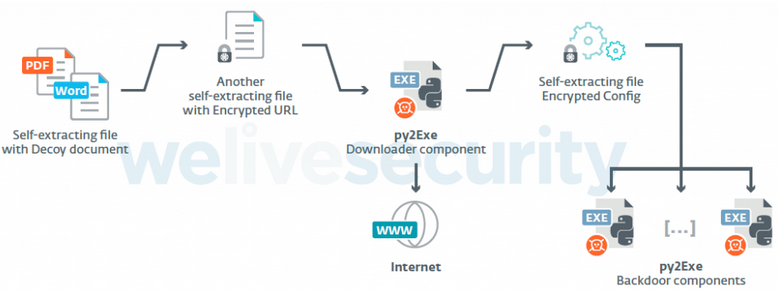
The malware delivered to victims, typically disguised as a Google application, is capable of taking screenshots, logging keystrokes, accessing the system’s clipboard, exfiltrating files and user data from web browsers, collecting information on geolocation and nearby wireless networks, and executing other malicious components fetched from the C&C server. The attackers appear to be particularly interested in backup, database, PGP, document, vector image, and geographic information system (GIS) files.
ESET says the group behind the Machete attacks continues to be active, regularly changing and improving its malware, infrastructure and phishing tactics.
“The Machete group’s operations are stronger than ever, and our investigation has shown that it is able to evolve quite rapidly, sometimes within weeks,” said ESET researcher Matias Porolli.
Related: “Packrat” Threat Group Targets Latin America













