Identity and Access Management Product Enhancements Help Fulfill Vision for Content-Aware IAM for Distributed and Mainframe Environments
CA Technologies took another step toward fulfilling its vision for Content-Aware Identity and Access management (IAM) today with new releases and enhancements to several of its offerings.
The company today released new updates and enhancements to its CA DLP, CA Identity Manager, CA ACF2 and CA Top Secret products.
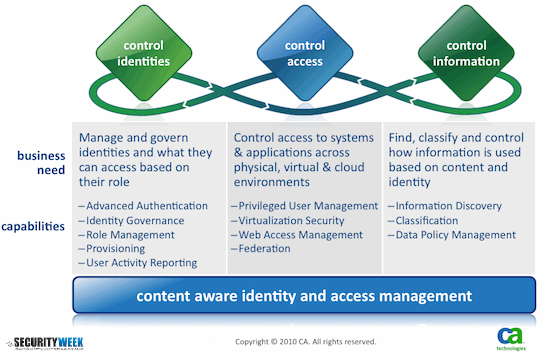
Content-Aware IAM is the next-generation approach to IAM that helps improve information security, reduce risk and meet compliance mandates and helps organizations:
• Reduce administrative effort and cost through the automated provisioning of information use policies to users.
• Improve security by removing data permissions immediately (for example, to view sensitive corporate information) upon termination or transfer of an employee.
• Ease compliance with regulations by detecting and correcting attempted violations of information use policies based on identity.
• Reduce effort and cost associated with compliance audits with easier reporting.
The limitations of traditional IAM is that it stops at the point of access; it doesn’t control how the information that is accessed is used. Content-Aware IAM goes a step further to not only help control identities and their access, but also what they can do with the information.
A breakdown of the releases
• CA DLP: The second major release of CA DLP in a year, CA DLP 12.5 delivers direct CA Identity Manager integration as well as enhanced detection techniques and policy-driven data encryption.
• Content registration detection technique – Scans files and creates a digital “fingerprint” to identify sensitive content as it travels within or exits an organization.
• CA Identity Manager integration – Uses identity attributes in data policy and influences information use (see CA Identity Manager below).
• Policy driven data encryption for data in use – Initiates the encryption of emails, including attachments and files sent to removable devices, via integration with native and third-party encryption technologies.
• Role-based event review – Delivers policy and role-based delegation that helps control visibility to events and enable segregation of duties in environments where CA DLP is deployed for multiple disciplines. For example, IT Security, Legal, Compliance, or HR could all deploy their own data policies and review infractions in isolation, protecting confidentiality and privacy.
• CA Identity Manager: Improved integration and automation with CA DLP allows CA Identity Manager to directly provision, de-provision, and modify users in the CA DLP hierarchy. As users’ roles change, those changes are passed into CA DLP, which allows their data-use entitlements to also automatically change.
• CA ACF2 and CA Top Secret for z/OS: Supports Content-Aware IAM in the mainframe environment with new data classification capabilities that help satisfy regulatory needs to control data use. The new releases of CA ACF2 and CA Top Secret for z/OS can be used to help classify data and ownership according to legal and government regulations. This allows the assignment of specific data classifications to critical resources for purposes of access policy refinement and reporting. Other security and administrative enhancements in these mainframe products include: reporting, certificate management, role-based security, operating system support, and protection of assets.
“Whether you are operating in the distributed world or in a mainframe environment, in order to secure information, comply with regulations and reduce risk, you need to control users, their access and what they can do with the information they access,” said Lina Liberti, vice president, Security, CA Technologies. “We see Content-Aware IAM advancing even further as we share intelligence across our entire IAM portfolio to improve the quality of access decisions and help strengthen an organization’s information security posture.”
CA Technologies recently acquired Arcot Systems which has been part of the company’s portfolio for a short time, and indicated that authentication technology from Arcot will play a role in content-aware IAM as they move forward.















