I’m probably stating the obvious, but a brief look at security reports that summarize 2014 demonstrates that attackers, again, have the upper hand. The following summary statistics* reveal a very clear picture:
• Number of successful attacks annually has increased by 144%
• The cost of data breach has increased by 96%
• Time it takes to resolve a cyber-attack has increased 221%
(*Based on internal analysis of the results from the 2011-2014 “Cost of Cyber Crime Study” reports from Ponemon Institute and HP)
The market is good at presenting statistics, but usually when analyzing the reasons for these disturbing trends, the market doesn’t do such a good job. Yes, we will see explanations for the trend based on new attack motivations such as hacktivisim, financially motivated attacks, government investments in cyber defense and offense – all this is true but, given the multi-billion dollar investments in cyber security, why are attackers still so successful?
Today’s attacks evade most advanced cyber-attack detection and prevention technologies in a matter of days and sometime even hours. Attackers behind well-organized advanced attack campaigns have the capability to analyze the security products’ capabilities before and during the attack and then to modify their attack tools, create new malware software, change the “route” of attack etc. all in a way that will bypass defense and, eventually, achieve the attack’s goal.
Over the past few years we’ve seen many well established security companies as well as early stage startup companies offer innovative security solutions. These companies have tried every possible technology in order to try and automatically predict what the attacker will do next, to predict how the malware will evolve into a new variant, and to identify abnormal network behavior.
We have also been hearing for years about new machine learning algorithms, various techniques to analyze big data, advanced sandbox and emulation techniques, honeypot technologies, reputation intelligence feeds etc. – and as said, unfortunately all are eventually bypassed by the persistent attacker.
The following diagram provides a high level and simplified abstract illustration of what I call as “the advanced threat problem”.
The figure below represents the current state of the security arena, in which cyber security protections can detect and prevent threat vectors in a limited area that I define as the “protection space”.
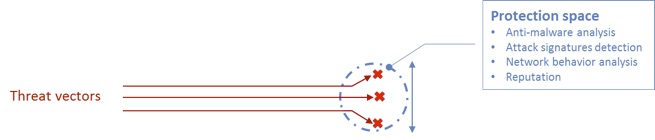
Inside this abstract protection space, which scopes the different attack vector variations, each security technology can predict with high confidence certain amounts of potential attack vectors and flag about them. However, when dealing with advanced persistent attack campaigns, the situation is different.
As shown in the second figure below, persistent attack campaigns include the capability to analyze the cyber protection mechanisms, measure their level of predictability (i.e., define their protection space) and then design the attack accordingly:
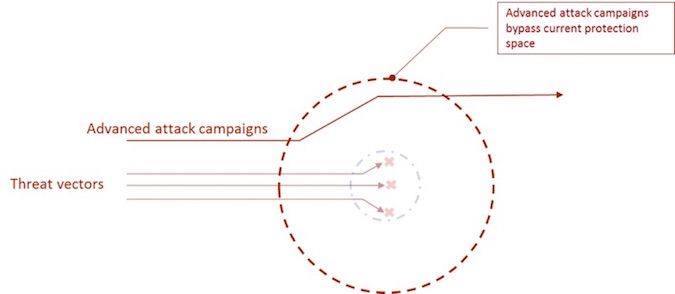
Advanced attack campaigns are designed to bypass the protection space and, once it is bypassed, the battle is lost.
This brings me to my main point: The advanced threat problem doesn’t lay in the fact the current technologies are not good enough, as these technologies are doing well within their protection space. The problem is that when these security technologies are bypassed (and every commercial security technology can be bypassed), they cannot be “programmed” to detect and prevent the new attack behavior, the same attack that has breached their protection-space borders.
“Programmability” of security product will allow the security experts to take control and fight back (see illustration below).
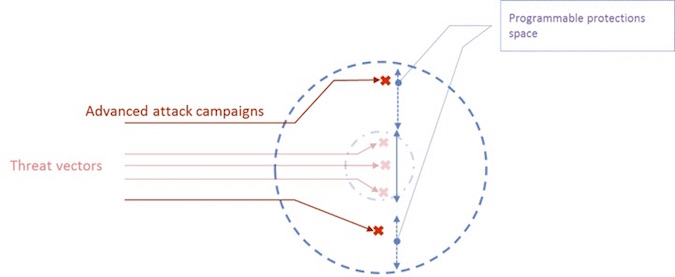
Programmability can mean many things, and it is certainly not a simple task to design a security product that is also a programmable one. The main challenge is to design a security product that is first of all a framework that includes a security language, that allows security experts to program new types of detection and prevention functions or to extend the capabilities of existing functions, and fast.
Development of a security programming language and a framework that compiles this language into real security processes are far from being a trivial task but it seems to be the only step that will allow security experts to fight back. This approach would allow the defenders to be as persistent, if not more, than the advanced attackers.
To summarize, a paradigm shift in the design of security products need to take place. Such a shift would allow network administrators and network security experts to start designing their own security solutions, rather than just administrate existing solutions in their limited security protection space.














