Attackers Used Brute Force Attacks Against Internet-Facing Controls Systems at Gas Compressor Stations
In its latest monthly report designed to promote preparedness, information sharing, and collaboration across infrastructure sectors, The Department of Homeland Security’s ICS-CERT publicly revealed information on a series of attacks that targeted gas compressor station operators earlier this year.
According to ICS-CERT, on February 22, 2013, it received a report from a gas compressor station owner about an increase in brute force attempts to access its process control network.
 Based on analysis by ICS-CERT, the attacks were originally traced back to 10 IP addresses. However, after other critical infrastructure asset owners were notified, it was discovered that similar brute force attempts to compromise their networks also occurred. Those new reports yielded 39 additional IP addresses where attacks appeared to originate from.
Based on analysis by ICS-CERT, the attacks were originally traced back to 10 IP addresses. However, after other critical infrastructure asset owners were notified, it was discovered that similar brute force attempts to compromise their networks also occurred. Those new reports yielded 39 additional IP addresses where attacks appeared to originate from.
“The companies reporting this activity operate gas compressor stations across the Midwest and Plains states within the US, although some of the attempts reported were solely against business networks,” ICS-CERT said in its report.
Natural compressor stations are a key component in moving gas through pipelines across the country. After natural gas is extracted, it needs to be processed and transported to where it will be used. As the gas is transported through a pipeline, it needs to be pressurized at various intervals, typically at compressor stations spaced between 40 to 100 miles apart.
The map below shows compressor stations across the country based on data through 2007/2008. Since the US natural gas industry has expanded significantly since 2008, it’s likely that the number of gas compressor stations has jumped.
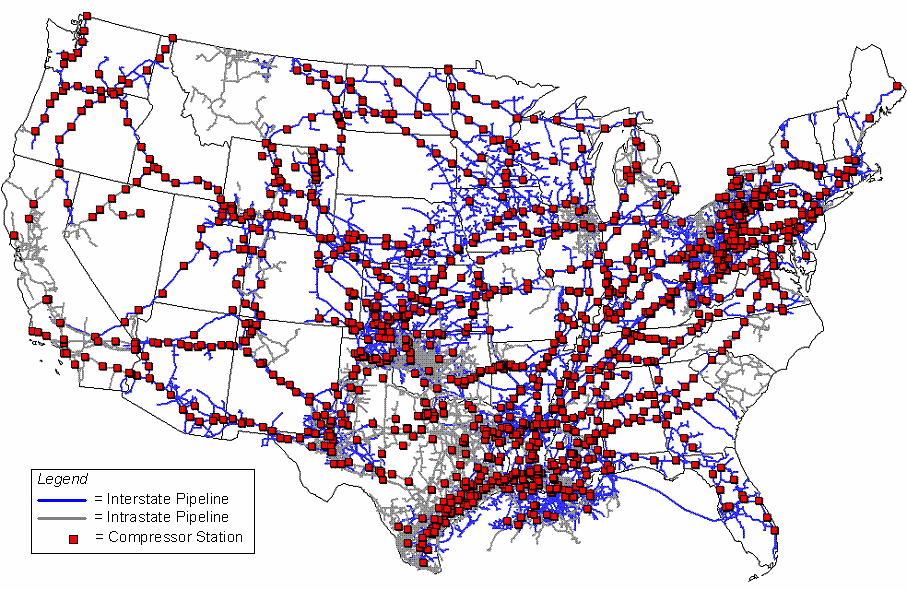
Map of U.S. Natural Gas Pipeline Compressor Stations – Source: Energy Information Administration, Office of Oil & Gas, Natural Gas Division, Natural Gas Transportation Information System.
According to log files from organizations that were hit, the attacks occurred between January 16, 2013, and February 23, 2013. Reports from affected entities began on February 22, 2013, ICS-CERT said.
Fortunately, none of the brute force attempts were successful, and the attacks stopped after March 8, 2013.
Eric Knapp, Director of Strategic Alliances for Wurldtech Security Technologies, was not surprised, but is somewhat disappointed after seeing the ICS-CERT report on brute force attacks facing control systems.
“It means there are still Internet-facing control systems out there to attack,” Knapp said. “There are valid reasons to have a control system remotely accessible, but not by plunking it on the Internet.”
“There are dozens of published recommendations, from ICS-CERT to private firms to blogs, that advise against connecting a control system directly to the Internet,” Knapp said.
“The shocking news is that the internet-facing control systems are ones used by the natural gas industry,” he continued.
According to ICS-CERT, 70% of reported attacks have targeted energy and critical manufacturing organizations.
With the availability of tools like Shodan, these systems can and will be found, and they can and will be attacked, Knapp warned.
Earlier this year, ICS-CERT issued a series of warnings about cyber attacks that had targeted pipeline companies in the natural gas industry.
Disclosure of the attacks against gas compressor stations shows further evidence that attackers are increasingly targeting critical infrastructure systems, or have them on their radar.
Honeypot activity analyzed by Trend Micro and included in the report’s supplemental content, showed industry-specific threats such as control system injection attacks.
“This isn’t corporate malware leaking into the ICS, but rather a clear indication of targeted attacks against critical infrastructure, Knapp said. “If that’s not enough to get asset owners to pull their control systems off the Internet, I don’t know what is.”
According to the ICS-CERT Monitor, in many cases that analysis was inconclusive because of limited or non-existent logging and forensics data from the ICS network. Knapp, who has authored multiple books on industrial control systems cyber security, says this is a point that he feels very strongly about.
“This is an unfortunate side effect of having insufficient cyber security measures in place, because firewalls, intrusion prevention systems, anti-virus, and other tools are excellent sources of relevant, actionable log data,” Knapp said. “Many control system assets can’t effectively produce their own logs — because they lack the capability or because they can’t afford the performance hit that can occur when you enable logging.”
Commercial security tools are an excellent source of surrogate logging, Knapp said, as they are designed to monitor networks, systems, and behavior and have built in logging functions.
“If these systems are in place, crank up the logging to ’11’ and log everything: even authorized, successful connections,” Knapp suggested. “If they’re not in place, or if there are blind spots in your current architecture, add an IDS or similar product to act as a probe.”
“These incidents highlight the need for constant vigilance on the part of industry asset owners and operator,” ICS-CERT said in its report. “The ability to detect anomalous network activity and network intrusions early in an incident greatly increases the chance of a successful mitigation and resolution.”
“Even if you can’t manage the huge amounts of logs yourself, having them available for the ICS-CERT teams will be a huge benefit to them, and ultimately to the whole industry,” Knapp said.
The danger of Internet-facing systems connected to critical infrastructure operations is not new. Billy Rios and Terry McCorkle, researchers for Cylance, an Irvine, California-based security firm, have a history of identifying vulnerable Industrial Control System (ICS) deployments. Last July, ICS-CERT issued a warning based on vulnerabilities discovered by Rios and McCorkle in the Tridium Niagara AX Framework, a popular software platform that integrates various control systems and devices and allows them to be managed over the Internet. Just recently they discovered that Google was using an outdated and “hackable” version of the Niagara framework building management system in one its facilities.
“The documented frequency and intensity of these attacks shows that the world has entered into a new era that requires the energy sector and other critical infrastructure companies to follow US-CERT recommendations and report cyber incidents quickly, “ said Lila Kee, North American Energy Standards Board member and chief product and marketing officer at GlobalSign. “Those corporations should also implement security standards to apply preventative measures to prepare for the ever-increasing number of attacks.”
ICS-CERT said that it responded to more than 200 incidents between Oct. 2012 and May 2013.
Related Podcast: Billy Rios and Terry McCorkle on the State of ICS/SCADA Security













