Update – 10/12/10 9:50AM – There have been reports that this attack used “Bugat” Malware in addition to Zeus (More)
On Monday morning, cybercriminals began sending massive volumes of spam email messages targeting LinkedIn users.
Starting at approximately 10am GMT, users of the popular business-focused social networking site began receiving emails with a fake contact request containing a malicious link.
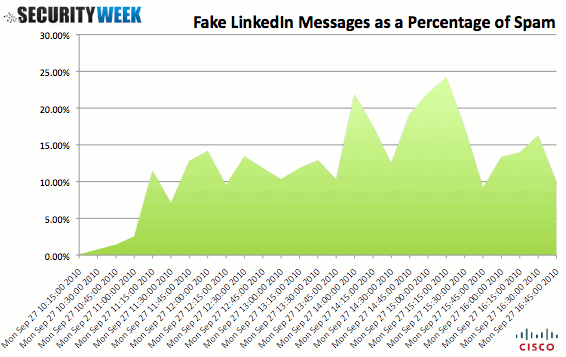
According to Cisco Security Intelligence, these messages accounted for as much as 24% of all spam sent within a 15-minute interval today. If users click, they are taken to a web page that says “PLEASE WAITING…. 4 SECONDS..” and then redirects them to Google, appearing as if nothing has happened. During those four seconds, the victim’s PC was attempted to be infected with the ZeuS Malware via a “drive-by download” – something that requires little or no user interaction to infect a system.
When Zeus infects PCs, users rarely notice any harm, and those who click on a link will may even have a chance manually download the executable file, as the malware first runs a series of browser exploits. ZeuS, also known as Zbot, WSNPOEM, NTOS and PRG, is the most prevalent banking malware platform for online fraud, and has been licensed by numerous criminal organizations. The program then waits for the user to log onto a list of targeted banks and financial institutions, and then steals login credentials and other data which are immediately sent to a remote server hosted by cybercriminals. It can also modify, in a user’s browser, the genuine web pages from a bank’s web servers to ask for personal information such as payment card number and PIN, one time passwords, etc. A new variant recently emerged that targets mobile devices – ZeuS in the Mobile or “Ztimo”- used to overcome two-factor authentication.
“Criminals are misusing brands familiar to business users to trick them into becoming infected by data stealing malware,” said Cisco Security Researcher Henry Stern. “They want to infect those users with access to large-dollar online commercial bank accounts. This attack is most interesting because of its scale. While there have been many previous attacks that impersonate social media sites, the scale of this attack, tens of billions of messages, makes it notable. The criminals behind this attack are among those who stole over US$100m from commercial bank accounts in 2009,” Stern added.
The chart below shows the spike in fake emails targeting LinkedIn users to spread the ZeuS Malware.