Cyber attacks against supervisory control and data acquisition (SCADA) systems doubled in 2014, according to Dell’s annual threat report, released Monday.
Dell SonicWALL saw global SCADA attacks increase against its customer base from 91,676 in January 2012 to 163,228 in January 2013, and 675,186 in January 2014.
“Attacks against SCADA systems are on the rise, and tend to be political in nature as they target operational capabilities within power plants, factories, and refineries,” the tech firm said.
Whereas the motive behind data-focused attacks is typically financial, SCADA attacks tend to be political in nature, since they target operational capabilities within power plants, factories, and refineries, rather than credit card information, Dell said.
Buffer overflow vulnerabilities were the primary point of attack against SCADA systems, which control remote equipment and collect data on equipment performance, accounting for 25% of the attacks witnessed by Dell.
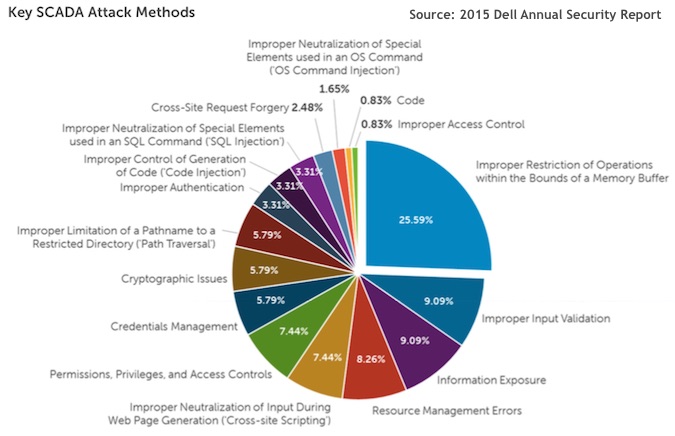
The majority of these attacks targeted Finland, the United Kingdom, and the United States, Dell said, noting that the reason is likely the fact that SCADA systems are more common in these regions and more likely to be connected to the Internet.
In 2014, Dell said that it saw 202,322 SCADA attacks in Finland, 69,656 in the UK, and 51,258 in the US.
Dell’s threat report leverages research from the company’s Global Response Intelligence Defense (GRID) network and telemetry data from Dell SonicWALL network traffic to identify emerging cyber threats.
“Since companies are only required to report data breaches that involve personal or payment information, SCADA attacks often go unreported,” said Patrick Sweeney, executive director, Dell Security. “This lack of information sharing combined with an aging industrial machinery infrastructure presents huge security challenges that will to continue to grow in the coming months and years.”
“Because companies are only required to report data breaches that involve personal or payment information, SCADA attacks often go unreported,” Dell said in its report. “As a result, other industrial companies within the space might not even know a SCADA threat exists until they are targeted themselves.”
A recent report published by the Industrial Control Systems Cyber Emergency Response Team (ICS-CERT) showed that while ICS vendors have been targeted by various types of malicious actors, over half of the attacks reported to the agency in 2014 involved advanced persistent threats (APTs).
ICS-CERT has issued alerts for muptiple campaigns over the last year, including one which focused on the use of the Havex RAT in attacks aimed at ICS, and the second related to BlackEnergy attacks exploiting vulnerabilities in products from GE, Advantech/Broadwin, and Siemens.
“Lack of information sharing combined with the vulnerability of industrial machinery due to its advanced age means that we can likely expect more SCADA attacks to occur in the coming months and years,” Dell’s report concluded.
Organizations such as the Industrial Control System Information Sharing and Analysis Center (ICS-ISAC) and Electricity Sector Information Sharing and Analysis Center (ES-ISAC) allow for reporting and sharing information about SCADA attacks and can help the industrial community become aware of emerging threats.
The report also highlighted a surge in point-of-sale (POS) malware and increased malware traffic within encrypted (https) web protocols.
The full report is available online in PDF format.
Releated Event: Learn More at the 2015 ICS Cyber Security Conference
















