The crash of the Malaysia Airlines flight MH17 in eastern Ukraine on June 17 continues to make headlines, making it a perfect event for cybercriminals to leverage in their malicious campaigns.
The incident is surrounded by mystery, and several conspiracy theories have emerged, allowing cybercrooks to exploit the tragedy for a wide range of activities, including spam, scams and malware distribution.
“Unfortunately, the actions of hackers worldwide are designed to generate profits. They focus on psychological triggers, on anything they can use in order to draw people’s attention and con them into getting from them whatever they wish whether its sensitive data, web traffic, clicks and so on,” Alex Balan, product manager at BullGuard, told SecurityWeek. “Any important event which is of high interest (such as tragedies similar to MH17 flight or the results of an election before it is closed) will be used by hackers in order to monetize people’s curiosity and interest.”
Spam and scams
According to security researchers, most of the cybercriminal operations leveraging the MH17 flight incident rely on social media websites instead of spam emails. However, Kaspersky Lab experts spotted one religious email-based spam run abusing the news.
Many of the scams that have been making the rounds over the past few days are connected to websites involved in affiliate marketing strategies based on CPA (Cost Per Action) or CPC (Cost Per Click) monetizing schemes, BullGuard said.
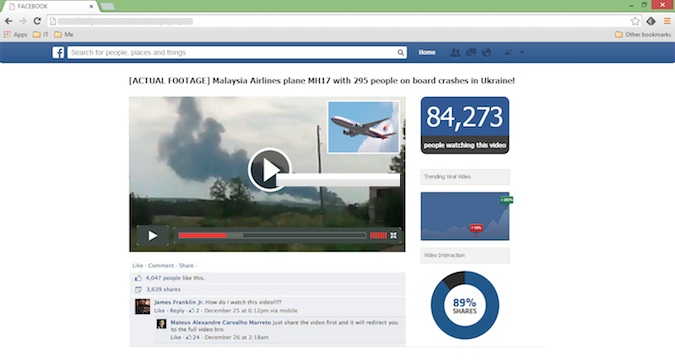
One scam spotted by Hoax Slayer attempts to trick users into completing surveys by promising them actual footage of the missile fired by pro-Russia militants to take down the Malaysian airliner. Other scammers have been trying to lure internauts to shady websites with the help of fake Facebook tribute pages.
Trend Micro analyzed a Twitter spam campaign that started shortly after Malaysia Airlines reported that it had lost contact with flight MH17 from Amsterdam. Several tweets written in Indonesian attempted to lure people to various websites and ads.
“Unfortunately, whenever disaster strikes the Internet scammers are never far behind. The fake social media pages which lead to surveys and use names or photographs of the victims in this case are particularly distasteful. Usually these will use imagery of a downed plane, or a car crash or something else which steers clear of the victims,” Chris Boyd, malware intelligence analyst with Malwarebytes, told SecurityWeek.
“However, it seems that in recent months the so-called ‘shock video’ social engineering has become more and more salacious and poor taste in an effort to keep people clicking. This is likely the next step in that evolution. Elsewhere on social media, rogue links and phishing attempts will continue to be peddled. We advise all netizens to obtain their news from verified and trusted sources, and be wary of anything claiming to offer up ‘exclusive footage’ on social media.”
Malware and other threats
Bianca Dima, e-threat analyst at Bitdefender, pointed out that social media scams can be used to lure users to even more dangerous sites, not just fake surveys.
“We advise users to be cautious when clicking on videos pretending to show exclusive footage of the missile fired at the Malaysian Airlines flight MH17 or any other related images spreading on social networks such as Twitter and Facebook,” Dima told SecurityWeek. “These are all empty promises designed to steal their personal data through bogus surveys, and possibly trick them into downloading malware disguised as plug-ins or add-ons.”
A perfect example of such an add-on was identified and analyzed by Kaspersky Lab expert Fabio Assolini.
“I analyzed a malicious Chrome extension distributed in the attack using the MH17 incident as a bait. The extension captures passwords of Facebook, Dropbox and display adds in sites such as Youtube. It also offers the possibility to download the video watched, but it’s redirecting to sites full of advertisement. It’s more like an adware, needing a lot of installations to generate volume of traffic and some hits to gain money on sponsored links programs,” Assolini said. “This is in fact an interesting move from Brazilian bad guys – they are going to a grayware area, investing their efforts to distribute adware/spyware, not only Trojan bankers.”
The CSIS Security Group in Denmark has identified Facebook likejacking campaigns that rely on bogus MH17 videos. Peter Kruse, a partner and e-crime specialist at CSIS, said they spotted the first campaign on Friday, but several others followed.
“They are written in English and target everyone who could be lured to click the link and then ‘like it’. The webpages try to trick the user into installing a fake Flash Player plugin which installs a BHO [Browser Helper Object] in the browser. This hijacks traffic and introduces popups,” Kruse told SecurityWeek via email.
The Twitter spam run analyzed by Trend Micro also involved links pointing to some malicious domains associated with IP addresses that have been connected to pieces of malware such as Zeus and Sality. The security firm believes that cybercriminals could launch attacks that may lead to personal information theft and system infection.
Many of the bogus crash videos analyzed by BullGuard lead not only to malicous websites, but also to ones designed to trick users into downloading malware disguised as various pieces of software. Some of these sites replicate legitimate services like Facebook, YouTube, and CNN.com.















