Integrated Solution Provides Visibility and Protection Across IT and OT Networks
Israeli industrial cybersecurity firm SCADAfence has teamed up with network traffic visibility platform provider Gigamon (NYSE: GIMO) to offer a joint solution that provides visibility and protection for IT and operation technology (OT) networks.
Through Gigamon’s ecosystem partner program, SCADAfence’s network monitoring solution is integrated with Gigamon’s GigaSECURE platform to provide IT and OT security staff with a detailed view of their industrial network, as well as threat detection capabilities, the companies explained.
Most IT security and monitoring solutions currently available were not designed for Operational Technology (OT) environments, often leaving these networks unprotected and unmonitored.
“In a sense, industrial control environments are like an old man—fragile, slow-paced, and not overly adept at dealing with change,” Gigamon’s Johnnie Konstantas explained in a recent SecurityWeek column. “Traffic in these environments is exceedingly low compared to a regular IT network and, for the most part, the technology has been in place for 10+ years and was not developed with Internet connectivity in mind, let alone cybersecurity.”
However, as more industrial control systems are being connected to the Internet to take advantage of features such as remote management, improved efficiency, and lowered costs, there is a risk that comes along with these benefits.
The joint solution from SCADAfenence and Gigamon was designed to help mitigate risks in industrial environments, such as operational downtime, product manipulation and theft of intellectual property.
“The joint solution provides industrial asset and network visibility and alerts manufacturers to abnormal activities from malicious malware to non-malicious human error, allowing them to quickly respond with increased accuracy,” Yoni Shohet, Co-founder and CEO of SCADAfence, said in a statement.
How it works
The joint solution leverages Gigamon’s capability to provide visibility of network traffic from across the ICS/SCADA environment, ensuring continuous traffic monitoring.
“The network traffic is passively gathered by Gigamon, deduplicated, aggregated into scalable traffic streams and then passed to SCADAfence’s continuous monitoring solution which analyzes the internal communications, including industrial protocols deep packet inspection (DPI),” SCADAfence explained.
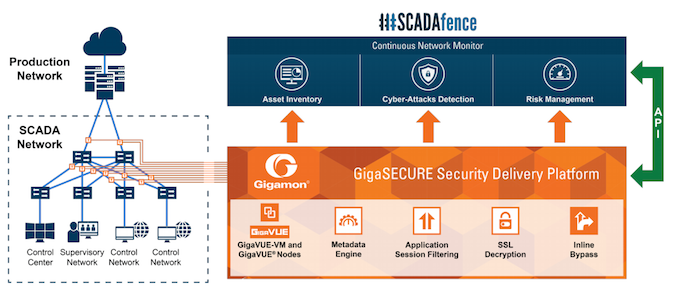
Deployed together and connected via API, the SCADAfence and GigaSECURE platforms can help detect cyber-attacks, monitor and detect non-malicious operational threats such as misconfigurations and human errors, and provide industrial protocol context-aware, network visibility including asset discovery, asset inventory and network topology.
Earlier this year, SCADAfence announced a partnership with network security giant Check Point Software to offer integrated cyber protection for critical infrastructure and industrial control organizations.
Related: Learn More at SecurityWeek’s ICS Cyber Security Conference















