The Cloud Atlas threat group has continued conducting cyber espionage operations and its recent attacks have involved a new piece of polymorphic malware.
The activities of Cloud Atlas, which is also tracked as Inception, were brought to light by Kaspersky in 2014. At the time, the cybersecurity firm described Cloud Atlas attacks as the return of Red October, a campaign previously observed targeting government, diplomatic and research organizations.
Cloud Atlas was initially spotted targeting users mainly in Russia, but also in Kazakhstan, Belarus, India and the Czech Republic. In a report published last year, Symantec said it had also seen victims in Ukraine, Moldova, Belgium, Iran, France, the United States, Turkey, Georgia and Bulgaria.
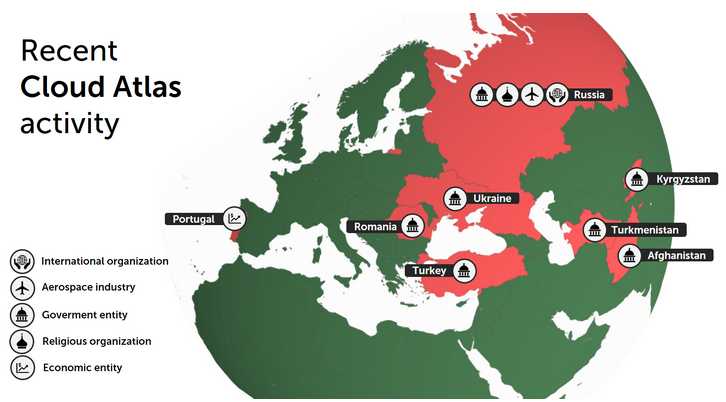
While Russia apparently continues to remain the main target, Kaspersky has recently spotted attacks against entities in Kyrgyzstan, Turkmenistan, Ukraine, Turkey, Romania and Portugal. A majority of the targets appear to be government organizations, but in Russia the hackers also targeted religious organizations, the aerospace industry and an international organization.
In October 2018, the hackers started using a new piece of malware, dubbed PowerShower, that is designed to fetch PowerShell and VBS modules that can be executed on a compromised machine. These modules can allow the attackers to steal documents, collect info about the compromised system, and steal passwords from the device. This piece of malware was previously detailed by researchers at Palo Alto Networks.
Kaspersky now says it has spotted an even newer piece of malware used by Cloud Atlas since April 2019. In attacks involving the new malware, which Kaspersky tracks as VBShower, PowerShower is no longer downloaded and executed in the first stages of the operation.
Instead, a malicious HTML app is downloaded and executed after the initial infection. After some information is collected about the infected device, VBShower is downloaded and executed. VBShower erases evidence of the infection from the system and reaches out to its command and control (C&C) server for commands. The attackers can now instruct VBShower to download PowerShower or another backdoor known to be used by Cloud Atlas.
Interestingly, Kaspersky says, this second backdoor has remained unchanged in the past five years since the company has been tracking Cloud Atlas.
Kaspersky has pointed out that both VBShower and the HTML app are polymorphic, which means they have unique code in each instance. This makes them more difficult to detect by security solutions that rely on indicators of compromise (IoC).
While there is no information on who might be behind the Cloud Atlas attacks, Kaspersky noted in its analysis of the Red October campaign that the hackers appeared to speak Russian. However, it could not say whether a nation state was behind the attacks.
Related: New APT10 Activity Detected in Southeast Asia
Related: Russia-Linked Hackers Hijack Infrastructure of Iranian Threat Group














