
Globalization and business transformation have created an incredibly complex worldwide supply chain for almost all manufacturers. Hardware ostensibly manufactured in the U.S. will inevitably include components manufactured in many different locations around the world — including nations that are in other circumstances described as ‘adversary states’.
The potential for interference in the supply chain, by foreign governments or criminal gangs, exists. An example of this threat was seen in the October 2018 Bloomberg report, “The Big Hack: How China Used a Tiny Chip to Infiltrate U.S. Companies”. This report claims that a unit of the People’s Liberation Army were involved in an operation that placed tiny spy chips on equipment manufactured in China for US-based Super Micro Computer Inc (SMC).
The report has been largely discredited in security circles, but Bloomberg has refused to remove it. True or fabricated, it is a graphic example of western fears of hardware supply chain attacks. If it were true, every subsequently manufactured SMC computer would have been delivered pre-compromised by the Chinese government.
U.S. manufacturers all attempt to protect their own supply chains. Intel, which developed its own Transparent Supply Chain set of policies, has now gone one step further. “The industry needs an end-to-end framework that can be applied across [the] multi-year life of any platform,” it announced today. “And that is our goal with the Compute Lifecycle Assurance Initiative – to substantially improve transparency and to provide higher levels of assurance that improve integrity, resilience and security during the entire platform lifecycle.”
Intel says it has identified four key lifecycle stages: build, transfer, operate and retire. It commits itself, over the next year, to build on its Transparent Supply Chain tools, to contribute best practices learned from experience, and to collaborate with the ecosystem to develop ways to improve security across the platform lifecycle.
The project is known as the Compute Lifecycle Assurance initiative. Intel gives no details on what this might entail, but says, “In the next 12 to 18 months, we expect to see growing interest from our customers, partners and from government oversight organizations to improve transparency beyond the manufacturing supply chain to also include transportation, provisioning, attestation and in-field updates.”
Earlier this year, Intel produced a whitepaper (PDF) described as a POC “to demonstrate the viability of implementing a blockchain-centric Transparent Supply Chain capability.”
The conclusion includes, “The private blockchain reduces the overall risk by limiting blockchain data access to TSC [Transparent Supply Chain] participants only. An attacker may infer a participant’s identity and associate that identity to an Ethereum account. Nonetheless, these attacks would reveal only account ownership, so that transaction creation can be tracked to a given participant. Data confidentiality is protected by cloud storage access controls and encryption.”
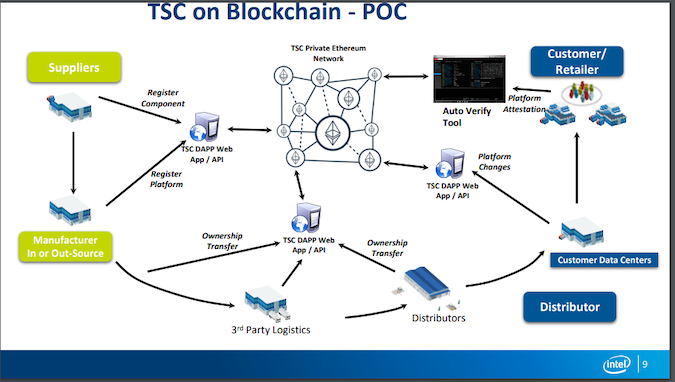
More recently, in September 2019, Intel provided a presentation (PDF) to the National Cybersecurity Center of Excellence (NCCoE). The presentation was delivered by Mark Boucher, described as the chief architect for Compute Lifecycle Assurance at Intel. It clearly shows the application of Intel’s current Transparent Supply Chain principles to a private Ethereum blockchain.
It may be, but it is not specified in today’s statement from Intel, that its view of a generic supply chain security solution is based on learned transparency principles built into a blockchain. Whether it proves to be this or something else, Intel says, “These are early days and we know we can’t do this alone. We invite the broader ecosystem to join us on this journey.”
Related: DUST Identity Emerges From Stealth to Protect Device Supply Chain
Related: Sepio Systems Raises $6.5 Million to Defend Against Rogue Hardware
Related: Intel Asks for Comments on Draft Federal Privacy Law












