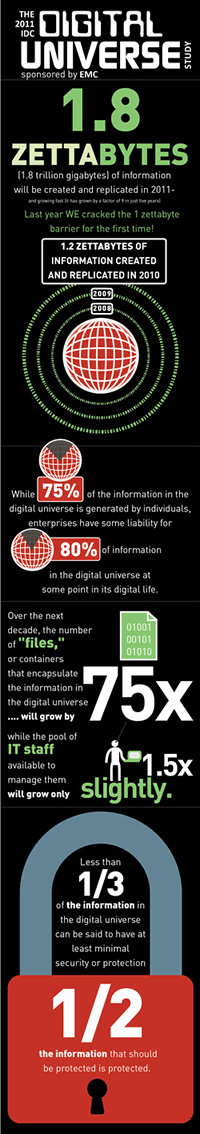
The world is creating massive amounts of data. How much? According to the results of the EMC-sponsored IDC Digital Universe study released today, 1.8 zettabytes of data will be created and/or replicated in 2011, revealing that the world’s information is more than doubling every two years—a rate faster than Moore’s Law.
 So, what does 1.8 zettabytes of data is equivalent to in the real world? EMC shared some interesting stats to help put the massive volume of data being created into perspective:
So, what does 1.8 zettabytes of data is equivalent to in the real world? EMC shared some interesting stats to help put the massive volume of data being created into perspective:
• Every person in the United States tweeting 3 tweets per minute for 26,976 years nonstop
• Every person in the world having over 215 million high-resolution MRI scans per day
• Over 200 billion HD movies (each 2 hours in length)—would take 1 person 47 million years to watch every movie 24×7
• The amount of information needed to fill 57.5 billion 32GB Apple iPads.
According to IDC, since 2005 annual enterprise investments in the Digital Universe—cloud, hardware, software, services, and staff to create, manage, store and generate revenue from the information—have increased 50% to $4 trillion (USD).
With this massive growth, comes many challenges. IDC notes that staffing will be a major challenge, with organizations having a hard time finding enough workers with the skills, experience, and resources required to manage the massive growth in data. Organizations will also need to put staff and resource into protecting this data, as currently, less than a third of the information being created can be said to have at least minimal security or protection; only about half the information that should be protected is protected.
According to IDC, by 2020, IT departments worldwide will experience:
• 10X the number of servers (virtual and physical).
• 50X the amount of information to be managed.
• 75X the number of files or containers that encapsulate the information in the digital universe, which is growing even faster than the information itself as more and more embedded systems, such as sensors in clothing, in bridges, or medical devices.
• 1.5X the number of IT professionals available to manage it all.
While cloud computing accounts for less than 2% of IT spending today, IDC estimates that by 2015 nearly 20% of the information will be “touched” by cloud computing service providers — meaning that somewhere in a byte’s journey from originator to disposal it will be stored or processed in a cloud. Perhaps as much as 10% will be maintained in a cloud.
The Digital Shadow Has a Mind of Its Own: The amount of information individuals create themselves—writing documents, taking pictures, downloading music, etc.—is far less than the amount of information being created about them in the digital universe.
The Liability and Responsibility is with Enterprises: While 75% of the information in the digital universe is generated by individuals, enterprises have some liability for 80% of information in the digital universe at some point in its digital life.
Other Key Findingsin the EMC Digital Universe Study:
• New security practices and tools can help enterprises identify the information that needs to be secured and at what level of security, and then do so from specific threat protection devices and software to fraud management systems and reputation protection services.
• New capture, search, discovery, and analysis tools can help organizations gain insights from their unstructured data, which accounts for more than 90% of the digital universe. These tools can create data about data automatically, much like facial recognition routines that help tag Facebook photos. Data about data, or metadata, is growing twice as fast as the digital universe as a whole.
• Business intelligence tools increasingly are dealing with real-time data, whether it’s charging auto insurance premiums based on where people drive, routing power through the intelligent grid, or changing marketing messages on the fly based on social networking responses.
• New storage management tools are available to cut the costs of the part of the digital universe we store, such as de-duplication, auto-tiering and virtualization, as well as to help us decide what exactly to store, as in content management solutions.
• Cloud computing solutions – both public and private and a combination of the two known as hybrid – provide enterprises with new levels of economies of scale, agility, and flexibility, compared to traditional IT environments. Long term this will be a key tool for dealing with the complexity of the digital universe.
• Cloud computing is enabling the consumption of IT-as-a-Service . Couple that with the Big Data phenomenon, and organizations increasingly will be motivated to consume IT as an external service vs. internal infrastructure investments.
• The growth of the digital universe continues to outpace the growth of storage capacity. But keep in mind that a gigabyte of stored content can generate a petabyte or more of transient data that we typically don’t store (e.g., digital TV signals we watch but don’t record, voice calls that are made digital in the network backbone for the duration of a call).
“The chaotic volume of information that continues growing relentlessly presents an endless amount of opportunity—driving transformational societal, technological, scientific, and economic changes,” said Jeremy Burton, Chief Marketing Officer, EMC Corporation. “Big Data is forcing change in the way businesses manage and extract value from their most important asset – information. EMC is at an ideal crossroad to help our customers—from the world’s largest enterprises to governments to small businesses—exploit the hidden value in the digital universe as they continue on their journey to the cloud.”
The full report is available here (Free PDF Download, No Registration Required)













