While application sandboxes can isolate threats and protect endpoints from certain types of malware attacks, there are fundamental issues in how they are designed, according to new research from Bromium.
Application sandboxes are useful for isolating certain threats and protecting the operating system from malware, but the protection is not robust enough against advanced or targeted malware targeting the operating system kernel, Rahul Kashyap, chief security architect and head of security research at Bromium, told SecurityWeek.

Kashyap outlined threat vectors sandboxes could not effectively block in a “A Pen-Tester’s Perspective” whitepaper released on Tuesday. Kashyap was careful to point out that he was not saying sandboxes don’t work, or that he was calling out certain vendors for their mistakes. Rather, his point was that sandboxes are often regarded as fail-proof and other security measures are often not implemented on the endpoint because there is a sandbox in place. Sandboxes work well for the job they were designed to do, but other security layers must be in place to handle other threats, Kashyap said.
“People think, I have a sandbox, so I am completely protected,” Kashyap said, and neglect other security steps such as regularly patching the operating system.
The report looked at sandbox technologies from Sandboxie (version 4.0.4), Bufferzone Pro (version 4.04-185), Dell Protected Workspace (powered by Invincea), and the built-in sandboxes in Google Chrome (version 27.0.1453.110 m) and Adobe Reader XI (version 11.0.3). Sandboxie, Bufferzone Pro, and Dell Protected Workspace successfully blocked off-the-shelf exploits. The researchers used the exploit module in Metasploit for CVE-2013-1347, the Internet Explorer vulnerability which was used in the Department of Labor watering hole attack earlier this year.
Bromium’s goal was to highlight the attack surface for these application sandboxes. Most of the issues were due to architectural limitations and implementation assumptions, Kashyap said.
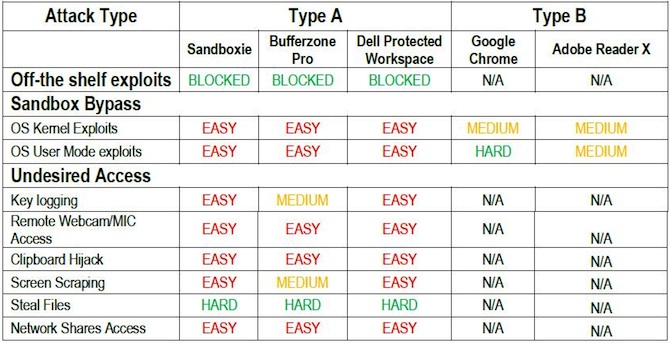
Bromium Labs grouped attacks into two categories, one that bypasses the sandbox entirely, and the other where exploits succeed without breaking out of the sandbox. The bypass techniques focused on exposing the Windows OS kernel and the sandbox itself. The other categories included post-exploitation scenarios, such as keylogging, remotely accessing the webcam and microphone, hijacking the contents of the clipboard, screen scraping, stealing files, and accessing network shares.
The sandbox “makes an assumption that the OS kernel is safe,” which means users will always be “vulnerable to zero day attacks and need to always patch,” the report found.
“The Windows kernel presents a broad attack surface to a skilled attacker, and a successful exploit against the kernel will breach the sandbox,” the report said. While the possibility of a kernel-based attack has been discussed in the past, Bromium researchers believe the attack vector “should be considered as a very real threat, at least as likely to be exploited as other possible vectors.” The researchers developed kernel-level exploits that bypassed the sandboxes for each of the tested products. It was easy to bypass the sandboxing software, but harder to do so in Chrome and Reader, Kashyap found.
Google had hardened the sandbox with additional security features such as restricting TCP/IP networking in case the renderer is compromised, which made it harder for the exploits to succeed.
There may be few vulnerabilities in the sandboxes, but plenty in the operating system kernel, Kashyap noted. Most malware authors haven’t targeted the kernel yet—with the exception of Duqu—because it requires more skill, but Bromium believes it will be more actively exploited in the near future.
IT and network administrators should never rely solely on the sandbox—regardless of what kind or from which vendor—to protect the endpoint, Kashyap said. Other security best practices still apply. Administrators should continue to regularly patch Windows to address both user- and kernel-mode vulnerabilities.
Finally, no one should ever assume that it is safe to execute malware within a sandbox to see what it does, Kashyap warned. If the malware is sophisticated enough, it will be still be able to cause damage, he said.
The full report from Bromium is available here in PDF format.
Related Podcast: Adobe’s David Lenoe on Frustrations With “Partial Disclosure”
Related Reading: Adobe’s Hunt for Sandbox Bypass Flaw a Frustrating Exercise














