The 2016 Ponemon ‘Cost of Data Breach Study‘ shows that breach-related costs are continuing to rise: a 29% increase in the total cost since 2013, and a 15% increase in the per capita cost over the same period. The average cost per lost or stolen record within the scope of the study is now $158.
Each year Ponemon conducts extensive interviews with several hundred different companies across the globe. This year it involved 1,500 interviews with 383 companies in 12 countries that had experienced data losses of between 3,000 and around 100,000 records. Mega breaches (such as Sony) are specifically excluded because they are still the exception rather than the rule. Similar companies and industrial sectors are chosen each year to maintain continuity and allow year-on-year comparisons.
The study shows a surprising variance in costs between both geographical region and industry sector. The highest per capita organizational costs are incurred in the US ($221) and Germany ($213); with the lowest in Brazil ($100) and India ($61).
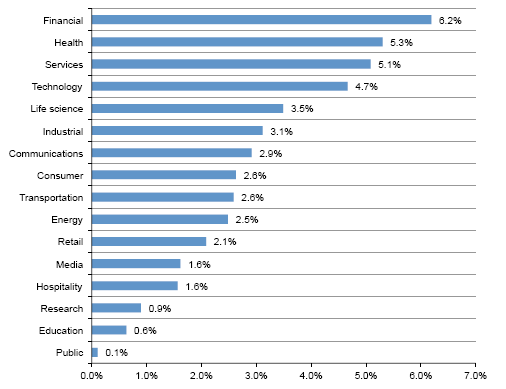
The average global cost per lost record is $158. This is higher in heavily regulated industries such as healthcare ($355), education ($246) and finance ($221); and lower in transportation ($129), research ($112) and the public sector ($80).
Such costs, consistent now over several years, should be taken as inevitable. “Over the many years studying the data breach experience of more than 2,000 organizations in every industry, we see that data breaches are now a consistent ‘cost of doing business’ in the cybercrime era,” said Dr. Larry Ponemon. “The evidence shows that this is a permanent cost organizations need to be prepared to deal with and incorporate in their data protection strategies.”
However, the stand-out figures for security practitioners are the effect of the time-to-detect, encryption and inccident response plans on the overall costs. These are all areas where specific action can reduce probable costs. And the probability of those costs can be calculated from this and earlier studies. “While the likelihood of a data breach involving a minimum of 10,000 records is estimated at approximately 26 percent over a 24-month period, the chances of a data breach involving a 100,000 records is less than 1 percent,” states the report.
The existence of an incident response team and ‘extensive use of encryption’ reduced the cost per record lost by $16. Ponemon’s figures also show an even more dramatic cost difference between a time-to-detect of less than 100 days (total average cost of $3.23 million) and that of more than 100 days ($4.38 million).
These figures could be used to generate an argument, complete with potential ROI, for using encryption, investing in incident detection (including threat information sharing), and developing an incident response plan.
This year’s ‘Cost of Data Breach Study’ was sponsored by IBM. “The amount of time, effort and costs that companies face in the wake of a data breach can be devastating,” said Ted Julian, vice president, Resilient (an IBM Company); “and unfortunately most companies still don’t have a plan in place to deal with this process efficiently. While the risk is inevitable, having a coordinated and automated incident response plan, as well as access to the right resources and skills, can make or break how much a company is impacted by a security event.”












