Cybercriminals ramped up the creation of Domain Name System (DNS) infrastructure for exploit kits by 75 percent year-on-year during the third quarter of 2015, a recent report from Infoblox Inc. reveals.
According to the company’s Infoblox DNS Threat Index, powered by IID, Angler is the largest threat among exploit kits. However, the report also shows that exploit kit activity was driven by incidents of the Angler, Magnitude, Neutrino, and Nuclear crimeware families, and that a significant contributor to the command-and-control (C&C) category was domain generation algorithm (DGA) based malware Matsnu.
Infoblox notes that the increase in exploit kits is alarming because the category represents the automation of cybercrime and because attackers can use them to target individuals, businesses, schools, and government agencies. Exploit kits are created by a small number of cybercriminals, but they can be rented to low-skilled threat actors with little technical knowledge.
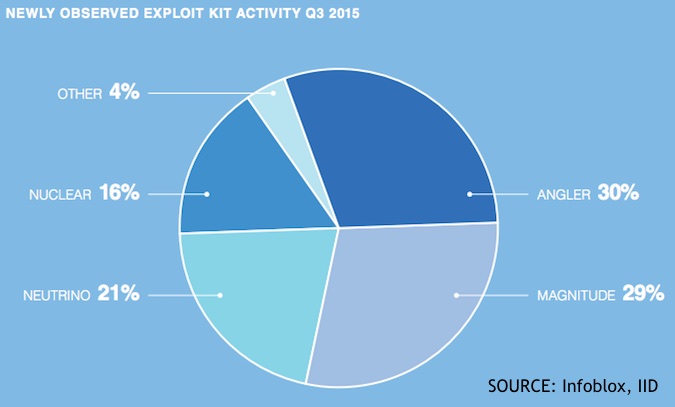
The Angler, Magnitude, Neutrino, and Nuclear exploit kits accounted for 96 percent of the category’s activity in the third quarter of the year. Angler took the first position with 30 percent of total activity, followed closely by Magnitude with 29 percent, while Neutrino and Nuclear took the third and fourth positions, with 21 percent and 16 percent of exploit kit activity, respectively.
Exploit kit attacks are usually conducted via spam emails and compromised websites, but can also be embedded in online ads (malvertising), and deliver a malicious payload when the user clicks on emails or ads. By taking advantage of vulnerabilities in other applications, exploit kits can plant ransomware, capture login credentials, or sensitive data.
Hackers frequently update exploit kits to take advantage of the latest zero-day vulnerabilities in popular software such as Adobe Flash Player. In Q3, Forbes.com exposed visitors to malicious advertisements that hackers managed to inject in the website to redirect users to a landing page for the Neutrino and Angler exploit kits.
Recent variants of Magnitude were used to target vulnerabilities in Adobe’s Flash Player and to deliver Cryptowall 3.0 ransomware, while Neutrino targets vulnerabilities in older versions of Java to download ransomware. The Nuclear exploit kits targets flaws in Adobe Flash, Adobe PDF, and Microsoft Internet Explorer, is usually used in high-volume compromises, and receives constant updates and improvements.
The report (PDF) also reveals that Matsnu malware, (also known as Androm), has become a significant contributor to the C&C malware category. The malware acts as a backdoor and can also download and install additional malicious software, while using DGA to communicate with C&C servers. With DGA, dynamically generated domains that are used as C&C domains for short periods of time allow bad actors to avoid being blocked.
Phishing is the main driver for malicious activities, despite the fact that it has been around for a long time, mainly because the technique works, the report reads. Courtesy of a rapidly created DNS infrastructure (representing a planting phase), cybercriminals build a base to launch attacks, steal data, and generally cause harm to their victims (during a so-called harvesting phase).
“Cybercriminals don’t stand still, and exploit kits are constantly evolving to take advantage of newly discovered vulnerabilities and to avoid traditional security systems. Organizations need to protect themselves by plugging into reliable sources of threat intelligence, then use that intelligence to disrupt malware communications through protocols such as DNS,” said Rod Rasmussen, chief technology officer at IID, said.
In September, Kaspersky Lab revealed that the Angler exploit kit started leveraging the Diffie-Hellman cryptographic algorithm to make it more difficult to detect exploits and prevent analysis. In October, Cisco announced that it caused significant damage to the operations of a cybercriminal group that could have made millions of dollars using ransomware distributed with the aid of the notorious Angler exploit kit.















