Tachyon Takes on Tanium With Promise to Go From Detection to Remediation Across the Entire IT Estate in Seconds
Time to detect and time to remediate is the difference between an incident and data loss. But while there have been dozens of new products designed to help the security team detect incidents, there has been very little that helps IT Ops remediate rapidly across the entire estate.
One of the problems is that detection and remediation are separate operations often handled by separate teams: security and IT. But security is not IT’s only customer — it must also respond to compliance, audit, and virtually every operational department in the organization with requests for enhancements or completely new apps.
The result is a huge workload made more difficult by the false positives that come from many of today’s threat detection systems. According to 1E’s own research involving 1000 IT professionals, more than half spend 25% of their time responding to unplanned incidents coming from urgent security updates, configuration changes and software audits.
Today 1E has launched Tachyon, designed to give IT operations instant actionable access into the furthest reaches of the entire IT estate (up to 1.5 million endpoints), regardless of distribution or operating system. Agents on every endpoint, whether server, desktop, mobile or IoT device can be queried from the Tachyon server. Incidents can be isolated and remedial action taken — within seconds across the entire estate.
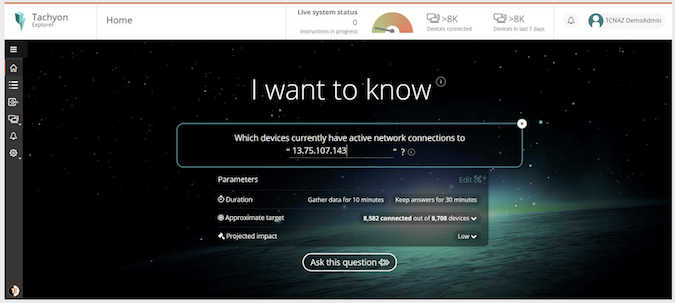
Stuart Okin, SVP of product at 1E, told SecurityWeek to think of Tachyon’s front end like ‘a Google for the IT estate’. Questions can be asked and replies drawn from every endpoint in seconds. Based on those answers, remedital action can be taken — again within seconds.
Okin gave an example involving abuse of Java. Assume that the security team has learned that a Java vulnerability is being exploited, and has passed this information to IT Ops. A single question to Tachyon asking for device software filtered by Java displays all devices at risk. A second question looks for historical evidence of connection to the attacker’s IP address. Within seconds, all (if any) compromised devices have been located.
Further communication with the attacker can be blocked instantly by instructing Tachyon to add a new rule to the local firewall blocking that IP address. Repeating the process will now confirm that no devices can connect to the attacker.
This principle applies across the board. If the security team learns of current a threat or detects indications of compromise through other threat intelligence systems, and can define the threat, the IT team can use Tachyon to locate and remediate within seconds. Of course, it needn’t be a security threat — it could be a threat to regulatory status, or a requirement from audit. It could be used, for example, to locate privileged accounts with access to sensitive data and to remove any that are not strictly necessary. Confirmation with precise details on the remaining privileged accounts can be sent to audit as necessary.
Okin stressed that Tachyon is not designed to replace any existing investments, but to work with them to enhance their performance. Microsoft SCCM is an example. “While other vendors are promoting a rip-and-replace approach, we built Tachyon from the ground up to layer on top of Microsoft SCCM, with a light footprint that enables speed and responsiveness,” commented Sumir Karayi, founder and CEO of 1E.
This was confirmed by a Fortune 500 health insurance company, which was one of the first users of Tachyon. “We rely heavily on Microsoft SCCM and other 1E solutions to automate everyday IT tasks such as software updates, but lacked the ability to identify and remediate severe problems instantly,” said the organization’s infrastructure engineer manager. “1E’s Tachyon adds those real-time capabilities – helping us ‘save the day’ in an emergency. With Tachyon, we can now address big problems in seconds rather than hours, in an organized, controlled way.”
Key to Tachyon’s workings are agents on each endpoint. These query the device and maintain a secure communication with the Tachyon server. They provide the functionality for remedial steps, and ensure that the system is eminently extensible by allowing additional functionality to be introduced without requiring any upgrade to the core system. It is designed to be endpoint cross platform, supporting Microsoft, Mac, Linux, mobile and IoT — making it suitable for large corporations and the emerging internet of things.
The strength of the Tachyon approach is that it doesn’t replace anything, nor does it attempt to automate decision making. Indeed, where remedial action can be described as an ‘impactful change’, a second approval can be required before the remediation is actioned. It makes existing systems work more efficiently and very much faster. Organizations will still need threat analysts to recognize possible incidents; and IT Ops to effect remediation where necessary. Tachyon allows the two teams to work together far more effectively, so that a potential incident can go to detection and remediation in seconds rather than hours or days.










