Apple Auto-Disables Outdated Versions of Flash Player, Pushes Several Security Fixes in Mac OS X 10.7.4 and Safari Update
Following a recent update to its iOS software that addressed several security issues with Apple’s mobile devices, the Cupertino tech titan pushed another significant software update today, this time for its flagship Mac OS X operating system and Safari Web browser.
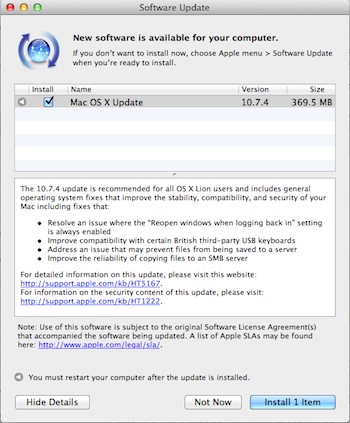
Coming in at 370 MB in size, the newly-released Mac OS X 10.7.4 update is recommended for all OS X Lion users and includes general operating system fixes that improve the stability, compatibility, and security.
But aside from typical security fixes, Apple has made an interesting move in an effort to further protect users. Through this latest software update, Safari 5.1.7 will now automatically disable older – and typically more vulnerable – versions of the Adobe Flash player.
 While many software vendors would prefer OS makers to keep their hands off their software, the move appears to be welcomed by Adobe, which has constantly battled vulnerabilities in its widely installed Flash Player.
While many software vendors would prefer OS makers to keep their hands off their software, the move appears to be welcomed by Adobe, which has constantly battled vulnerabilities in its widely installed Flash Player.
“We welcome today’s initiative by Apple to encourage Mac users to stay up-to-date,” noted Adobe’s Brad Arkin in a blog post. “With the Apple Safari 5.1.7 update released today, Apple is disabling older versions of Flash Player (specifically Flash Player 10.1.102.64 and earlier) and directing users to the Flash Player Download Center, from where they can install the latest, most secure version of Flash Player.”
“After Apple’s recent auto-disabling Java release, this is Apple’s second action reaching across normal vendor boundaries and experimenting with common sense, best practice guidelines,” noted Wolfgang Kandek, CTO at Qualys.
“If Safari 5.1.7 detects an out-of-date version of Flash Player on your system, you will see a dialog informing you that Flash Player has been disabled,” Apple’s security advisory explained. “The dialog provides the option to go directly to Adobe’s website, where you can download and install an updated version of Flash Player.”
Reminding users of the importance of keeping software up-to-date, Arkin added, “The single most important thing we can do to protect ourselves from the bad guys is to stay up-to-date. A thank you to the security team at Apple for working with us to help protect our mutual customers!”
In addition to disabling out-of-date versions of Adobe Flash Player, the latest software update addresses many more security issues. “This release fixes more than 30 vulnerabilities in the core OS, Apple Applications such as QuickTime and some included software such as Samba, Ruby and PHP,” Kandek said.
Other OS-related issues address in the update include fixing an issue where the “Reopen windows when logging back in” setting is always enabled, improved compatibility with certain British third-party USB keyboards, and fixing an issue related to problems with files being saved to a server. The update also improves the reliability of copying files to an SMB server.
For Mac OS X users who run Snow Leopard, a similar update for Snow Leopard 10.6.8 is available as Security Update 2012-0002.














