As part of Google’s Safe Browsing initiative that launched five years ago, the search giant had the goal of protecting Internet users from malicious content of various types, including phishing sites, malware, and poisoned search results.
While most of the major security vendors produce their own threat reports on an ongoing basis, Google hasn’t always shared the numbers behind what its platform sees and blocks on an ongoing basis.
Today, however, Google has shared some interesting Web threat statistics, and while the information was not published as an official “threat report”, the company has provided some great insight into the growth of malicious activity across the Web.
Through its massive infrastructrure and reach, Google has developed a platform that automatically detects malicious across the Internet, and distributes warnings to end users and even network administrators.
Through built-in protection for Chrome, Firefox, and Safari, Google said it protects approximately 600 million Internet users and issues several million warnings each day to those users.
Other key metrics and tidbits shared by Google include:
• The company provides a free and public Safe Browsing API that allows other organizations to keep their users safe by using the data Google has compiled.
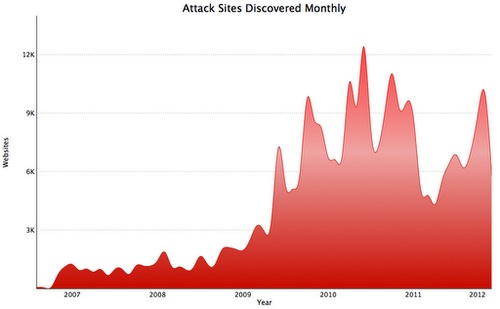
• Google said it discovers about 9,500 new malicious websites every day – These sites could be either innocent sites that have been compromised by cybercriminals, or purpose-built sites designed for malware distribution or phishing.
• Approximately 12-14 million Google Search queries per day show warnings in order to caution users from going to sites that may be compromised.
• Google provides malware warnings for about 300,000 downloads per day through its Chrome download protection service.
• Google also sends thousands of notifications daily to Internet Service Providers (ISPs) & CERTs to help them keep their networks clean.
While Google says it still sees some of the same techniques it did over five years ago, phishing attacks are also getting more creative, as well as faster and more diverse. In particular, Google noted that many phishing URLs remain online for less than an hour in an attempt to evade detection. A recent report from the Anti-Phishing Working Group (APWG) also showed plunging phishing times.
“The uptime of a phishing attack is an important factor in determining how damaging phishing attacks are and also can measure the success — or failure — of mitigation efforts,” noted Ram Mohan, EVP and CTO at Afilias, in a recent column analyzing a recent APWG Phishing report. “The longer a phishing attack remains active (“up”), the more severe the damage the victims and target institutions are likely to incur. Compared to an average up time of 73 hours in the second half of 2010, the average uptime for an attack in the same period a year later was 11 hours and 43 minutes.”
Additionally, Google along with most other security vendors, says that spear phishing (targeted) attacks have become increasingly common. When a legitimate website is compromised, it’s often modified to load content from a malicious third party site, or to redirect users to an attack site which often delivers “Drive by downloads” to visitors.
“Google is providing a good base-line for security and are definitely providing value to the Internet ecosystem,” Patrik Runald, Director of Websense Security Labs told SecurityWeek. “Their statistics for phishing and how long a phishing site stays up is in line with what Websense is seeing. The same goes for compromised sites which make up the majority of malicious sites we identify. We see a pattern of many compromised sites leading to a few number of malicious sites.”
“Our adversaries are highly motivated by making money from unsuspecting victims, and at great cost to everyone involved,” Niels Provos, a member of Google’s Security Team, wrote in a blog post. “Our tangible impact in making the web more secure and our ability to directly protect users from harm has been a great source of motivation for everyone on the Safe Browsing team. We are also happy that our free data feed has become the de facto base of comparison for academic research in this space.”
Action Items – What can you do?
Website owners can register their website with Google Webmaster Tools in order to be alerted if Google finds suspicious code on their website.
Internet Service Providers (ISPs) & CERTs can sign up to receive frequent alerts from Google in order to help them keep their networks clean. If you’re a network administrator and haven’t yet registered your AS, you can do so here.
“Phishing is here to stay,” Mohan concludes. “While techniques for fighting these criminals are necessarily evolving along with the criminal activity itself, the lack of aggressive takedown programs and effective metrics and service levels has created a situation where criminals can depend upon cheap and poorly administered TLDs to wreak havoc on unsuspecting Internet users. As in all things digital, it pays to be careful before you click!”















