Yahoo has since released an updated extension to address the issue, which was discovered by a security researcher shortly after Yahoo announced Axis.
When Yahoo released its new Axis extension for Google’s Chrome browser Wednesday, the company accidentally disclosed a private signing key that could be abused by an attacker.
The mistake was discovered by security researcher Nik Cubrilovic shortly after Yahoo launched Axis, which is available both as a mobile browser and a desktop plug-in for the Chrome, Firefox, Safari and Internet Explorer browsers. According to Cubrilovic, the private signing key Yahoo included in the source file could be used to create a malicious, signed browser extension that would be treated as legitimate.
“The certificate file is used by Yahoo! to sign the extension package, which is used by Chrome and the webstore to authenticate that the package comes from Yahoo!,” he blogged. “With access to the private certificate file a malicious attacker is able to create a forged extension that Chrome will authenticate as being from Yahoo!.”
As a proof-of-concept, Cubrilovic cloned the source file to the extension and added a content script that prompts a JavaScript alert, then signed the forged extension with the Yahoo certificate and installed it in Chrome.
“A private key is used by a developer to sign an extension package in order to prove that the extension is actually from the developer,” blogged security specialist Joshua Long. “If a malicious third party were to obtain the private key, they would be able to release an extension signed with that developer’s certificate. In other words, any of us could write an app and fairly convincingly pretend that it was actually from Yahoo.”
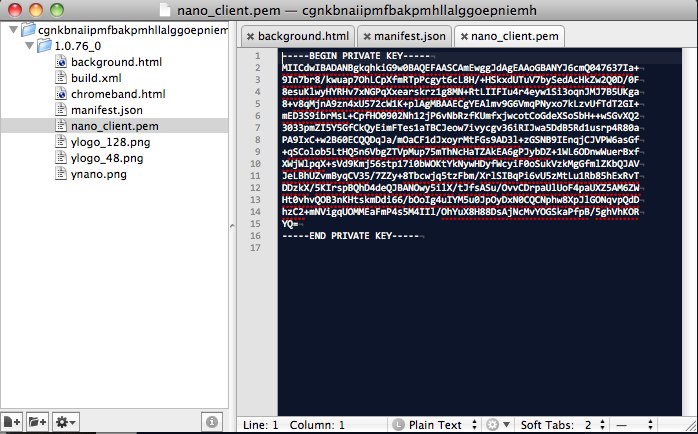
With the private certificate file and a fake extension an attacker could create for example a spoofed package that captures all web traffic, including passwords and session cookies, Cubrilovic blogged.
“The easiest way to get this installed onto a victims machine would be to DNS spoof the update URL,” he explained. “The next time the extension attempts to update it will silently install and run the spoofed extension.”
A Yahoo spokesperson told SecurityWeek that it worked quickly to resolve the issue and has released a new Chrome plug-in. “Yahoo! takes online security seriously… Users who downloaded Yahoo! Axis on Chrome between the hours of 6-9 p.m. Pacific Time on May 23, 2012, are encouraged to uninstall the previous version and reinstall the new version at axis.yahoo.com,” the spokesperson said.














