DHS Releases Trove of Documents Related to Wrong “Aurora” in Response to Freedom of Information Act (FOIA) Request
The U.S. Department of Homeland Security (DHS) has mistakenly released hundreds of documents, some of which contain sensitive information and potentially vulnerable critical infrastructure points across the United States, in response to a recent Freedom of Information Act (FOIA) request about a cyber-security attack.
The Operation Aurora attack was publicized in 2010 and impacted Google and a number of other high-profile companies. However, DHS responded to the request by releasing more than 800 pages of documents related to the ‘Aurora’ experiment conducted several years ago at the Idaho National Laboratory, where researchers demonstrated a way to damage a generator via a cyber-attack.
The documents are posted on MuckRock.com. The information request was made May 17. On July 3, the agency replied with the mistaken documents.
When contacted by SecurityWeek, the DHS declined to comment about the situation.
Of the documents released by the DHS, none were related to the Operation Aurora cyber attack as requested.
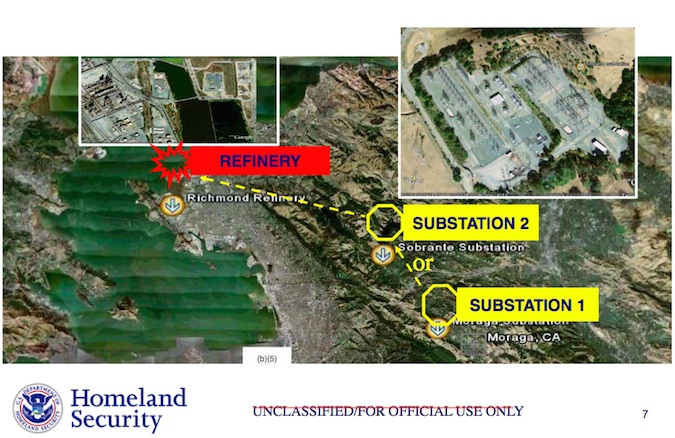
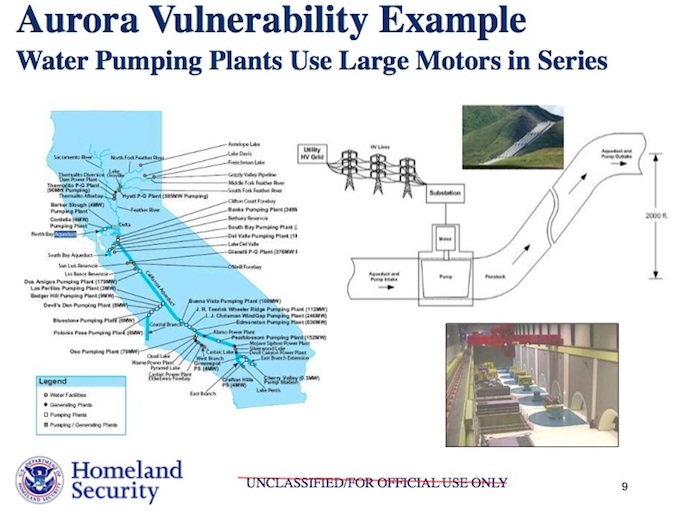
According to a blog post by Dale Peterson, founder of Digital Bond, many of the 840 pages are comprised of old weekly reports from the DHS’ Control System Security Program (CSSP) from 2007. Other pages that were released included information about possible examples of facilities that could be vulnerable to attack, such as water plants and gas pipelines (pages 70 and 71). Other pages were redacted due to their sensitivity.
“The real beauty of the Aurora demonstration was it clearly showed that a cyber attack could affect a physical process,” blogged Peterson. “The specific vulnerability they chose to achieve this, while not unimportant, was not the main point to take from Aurora. It was an effective and dramatic demonstration.”
In the Aurora experiment, the researchers demonstrated the dangers of a malicious attacker disconnecting and reconnecting a generator to the electric grid out of phase. The exact extent of the danger utilities face and whether or not enough has been done to mitigate the issue has been the subject of some debate. Joe Weiss of Applied Control Solutions said he believes the issue has been downplayed.
“What you have is a physical problem that cyber is able to exploit,” explained Weiss, in an interview with SecurityWeek. “This physical problem affects every single substation everywhere. Period.”
The North American Electric Reliability Corporation (NERC) did not respond to a request for comment today by SecurityWeek.
“To me the only thing that is still a mystery about Aurora is the precise mechanics of what commands were sent to which device in order to cause the destruction of the generator,” said Andrew Ginter, vice president of industrial security at Waterfall Security Solutions. “The basic principles have been out in the public domain for a very long time.”
“The basic principle,” he said, “is that you disconnect the generator from the grid, and within milliseconds it starts speeding up because it has no load anymore….If you time it right and you reconnect it to the grid when it’s out of sync, now there’s enormous force on the generator to bring it back into sync.”
According to information on the MuckRock site, the person who filed the FOIA request received a “no-responsive documents” response from the FBI in reaction to the FOIA request, while the National Security Agency notified him that his request for information is being processed.
The incident the FOIA request was actually about, the Operation Aurora cyber attack, impacted dozens of organizations, including Juniper Networks and aerospace and defense company Northrop Grumman, and is believed by many to have been perpetrated by hackers from China. The Chinese government denied any involvement when the attack was made public.
Related: ICS Cyber Security Conference
















