The threat actor that recently breached Twilio systems also targeted Cloudflare, and a few of the web security company’s employees fell for the phishing messages.
Twilio revealed over the weekend that it became aware of unauthorized access to some of its systems on August 4. An investigation showed that the attackers had tricked some of its employees into providing their credentials, which they then used to access internal systems and obtain customer data.
The threat actor sent phishing text messages to Twilio employees to trick them into entering their credentials on a malicious website. The messages informed recipients of expired passwords and schedule changes, and pointed to domains that included the words ‘Twilio’, ‘Okta’ and ‘SSO’.
The enterprise communications firms noted that the attacker, which it described as well organized and sophisticated, “seemed to have sophisticated abilities to match employee names from sources with their phone numbers.”
Cloudflare revealed on Tuesday that its own employees also received similar text messages, on July 20. The company said more than 100 SMS messages were sent to its employees and their families, pointing them to websites hosted on domains that appeared to belong to Cloudflare.
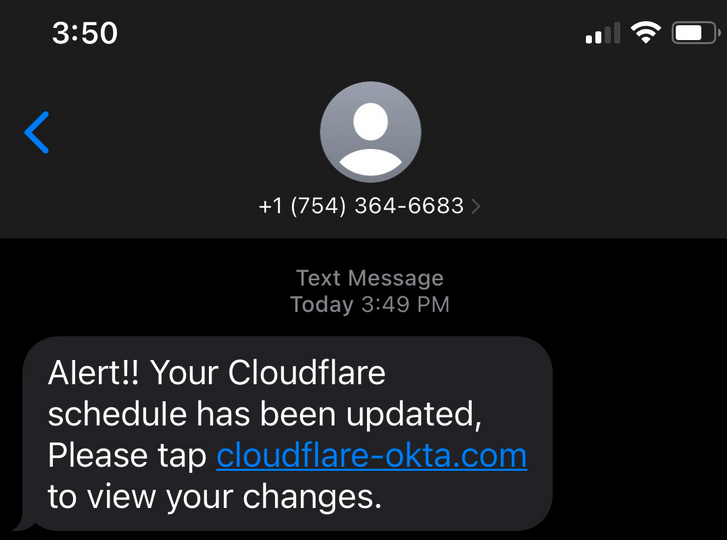
Cloudflare uses Okta identity services and the phishing page looked identical to the legitimate Okta login page. If users entered their username and password, the credentials would be sent to the attacker, who likely attempted to use them immediately to log into Cloudflare systems. This would prompt them for second-factor authentication — typically a code received via SMS or from a dedicated app — and the phishing page would then also prompt the victim to enter a code, which would also be sent to the attacker.
However, in the case of Cloudflare, while three employees did enter their credentials on the phishing site, the company uses physical security keys from vendors such as YubiKey for two-factor authentication, which prevented the attacker from accessing its systems.
According to Cloudflare, the phishing page was also set up to deliver the AnyDesk remote access software, which would give the attacker control over the victim’s computer. The company said none of its employees got to this step and it’s confident that its security systems would have blocked the installation of the software.
Both Cloudflare and Twilio have taken action to disrupt the infrastructure used by the attackers, but they appeared to be persistent, changing mobile carriers and hosting providers in an effort to continue their attack.
Cloudflare monitors the web for potentially malicious domains, but the domain used in this attack was registered only an hour before the first phishing messages went out and the company had yet to notice them.
The attack has yet to be linked to a known threat actor, but Cloudflare has shared some indicators of compromise (IoCs), as well as information on the infrastructure used by the attacker.
Related: Cryptocurrency Services Hit by Data Breach at CRM Company HubSpot
Related: Microsoft, Okta Confirm Data Breaches Involving Compromised Accounts













