“IXESHE” Attack Campaign Leveraged “Weaponized” PDFs Targeting Zero-day Exploits Dating Back to 2009.
Trend Micro has revealed details on a series of attacks that tried to stay under the radar by using machines inside compromised networks as command and control (C&Cs) servers.
In a report obtained by SecurityWeek that is expected to soon be released to the public, Trend Micro pulled the covers off an APT known as IXESHE. Known for targeting East Asian governments, electronic manufacturers and a German telecommunications company, the IXESHE (pronounced I-sushi) campaign used targeted emails with malicious “weaponized” PDF attachments to infect computers.
One of the most interesting parts of the campaign however, is that the IXESHE attackers almost always make use of compromised servers for command and control purposes.
“In some cases, the compromised servers are hosted on target organizations’ networks after successful infiltration so the attackers can increase their control of the victims’ infrastructure,” according to the report. “Using this approach, the attackers amassed at least 60 C&C servers over time. This technique also allows the attackers to cover their tracks, as having the C&C server in the victims’ corporate networks means very little C&C traffic leaves them. The attackers’ deliberate use of compromised machines and dynamic Domain Name System (DNS) services allows them to hide traces of their presence by confusing their activities with data belonging to legitimate individuals.”
In an April interview, Tom Kellermann, vice president of cybersecurity at Trend Micro, told SecurityWeek he had seen hacker crews using compromised servers for C&C operations going back several months. Today, he reiterated that the technique is being adopted by elite hacker crews, and rated the sophistication of the IXESHE campaign as a 9.3 out of 10.
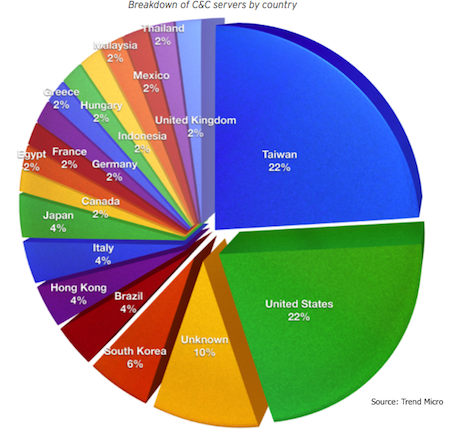
The majority of the C&Cs used by the IXESHE attackers (22 percent) were based in the United States and Taiwan (also 22 percent). This is, however, not a true indication of geographical attribution of the attacks, the report explained, in part because not all of them are active and many of them are compromised machines. At least 11 of the C&C servers were hosted on compromised machines belonging to an East Asian government.
“Most of the malware samples directly accessed an IP address as a C&C server,” according to the report. “Connections to domains did exist in some cases. The domains were usually registered using free dynamic DNS service providers or compromised websites. Overall, this strategy was part of the attackers’ modus operandi. By choosing compromised machines to act as C&C servers, fewer clues were left for investigators to follow in an attempt to find out who is behind the attacks compared with those using bulletproof hosting services and registered domain names. To conduct research on these servers, investigators need to differentiate between information related to malicious and legitimate use.”
In most cases, the IXESHE attacks involved Adobe Acrobat, Reader and Flash Player exploits, including: CVE-2009-0927, CVE-2011-0609 and CVE-2011-0611, according to the report. The campaign has been successfully executing targeted attacks since 2009. The attackers kept track of their operations by embedding a “campaign tag” in the malware that appears to describe when each attack was launched and in some cases the nature of its target. Trend Micro found more than 40 of these campaign tags.
Besides the use of infected computers on compromised networks as command and control servers, the attackers also utilized the proxy tool HTran to mask their true location.
According to Trend Micro’s researchers, the IXESHE malware enabled attackers to easily take over and maintain control over an infected system and execute the following functions:
• List all services, processes, and drives
• Terminate processes and services
• Download and upload files
• Start processes and services
• Get victims’ user names
• Get a machine’s name and domain name
• Download and execute arbitrary files
• Cause a system to pause or sleep for a specified number of minutes
• Spawn a remote shell
• List all current files and directories
“While their identities remain unknown, the attackers behind the IXESHE campaign demonstrated that they were both determined and capable,” according to the report. “While the malware used in the attacks were not very complicated by nature, these proved very effective.”
Related: Attackers Place Command and Control Servers Inside Enterprise Walls
Mike Lennon contributed to this report.














