Last week we looked at how underground markets operate. Similarly to any market economy, the goods being traded in these markets are driven by supply and demand. There is no Consumer Price Index (CPI) for these illicit items. Yet, by tapping into hacker forums we can see the different goods being sold in these forums, as well as their asking price. In the next two articles we explore the current trends within these exchanges to better understand how hackers understand the value of stolen data better than we do.
| Part in a Series on Cybercrime – Read Noa’s Other Featured Cybercrime Columns Here |
Commodity #1: Credit Cards
Credit cards have been a big deal for obvious reasons. Research of IRC logs from 2006 show that from all illegally exchanged data marked as “sensitive”, the majority of this data was attributed to credit card numbers. The asking price of a compromised credit card number ranges from $1 to $25 (depending on the credit line associated with it).
Credit Cards – a Commodity Decreasing in Value
Due to massive data breaches, stolen credit cards became widely available and as a result the face value of individual credit card records has decreased. Symantec’s 2010 Internet Security Threat Report reflects this finding. The report shows that stolen credit cards make up 19% of goods and services available for sale on underground economy servers. Credit card numbers were sold for as little as $0.85 per single card when sold in bulk. These numbers are easily explainable. Of course, the underground market is an open market – so the numbers do fluctuate. Symantec reported findings of lower price tags for the same goods the previous year. But prices also differ across country lines. In the attached screenshot, you can view the “ongoing” rate, and see that stolen EU and Asian credit cards fetch a higher sum than their US counterparts.
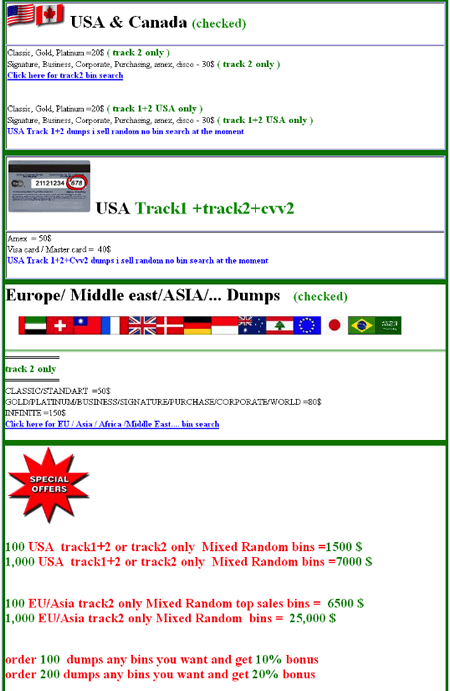
The devaluation of stolen credit cards is not only attributable to supply and demand. It also reflects that banks have applied different anti-fraud mechanisms that make the detection of illegitimate activity more effective, while hindering the criminal’s usage of a stolen card. More so, monetizing on credit cards is not as easy as it sounds.
Credit Cards – Methods to Cash Out
In order to monetize on credit cards, additional identifying information, such as a name and expiration date, are required to complete the transaction. For online purchases, retailers request the CVV2 numbers. Yet, according to the Payment Card Industry (PCI) regulations, consumer sites are not allowed to store CVV2 numbers. These details are mainly sold separately, and as the screen shot shows, this information fetches some high prices. To cash out, a real purchase needs to be performed by the criminal and the real goods should be sold. Alternatively, monetizing on credit cards could be performed by manufacturing real plastic cards with the stolen number. The manufacturing and distribution of these stolen cards entail additional hardware expense, complexities and risks.
Criminals have found some creative ways to cash out on cards.
Here are a few examples:
• Participation in Gambling Sites – In this scheme, the criminal opens two separate accounts in an online gambling site, such as poker. One account is attached to the legitimate card, while the other is attached to the stolen card. Both accounts, under the same user, play in the same table – one against the other- while the “illegal” account loses to the “legal” account. The credit card company sees that the illegal card was used at a gambling site but cannot track the criminal who, in the meanwhile, received the funds.
• Buying from Oneself – In this case, the criminal sets up two accounts while the account with illegitimate card buys goods from the legal account holder. Take for example a recent iTunes scam. In that scheme, a band player used stolen credit cards to buy their own songs.
• Promoting Discounted Goods – This is a common scam – which can even be performed from jail. The cyber-criminals open accounts on sites such as eBay with stolen card information. They then promote selling bona-fide, yet discounted goods. Users quickly register to these discounts and pay the criminal the advertised (discounted) price. Meanwhile, the criminal purchases the real product at full-rate using the illegal card, and delivers the real product to the user.
Commodity #2: Bank Accounts
As opposed to credit cards, bank account details fetch a large amount of money. Yet, in a similar manner, hackers need to invest effort to monetize on the details. Either an individual is required to come in person to the bank and provide additional identifying information, or if an ATM PIN is obtained, a plastic card needs to be manufactured.
Stolen Bank Accounts – A Commodity with Low Returns
As banks continue to develop their anti-fraud mechanisms, the criminals need to take the necessary cautionary steps to avoid detection of their fraudulent activity. Some of these steps include purchasing, or transferring sums, only in small amounts over a long period of time. Often, funds are first transferred to a mule account that collaborates with the attacker. That being said – finding these mules is becoming harder for criminals, as Cisco’s report (PDF) shows that mules are in short supply. It comes as no surprise then, that cyber-criminals are looking for alternative ways to seek more profitable data.
Next Column – Credentials are the New Credit Cards
As the price of credit cards lowers, the price of other goods increases. What are the other goods and how can you protect your customer data from being exchanged in an underground market? Stay tuned for the next column where I’ll discuss the rise of online credentials and provide some advice!
Read More Cybercrime Columns in the SecurityWeek Cybercrime Section















