Air-gapped cryptocurrency wallets are believed to hold private keys stored in them secure, but an Israeli researcher has demonstrated that attackers can leak the keys from such wallets in a matter of seconds.
In a recently published whitepaper (PDF), Dr. Mordechai Guri from the Ben-Gurion University of the Negev, Israel, explains that managing cryptocurrency wallets offline, in isolated computers, isn’t enough to secure the private keys from theft.
The air-gapped (cold) wallets are software wallets that are managed offline, disconnected from the Web, thus offering increased security compared to hot wallets, which are always online. Because they are physically isolated from the Internet, air-gapped wallets are said to provide the highest level of protection for private keys.
What the research paper reveals, however, is that an attacker able to infiltrate the offline wallet and to infect it with malicious code can then use various air-gap covert channel techniques to exfiltrate the private keys held in the wallet.
To compromise the isolated machine, the attacker can use various techniques that have already proven feasible in the past decade, the researcher argues. The malware can be preinstalled, delivered during the initial installation of the wallet, or pushed through removable media.
Exfiltration methods vary as well, and the whitepaper evaluates several techniques, including physical, electromagnetic, electric, magnetic, acoustic, optical, and thermal ones. Once in the possession of the private keys, the attacker has full control over the cryptocurrency in the compromised wallet.
“This research shows that although cold wallets provide a high degree of isolation, it’s not beyond the capability of motivated attackers to compromise such wallets and steal private keys from them. We demonstrate how a 256-bit private key (e.g., bitcoin’s private keys) can be exfiltrated from an offline, air-gapped wallet […] within a matter of seconds,” Guri notes.
Although kept on offline computers, external media – such as a USB flash drive, an optical disc (CD/DVD), or a memory card (SD card) – is occasionally connected to the air-gapped machine, usually for signing and broadcasting transactions. The use of removable media to infect computers is an attack vector known to be effective and attackers could use it to infiltrate the air-gapped wallet, Guri argues.
Attackers could also modify operating systems and wallets on the download sites to set up attacks. In 2016, the Linux Mint distribution was infected in such an incident, and so was a CCleaner version last year, which proves that such attack vectors are feasible as well. The wallet could also be infected after being downloaded, via the removable drive used to transfer it to the isolated computer.
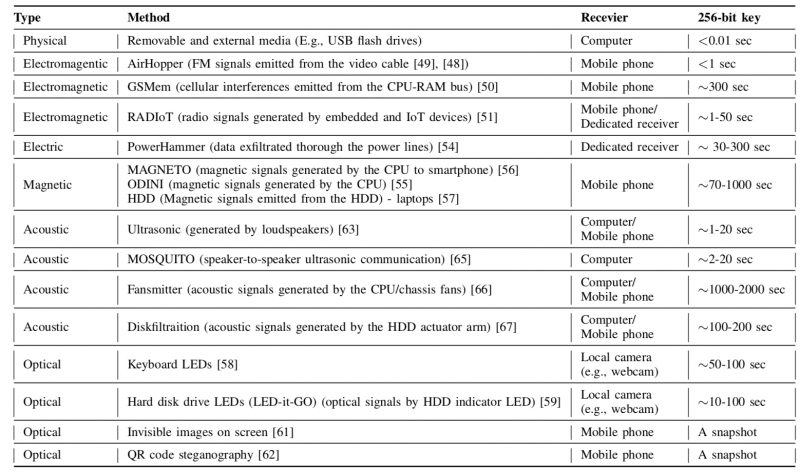
Once the attacker has established a foothold in the air-gapped computer running the wallet, they can use covert channels to exfiltrate the private keys, the researcher says. These channels are classified into seven main categories: physical, electromagnetic, electric, magnetic, acoustic, optical, and thermal. Exfiltration rates can range from less than one second to several minutes.
“In this type of attack vector the wallet keys are transmitted from the offline wallet to a nearby (online) computer, smartphone, webcam, or other type of receiver via these covert channels. The private keys are then sent to the attacker through the Internet,” the whitepaper reads.
Attackers can use physical (removable) media to steal the private keys and send them to the attacker when the drive is inserted into the hot wallet computer.
The AirHopper proof-of-concept (PoC) malware demonstrated several years ago how data can be exfiltrated using electromagnetic signals. Similarly, the GSMem PoC malware showed how data can be sent from the infected machine to nearby mobile phones over GSM frequencies. USBee also uses electromagnetic emissions for data exfiltration from isolated computers.
The recently demonstrated PowerHammer malware can stealthily exfiltrate data from air-gapped computers using power lines. Similarly, the ODINI and MAGNETO malware families use magnetic fields for data exfiltration.
Optical signals can also be leveraged for data exfiltration, either using keyboard LEDs, hard disk drive (HDD) LEDs, or QR stenography. This last method is feasible when a QR code displayed on the isolated computer’s screen is used to validate a transaction. Attackers could covertly project the private keys on the screen along with the QR code of the signed transaction.
The recently detailed MOSQUITO attacks demonstrate how acoustic covert channels can be used for data exfiltration. Computer fans can also be leveraged for similar purposes, the same as the acoustic signals emitted from the HDD.
Several years ago, security researchers also demonstrated that heat emissions and built-in thermal sensors of two computers in close proximity can be used for data transmission.
Countermeasures include the use of anti-virus programs and intrusion detection and prevention systems to keep malware off the air-gapped computer in the first place. Furthermore, it is possible to detect and block some of the covert channels through behavioural analysis, the researcher argues.
“With the emergence of cryptocurrencies and the accompanying need to secure private keys from online threats, it has been suggested that private users manage their cryptocurrency wallets offline in isolated, air-gapped computers. We show that despite the high degree of isolation of cold wallets,
motivated attackers can steal the private keys out of the air-gapped wallets. With the private keys in hand, an attacker virtually owns all of the currency in the wallet,” Guri concludes.














