Security researchers from BAE Systems and G-Data recently shared research on a cyber-espionage toolkit called Snake (also referred to as Turla or Uroburos) that was used in attacks against targets in the Ukraine, Lithuania, Great Britain, the United States and other nations.
According to BAE Systems, the malware is the work of a technically sophisticated and well-organized group. However, BAE did not say exactly who is behind the campaign or who might be paying them despite evidence linking these tools to previous breaches connected to Russian threat actors.
While BAE determined there was a connection between the authors of Snake and Agent.BTZ, Kaspersky Lab has dug a little deeper and found some interesting pieces.
As background, Agent.btz was highlighted by the media in late 2008 after it was found being used it was used to infect US military networks.
According to Wikipedia, the 2008 cyberattack on the United States was the “worst breach of U.S. military computers in history” and led to the creation of the United States Cyber Command.
Some reports say that it took the Pentagon roughly 14 months to fully eradicate Agent.BTZ from military networks.
Kaspersky Lab said that it first became aware of the cyber espionage campaign in March 2013, when the company’s experts were investigating an incident involving a highly sophisticated rootkit.
Originally known as the “Sun rootkit”, based on a filename used as a virtual file system “sunstore.dmp”, it is also accessible as “.Sundrive1” and “.Sundrive2”. The “Sun rootkit” and Snake are in fact one and the same, Kaspersky says.
Kaspersky Lab experts say the Agent.btz worm has “served as an inspiration” for the creation of a range of sophisticated cyber weapons, including Red October, Turla and Flame/Gauss:
· Red October developers clearly knew about Agent.btz’s functionality as their USB Stealer module (created in 2010-2011) searches for the worm’s data containers (“mssysmgr.ocx” and “thumb.dd” files) which hold information about infected systems and activity logs, and then steal it from the connected USB drives.
· Turla uses the same file names for its logs (“mswmpdat.tlb”, “winview.ocx” and “wmcache.nld”) whilst stored in the infected system, and the same XOR key for encrypting its log files as Agent.btz.
· Flame/Gauss use similar naming conventions such as “*.ocx” files and “thumb*.db”. Also, they use the USB drive as a container for stolen data.
Do these examples mean that there is a direct link between developers of these cyber espionage tools?
“It is not possible to draw such a conclusion based on these facts alone,” said Aleks Gostev, Chief Security Expert at Kaspersky Lab. “The information used by developers was publicly known at the time of Red October and Flame/Gauss’ creation.”
“It is no secret that Agent.btz used “thumb.dd” as a container file to collect information from infected systems,” he said. “In addition, the XOR key used by the developers of Turla and Agent.btz to encrypt their log files was also published in 2008.”
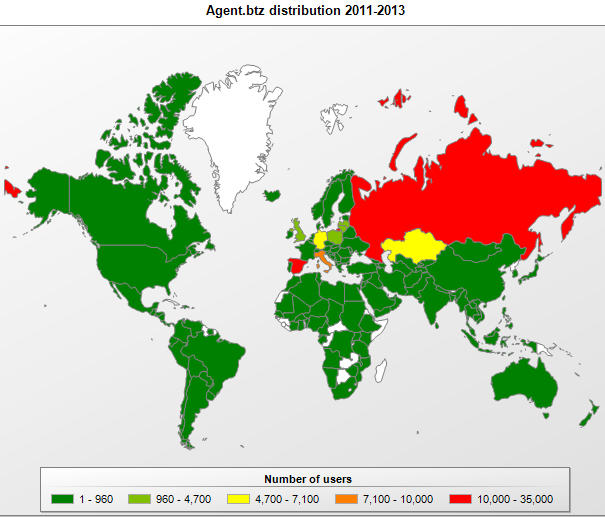
According to data collected by Kaspersky Lab, Agent.btz was discovered on 13,800 systems across 100 countries in 2013.
More details are available in a blog post to Kaspersky Lab’s Securelist.
Sergey Shevchenko also published an interesting report on the modus operandi of Agent.btz in November 2008.
















