Anyone who reads the news has probably sensed that breaches and hacking are on the rise. Breaches are constantly in the news whether in the form of sensational attacks against the likes of Ashley Madison or potentially more serious and far-reaching attacks such as those against Anthem Healthcare or the U.S. Office of Personnel Management (OPM).
While these anecdotal examples make headlines, I have been increasingly asked by those inside and outside of the security industry if breaches are truly more common or are they simply being sensationalized in the media and by security vendors.
But a more quantitative analysis confirms the rising tide of breaches and gives us insight into how they are happening. The Privacy Rights Clearinghouse has maintained an easily searchable database of breaches from 2005 to the present, allowing us to easily track the rise and fall of data breaches.
The PRC’s database also breaks down each breach by the industry that was affected and how the breach occurred. While these statistics only reflect data from breaches that have been made public, they provide a consistent way to see the year-over-year trends in breaches.
The table below shows year-over-year trends of breach data from 2013 through August 2015. I picked 2013 as a starting point because it includes the Target breach, which marked the beginning of a series of massive data breaches that continues today.
Additionally, we took advantage of the PRC’s database to analyze how the breach occurred. Known sources of a breach include hacking by external parties, disclosures by insiders, accidental disclosures, loss of physical records, as well as losses from portable devices and stationary devices like servers.
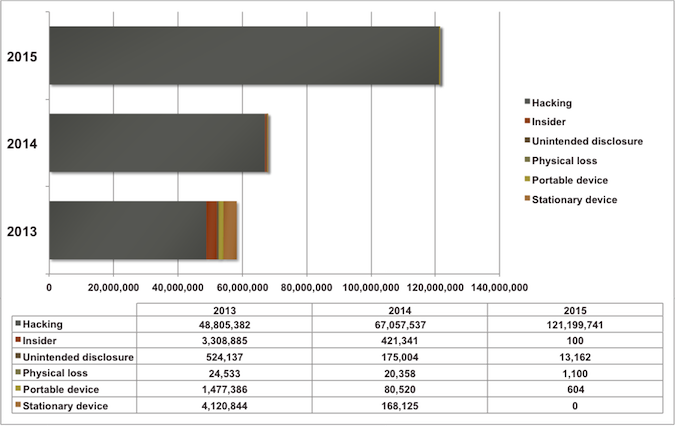
(Source: Privacy Rights Clearinghouse)
The data is clear and powerful. First, based on the number of records compromised, breaches are on the rise. In security circles, 2014 was known colloquially as “the year of the breach.” However, 2015 almost doubled the 2014 tally of breached records, and has done so in the first eight months.
Digging deeper, we can see the source of these breaches. The first thing that stands out is that external hacking is far and away the leading source of breaches, and the percentage is growing. In 2013, external hacking accounted for 83.77 percent of the total records that were compromised. In 2014, that percentage jumped to 98.73 percent. So far in 2015, the percentage continued its rise to 99.99 percent.
This uptick is due to two factors. First, there is a massive increase in the records being compromised by external hacking – from roughly 49 million records in 2013 to 121 million and counting in 2015.
However, there is an accompanying decrease in records lost from all other sources. Breaches tied to insider disclosures, physical loss, and lost or stolen devices have all dropped year over year.
These contrasting trend lines tell us a lot about the state of modern security. Organizations are committing considerable time, talent and money to the task of preventing breaches. The good news is that organizations seem to have successfully cleaned up many mistakes that led to past breaches. The bad news is that even with these efforts, attackers are actually more successful, not less.
To reverse the trend, security teams must adopt new tools and techniques that identify breaches in real time. This means going beyond just malware to identifying all phases of a breach, including the steps of attacks that don’t use malware at all. It requires a unified and real-time understanding of an attack from reconnaissance through to the attempt to gather data for exfiltration.
In my next column, I’ll dive deeper into the techniques that can help you achieve these goals. But in the meantime, we can at least rest assured that we have hard data that shows us where we as an industry are winning and where we are losing.












