APT1: Mandiant Exposes One of China’s Most Active Cyber Espionage Units
In a fascinating, unprecedented, and statistics-packed report, security firm Mandiant made direct allegations and exposed a multi-year, massive cyber espionage campaign that they say with confidence is the work of China, more specifically, a unit of China’s People’s Liberation Army (PLA).
Mandiant has named the attack group “APT1”, what is likely a government-sponsored group that is one of the most persistent of China’s cyber threat actors, and considered to be one of the most prolific in terms of quantity of information it has stolen.
 To further its claims that there are actual individuals behind the keyboard, Mandiant also revealed three “personas” that they say are associated with APT1 attacks.
To further its claims that there are actual individuals behind the keyboard, Mandiant also revealed three “personas” that they say are associated with APT1 attacks.
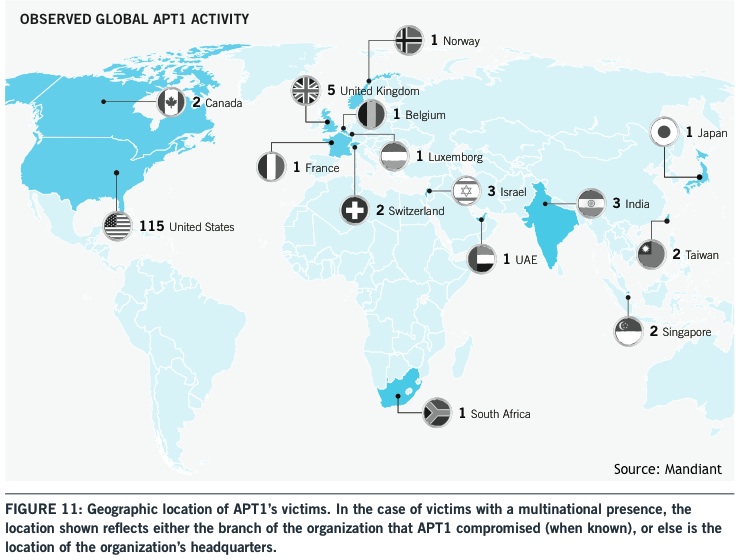
According to Mandiant’s investigations, APT1 has taken hundreds of terabytes of data from at least 141 organizations across many industries going as far back as 2006, but representing just a small fraction of the overall cyber espionage that APT1 has conducted.
It was the massive scale and impact of APT1’s operations that compelled Mandiant to write and publically release the report.
Historically, Mandiant has said there was no way to determine the extent of China’s involvement in many attacks, but the firm now says it has enough evidence to confidently say that “the groups conducting these activities are based primarily in China and that the Chinese Government is aware of them.”
While many firms steer away from publicly calling out China as a culprit in cyber attacks, Mandiant is taking a stance and boldly pointing fingers at China, and bringing many statistics and research to back its case.
“It is time to acknowledge the threat is originating in China, and we wanted to do our part to arm and prepare security professionals to combat that threat effectively.”
“The issue of attribution has always been a missing link in publicly understanding the landscape of APT cyber espionage. Without establishing a solid connection to China, there will always be room for observers to dismiss APT actions as uncoordinated, solely criminal in nature, or peripheral to larger national security and global economic concerns.”
Mandiant believes APT1 is the 2nd Bureau of the People’s Liberation Army (PLA) General staff Department’s (GSD) 3rd Department, commonly known by its Military unit Cover Designator (MUCD) as Unit 61398.
The security firm estimates that Unit 61398 is staffed by hundreds, or even thousands of people, and that China Telecom provided special fiber optic communications infrastructure for the unit. Additionally, Mandiant said that it conservatively estimates that APT1’s current attack infrastructure includes over 1,000 servers across dozens of countries.
Mandiant said that it was able to confirm 937 command and control servers running on 849 distinct IP addresses and has confirmed 2,551 domain names attributed to APT1 in the last several years.
“Our research and observations indicate that the Communist Party of China is tasking the Chinese People’s Liberation Army (PLA) to commit systematic cyber espionage and data theft against organizations around the world,” the report alleged.
When APT1 launches an attack against a target, it’s typically not a one shot deal or a quick hit. In fact, according to Mandiant’s research, APT1 maintained access to victim networks for an average of 356 days. The longest time period APT1 maintained access to a victim’s network was four years and ten months.
In one operation, Mandiant witnessed APT1 steal 6.5 terabytes of compressed data from a single organization over a ten-month time period. APT1’s targets include organizations across a broad range of industries, mainly in the United States and other English-speaking countries.
In over 97% of the 1,905 times Mandiant witnessed APT1 intruders connecting to their attack infrastructure, APT1 used IP addresses registered in Shanghai and systems set to use the Simplified Chinese language.
“Once the group establishes access to a victim’s network, they continue to access it periodically over several months or years to steal large volumes of valuable intellectual property, including technology blueprints, proprietary manufacturing processes, test results, business plans, pricing documents, partnership agreements, emails and contact lists from victim organizations’ leadership,” the report explained.
Hacking For Economic Gain and Advantage
Mandiant’s investigations show that APT1 has targeted at least four of the seven strategic emerging industries that China identified in its 12th Five Year Plan, and warns that any industry related to China’s strategic priorities are potential attack targets.
Mandiant highlighted an attack in 2008 that compromised the network of a company involved in a wholesale industry. According to Mandiant, over the next two and a half years, APT1 used various tools to steal an unknown number of files from the victim and repeatedly accessed the email accounts of several executives, including the conpany’s CEO and General Counsel. During this same time period, news organizations reported that China had successfully negotiated a double-digit decrease in price per unit with the victim organization for one of its major commodities, Mandiant said.
China continues to deny claims
As usual, China denied that its Army had supported any kind of hacking activity.
“Not only are reports that China’s army has been involved in hacking unprofessional, they do not fit with the facts,” China’s defense ministry said in a statement to AFP. “Hacking attacks are a global problem. Like other countries, China also faces the threat of hacking attacks, and is one of the main countries falling victim to hacking attacks.”
China’s foreign ministry also reminded that China was itself a major victim, saying that most overseas cyberattacks against it originate in the US.
Recent attacks against several high-profile US media outlets, Including The New York Times, The Wall Street Journal, The Washington Post, and Bloomberg, as well as against Twitter and others, have further raised concerns over Chinese hackers.
In late January, The New York Times said hackers stole corporate passwords and targeted the computers of 53 employees including former Beijing bureau chief Jim Yardley, who is now the South Asia bureau chief at the Times based in India, after the newspaper published a report on the vast wealth amassed by Premier Wen Jiabao’s family.
Mandiant was hired to investigate the attacks against The Times.
While Mandiant hopes its efforts will lead to increased understanding and coordinated action in countering targeted cyber attacks, it also acknowledged that releasing this report has put itself somewhat at risk.
“We are acutely aware of the risk this report poses for us,” Mandiant noted. “We expect reprisals from China as well as an onslaught of criticism.”
In addition to the detailed report, Mandiant provided more than 3,000 APT1 indicators of compromise, including domain names, IP addresses, X.509 encryption certificates and MD5 hashes of malware used by APT1’s attackers, in order to help organizations identify and defend against APT1 operations.
The full report from Mandiant can be found here (PDF), and the Appendix and 3,000+ APT1 Indicators can be found here (.zip). Mandiant also provided a video showing actual APT1 activity which is embedded below.
This report is likely to be one of the most important reports of the year and should be required reading for any information security professional—or if it were up to me, everyone within an organization.
















