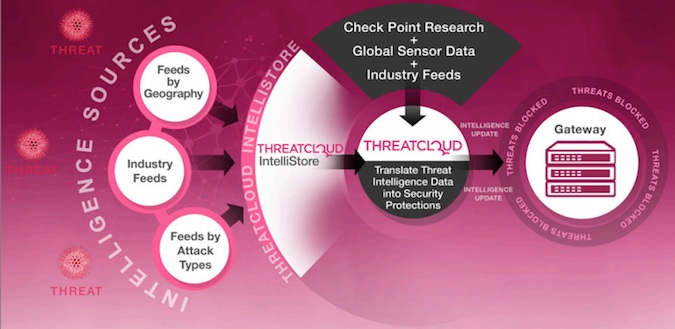
Internet security firm Check Point Software Technologies has launched a new intelligence marketplace that enables organizations to purchase intelligence feeds to help them defend against cyberattacks using their Check Point security gateways.
Dubbed ThreatCloud IntelliStore, the intelligence marketplace builds on Check Point’s ThreatCloud intelligence infrastructure, which delivers threat data from a global network of threat sensors.
“Organizations need customizable threat intelligence that can be immediately used within their network environments to prevent cyberattacks from occurring,” Check Point explained. “Today however, sources for threat intelligence are fragmented, and offered by numerous vendors for specific countries and verticals.”
Designed to offer actionable threat intelligence to customers using Software-defined Protection, ThreatCloud IntelliStore launched with several intelligence partners including:
• iSIGHT Partners
• CrowdStrike
• Internet Identity (IID)
• NetClean
• PhishLabs
• SenseCy
• ThreatGRID
More third-party intelligence partners are expected to follow.
Customers can select and customize intelligence feeds from a variety of sources according to their organizations’ needs in specific geographies, vertical industries, and protection types, Check Point said.
“We are extremely excited to launch the ThreatCloud IntelliStore. It’s a groundbreaking collaboration that seeks to eliminate the current fragmentation of the threat intelligence market and is the first platform to automatically aggregate threat intelligence feeds for real prevention,” said Dorit Dor, vice president of products at Check Point.
“The unfortunate reality of today’s advanced cybercrime attacks is that they are always evolving faster than organizations can keep up with them,” said Rod Rasmussen, president and chief technology officer at IID.
“By bringing together the best sources for threat intelligence, ThreatCloud IntelliStore provides organizations the flexibility to select the most appropriate data feeds through a singular system,” said Dov Yoran, chief executive officer and co-founder at ThreatGRID. “This data in turn is fed into ThreatCloud and provides the protections organizations need across all of their security gateways.”
For More information on ThreatCloud IntelliStore is available online.
















