Throughout this series of columns, the discussion has focused on topics leading up to where/when the pitched battle takes place and forces are committed to action. These critical aspects ultimately weigh heavily on whether you will win or lose. In US military doctrine, the pitched battle is fought in the close combat area. This is where “forces are in immediate contact with the enemy…or where commanders envision close combat taking place. …The close area is historically the only location where the commander could conduct his decisive operation.”
As shown in Figure 1, military commanders manage their area of operations in order to determine enemy intent, shape their actions, strip key assets and attrit them through the depth of the battlespace. The concept is that by the time the enemy reaches the close combat area, they are degraded and positioned to ensure their defeat. They have been forced to conform to the friendly commander’s plan of actions.
Figure 1: Basic Military Operations Battlefield Management
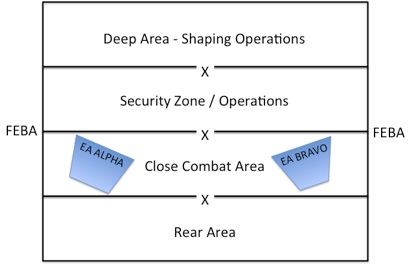
In military operations, the close combat area is usually positioned on defensible terrain. If all goes according to plan, the enemy will be channeled into terrain where they can be slowed in ordered bring the full brunt of direct and indirect fires to bear against them.
Those areas are called engagement areas and depicted in Figure 1 as “EA ALPHA” and “EA BRAVO.” These areas are selected during the Intelligence Preparation of the Operational Environment (IPOE). They are based on the type of enemy the friendly forces face and how the terrain supports the plan. Since it is impossible to defend every bit of the terrain, engagement areas allow defenders to concentrate their efforts in the most likely area the enemy will traverse. Driving the enemy (shaping operations) in the right direction and blinding them along the way (security operations) leads to an increased likelihood of them reaching those pre-planed areas.
This is a very simplistic view of a very complex and sophisticated process. However, the point of the discussion is that effective military units do not hope the enemy goes one way or another. They do not guess on a military course of action. They force the enemy to act the way they want and move them in the direction they want them to go. By the time the enemy reaches the close combat fight, they are battered, bruised, confused and susceptible to receiving the final blow. If the enemy arrived fresh in the close combat area, they would have the ability to fend off any attempt to defeat them and possibly win.
The way most cyber security architecture is deployed, the cyber enemy arrives to the close combat area fresh and ready to do battle. The idea of using defense in depth as commonly referred to in the lexicon of network defenders focuses on positioning defense technologies throughout a network. The majority of the security technology, i.e. Intrusion Detection Systems (IDS), Intrusion Prevention Systems (IPS) and firewalls, and web proxies reside in the security zone (formerly known as the DMZ). They also employ the “defend everyone from everything” theory or constrain the agility of users. Current firewalls cannot block every known bad actor or action without inhibiting performance and throughput. Additionally, an IDS is limited to telling you something bad is happening, but not directing or imposing the will of the defender on the attacker. So by the time the threats arrive at their intended target, a host antivirus or other security application is fighting the pitched battle by itself. This equates to hundreds of computers on a network fighting individual battles with no mutual support between positions or coordinated effort between these systems.
In today’s world of mobile users with laptops or “Bring your own” devices leaving and returning to the enterprise infrastructure, these technologies are not enough. As an alternative or complimentary measure, administrators can segment their networks into engagement areas that the cyber security specialists treat with different care. In Figure 2, critical systems such as web or email servers in EA ALPHA should have dedicated personnel/systems constantly monitoring for malicious or anomalous behavior.
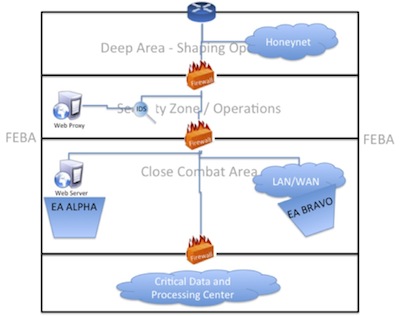
Figure 2: Cyber domain depicted within the basic operational framework
Also depicted in Figure 2, the LAN/WAN contains the majority of the day-to-day computing systems of any network. This is where the majority of the users reside. There are many ways to protect this area. Based on business process and acceptable level of risk these systems can be extremely restrictive or very open. Well-defined business processes and use cases per system user can result in a very functional PC that only allows what is necessary. When the business processes are not well defined or the system travels in and out of the network, then it may be necessary to create another engagement area designed to allow maximum functionality but limiting access to other systems or business functions within the network.
Engagement areas also enable active defense. Active defense is not the process of applying signatures, patching systems, or enforcing rules. These are necessary measures but not active. The most important aspect of using engagement areas to create an active defense is engagement. This means active monitoring of system logs, behavior and netflow and then taking immediate action against systems displaying indicators of compromise. It also means using information about hosts within a network that have similar business functions, user behavior or composition to gain understanding of normal versus abnormal operations.
Active defense in engagement areas also must include rules of engagement for the security team to use against systems that indicate compromise. In most networks, once a system is indicating compromise, it is isolated, investigated and cleaned. The change here is that if the system is actively in the process of probing or compromising other hosts, it must be declared hostile and remote measures must be used to take it off line.
The most important decisions in determining how to conduct close combat operations and how much protection different network elements will receive are made by corporate leadership – not the system administrators of security operations specialists. Like the military, the leadership must make decisions based on operational requirements and risk. These efforts require detailed planning, rehearsal and synchronized execution. Like all military operations, no plan survives first contact with the enemy. But having a plan gives everyone a start point and common understanding from which to maneuver. Understanding how to win the close combat fight starts with a good plan and continues through out the life of the network. “May the odds be ever in your favor.”














