Details Emerge on “Duqu” a Possible Precursor to the Next Stuxnet
Symantec researchers shared details today on what they say could be the precursor to a future Stuxnet-like attack. Symantec said they were tipped off about the threat on October 13th by a research lab “with strong international connections.”
The threat has been named “Duqu” [dyü-kyü], simply because it creates files with the file name prefix “~DQ”.
According to Symantec, early samples of the malware were seen in Europe, with one revealing a compilation date as late as October 17, 2011 that Symantec is currently analyzing. Initial findings compared Duqu to Stuxnet, with parts of it nearly identical to Stuxnet—but it appears to serve a different purpose and does NOT contain code that would target industrial control systems.
Instead, Duqu’s primary purpose appears to be a remote access Trojan or RAT, an acronym that stands for Remote Access Tool that can provide a way for attackers to install other forms of malware that can record keystrokes and collect other system information.
“The threat was written by the same authors (or those that have access to the Stuxnet source code) and appears to have been created since the last Stuxnet file was recovered,” notes the Symantec Blog post. “Duqu’s purpose is to gather intelligence data and assets from entities, such as industrial control system manufacturers, in order to more easily conduct a future attack against another third party. The attackers are looking for information such as design documents that could help them mount a future attack on an industrial control facility,”
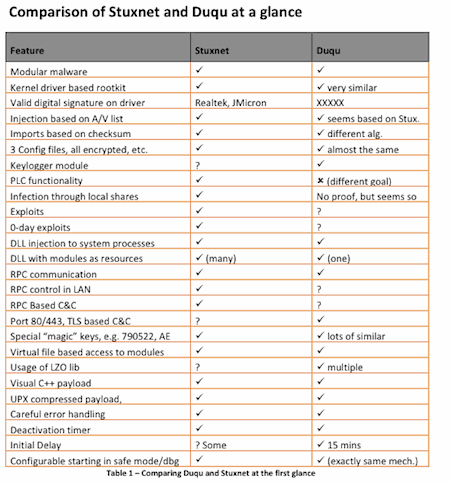 Interestingly, early variants don’t appear to self-replicate. “Our telemetry shows the threat was highly targeted toward a limited number of organizations for their specific assets,” Symantec added. “However, it’s possible that other attacks are being conducted against other organizations in a similar manner with currently undetected variants.”
Interestingly, early variants don’t appear to self-replicate. “Our telemetry shows the threat was highly targeted toward a limited number of organizations for their specific assets,” Symantec added. “However, it’s possible that other attacks are being conducted against other organizations in a similar manner with currently undetected variants.”
Symantec’s discoveries revealed that the attackers were searching for assets that could be used in a future attack.
“In one case, the attackers did not appear to successfully exfiltrate any sensitive data, but details are not available in all cases. Two variants were recovered, and in reviewing our archive of submissions, the first recording of one of the binaries was on September 1, 2011. However, based on file compile times, attacks using these variants may have been conducted as early as December 2010.”
Symantec’s Security Response Team said that the command-and-control (C&C) server, which uses a custom C&C protocol, primarily for downloading or uploading what appear to be JPG files, was still operational at the time of publishing. (Update: According to McAfee, the Command and Control server for samples it analyzed, was based in India and has been blacklisted by its ISP and is no longer functioning.)
While Duqu shares man similarities and code with Stuxnet, Symantec noted that payload is completely different. “Instead of a payload designed to sabotage an industrial control system, the payload has been replaced with general remote access capabilities. The creators of Duqu had access to the source code of Stuxnet, not just the Stuxnet binaries.”
Key points from Symantec’s Security Response Team:
• Executables using the Stuxnet source code have been discovered. They appear to have been developed since the last Stuxnet file was recovered.
• The executables are designed to capture information such as keystrokes and system information.
• Current analysis shows no code related to industrial control systems, exploits, or self-replication.
• The executables have been found in a limited number of organizations, including those involved in the manufacturing of industrial control systems.
• The exfiltrated data may be used to enable a future Stuxnet-like attack.
Finally, the threat is configured to be a short term infiltration tool and it set to run for 36 days. After 36 days, the threat will automatically remove itself from the system. However, other malware installed after attackers gain access by using duqu could still reside in enterprise networks.
While the analysis shows many similarities in code and design to Stuxnet, the attack targets and usage could be more along the lines of what McAfee Identified in what it called “Operation Shady RAT” earlier this year. While both Duqu and Stuxnet may share some common code, Symantec acknowledged that this is an entirely different animal, and really doesn’t appear to do anything similar to what Stuxnet was designed to to do. Stuxnet targeted five organizations in Iran, spying on attempting to destrupt their uranium enrichment process by spinning centrifuges into destruction. From what Symantec has shared, Duqu appears to be an advanced trojan designed to penetrate enterprise systems with the eventual goal of implanting other data stealing malware, but other than some code similarities, not very similar to Stuxnet in attack use.
This is in the early stages and much more should be learned over time.
Deatiled findings are available in a white paper from Symantec here. More on McAfee’s Analysis can be found here.
Related Reading: Getting Your Hands Dirty in the Fight on Modern Malware Part 1 and Part 2
















