Firesheep Extension for Firefox Enables HTTP Session Hijacking For the Masses. Instantly Hacks Into Facebook, Twitter, Hotmail and Many More Sites With Ease.
A new Firefox extension developed by Eric Butler, a freelance web application and software developer from Seattle, WA, makes it dead simple to hack into someone’s social networking and email accounts. With the right setup, and using the “FireSheep” extension for FireFox, you can be logged into someone’s facebook (or any other of the supported sites) within seconds. The extension essentially enables anyone on an insecure wireless network to access user login info for all major social networks and other popular web services.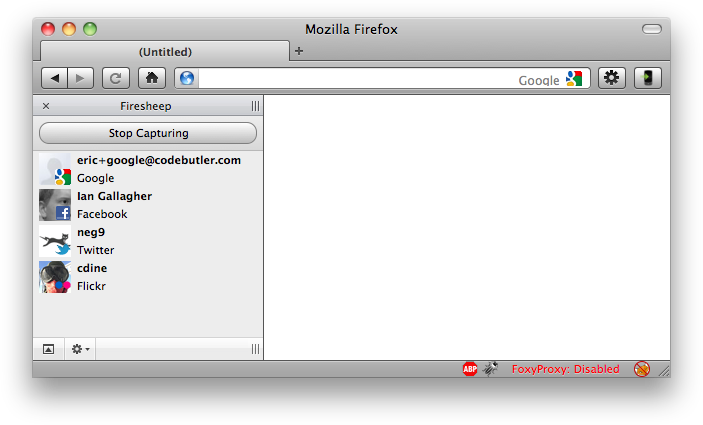
This extension makes something that was already possible, but typically harder to do, incredibly easy.
SecurityWeek decided to test it out to see how it worked. It’s scary how easy this tool made hacking sessions and stealing cookies. Since we didn’t have an unsecured wireless network setup in our office, we started by setting adding a router to our network and left the network open an unsecured (no wireless network password).
We installed the Firesheep Firefox extension on a Mac in the office, logged onto the unsecured wireless network and waited. We quickly grabbed our iPad, logged onto the same unsecured network, opened Safari and logged into Facebook. Within seconds, the Facebook account showed up in our list. One click and we were instantly logged in as that user. Scary. From download of the extension to successful login took about five minutes. No tricky packet sniffing software, just a simple Firefox extension, all within the browser.
During our short test we were able to hijack sessions from Google, Yahoo, Facebook and Amazon. We have not tried others yet. The key to a successful hijack is logging into the sites WITHOUT using HTTPS. With Gmail, we were unable to successfully get into the HTTPS protected session, but were able to login to other non-https protected Google services.
“As soon as anyone on the network visits an insecure website known to Firesheep, their name and photo will be displayed in the window. All you have to do is double click on their name and open sesame, you will be able to log into that user’s site with their credentials,” Butler writes.
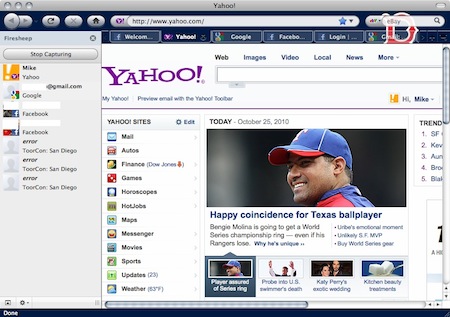
One thing to note is that once the hijacked user logs out of their account, you’ll be logged out as well.
How does this work?
As Eric explains in his blog post announcing the extension, “It’s extremely common for websites to protect your password by encrypting the initial login, but surprisingly uncommon for websites to encrypt everything else. This leaves the cookie (and the user) vulnerable. HTTP session hijacking (sometimes called “sidejacking”) is when an attacker gets a hold of a user’s cookie, allowing them to do anything the user can do on a particular website. On an open wireless network, cookies are basically shouted through the air, making these attacks extremely easy.”
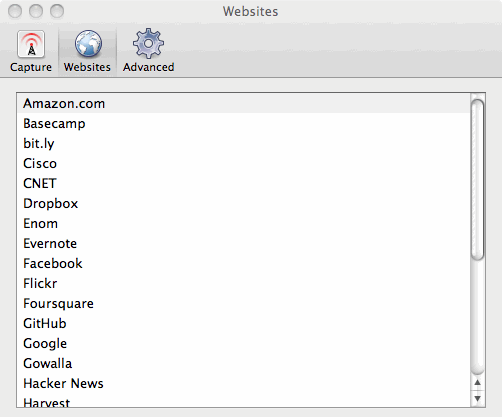
Firesheep is currently able to hijack cookies from Amazon.com, Basecamp, bit.ly, Cisco, CNET, Dropbox, Enom, Evernote, Facebook, Flickr, Github, Google, HackerNews, Harvest, Windows Live, NY Times, Pivotal Tracker, Slicehost, tumblr, Twitter, WordPress, Yahoo, Yelp.
How do you protect your self against these types of attacks?
Use wireless networks you trust and always use HTTPS whenever possible when logging into any personal accounts. If you’re reading this post while using the free Wifi at coffee shop near a college or university today, and happen to be logged into any of the many services that Firesheep can hijack, you may want to think about logging out. Techcrunch also has a couple tips on protecting yourself from Firesheep and other attacks that take advantage of unsecured wireless network traffic.
On his LinkedIn page, Eric Butler says he’s “looking for a position to build products that users love.” My guess is that he’ll have some offers on the table soon as a result of the exposure he’ll be getting from this project.
Related: Google Admits Streetview Cars Collected “Entire Emails, URLs and Passwords” from Wireless Networks
Tags: Firesheep, Browser Session Hack, cleartext session ids, hacking wifi session, Firesheep Extension stats














