Security firm Trend Micro said late Monday that it has obtained samples of the malware that is assumed to be responsible for infecting systems at the Israeli police department and effectively knocking them offline.
According to the Times of Israel, the attack was significant enough to have forced all police depart computers to be taken offline temporarily on Oct. 25.
The malware reportedly penetrated the police force via a malicious email with a .RAR archive attached. The email purported to be sent from, Benny Gatz, the head of the Israel Defense Forces, using the email address “bennygantz59(at)gmail.com” and using subject line of “IDF strikes militants in Gaza Strip following rocket barrage”.
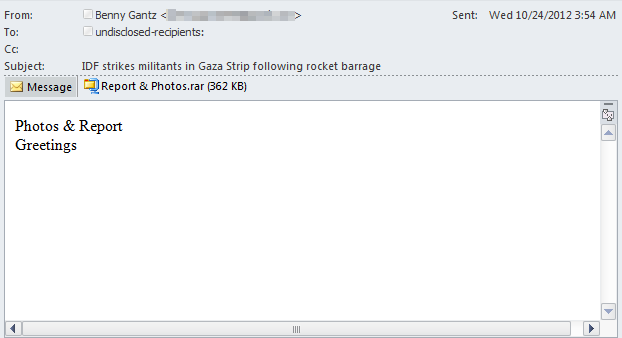
According to Trend Micro, the .RAR attachment included malware, which after being analyzed by Trend Researchers, was determined to include a backdoor using the Xtreme Remote Access Trojan (RAT) or “Xtreme RAT”.
Popular RATs include DarkComet and PoisonIvy, while many other lesser-known RATs exist, such as the PlugX RAT (sometimes called Flowershow) that targeted defense firms using a recently-discovered IE Zero-day. In late September, researchers from AlienVault connected the PlugX attacks to China, going as far as naming the author of the malware after decoding the RAT.
In the case of the attacks against the Israeli Police Force, Roni Bachar, from Israeli security firm Avnet, told the Times of Israel that servers and PCs might have been compromised for as long as a week before the infection was discovered. “It was only late Wednesday night that police realized what happened and ordered that computers be taken offline. Apparently the virus was also distributed to other government departments,” Bachar told the Times.
When Trend Micro analyzed the headers from the malicious emails used to conduct the attack, they determined that the targets were likely to have been within the Israeli Customs agency.
Detected by Trend Micro as BKDR_XTRAT.B, the backdoor used in the attacks appears to be the newest version of Xtreme RAT which is compatible with Microsoft’s new Windows 8 operating system, has enhanced audio and desktop capture capabilities, and brings improved Chrome and Firefox password grabbing, while still maintaining the ability to grab passwords from Opera and Apple’s Safari Web browsers.
In terms of attribution, it’s unclear who is behind the attack, but Bachar has his suspicions.
“The pattern of the attack and the type of virus used were very similar to other cases of attacks which were found to have been sponsored by governments,” Bachar told the Times. “At this point, I think we can be fairly certain that it was sponsored by a nation-state, most likely Iran,” he added.
While many recent global attacks have resulted at fingers being pointed at China and the United States, Iran is being viewed as increasingly aggressive, and being blamed for recent attacks against US financial institutions and a high a profile attack against Saudi oil giant Aramco that erased critical files on about 30,000 of its computers, as well as attacks against Qatari natural gas firm RasGas.
According to recent reports, American officials have “more than a suspicion” that Iran was to blame for the Aramco attacks, that also possibly included recent denial of service attacks on some US banks, according to James Lewis, a senior fellow at the Center for Strategic and International Studies think tank.
According to security firm F-Secure, the Xtreme RAT also appears to have been used in attacks that targeted Syrian anti-government activists.















