“Why do you rob banks?”—Reporter
“Because that’s where the money is.” —Willie Sutton
Despite the enormous attention on data breaches and cyber attacks, relatively little focus (and investment) has shifted to the principal scene of the crime, the servers and storage devices that manage and safeguard the vast bulk of a company’s or government agency’s data.
Whether this data resides in the compute layer in traditional enterprise data centers or, increasingly, in new cloud computing environments such as Amazon Web Services or Microsoft Azure, it is self-evident that perimeter-centric technologies such as firewalls, IDS/IPS, and APT/malware detection systems provide limited value in addressing internal InfoSec issues. If vaults deep within the building protect banks from bank robbers, why do so many security professionals focus so much attention on their data center’s front door?
It’s time to sharpen our focus to prioritize and secure critical information assets at the source, not only at the perimeter. This becomes even more important—and challenging—as we exit the well understood and fairly static client-server era and move to today’s computing environment, where applications and infrastructure have become more dynamic, distributed, hybrid, and heterogeneous. Much of what has made application development organizations more agile—orchestration, RESTful APIs, GitHub—has had a dark side from a security perspective. Increasingly, multi-tier applications are distributed across multiple environments to optimize cost and processing capabilities—e.g., ecommerce, Hadoop—and the notion of the perimeter as the control point can no longer be assumed.
Irrespective of where computing is running, we have to better understand which assets the Willie Suttons of the cyber world would target and develop a strategy that ringfences them off from other, less strategic assets.
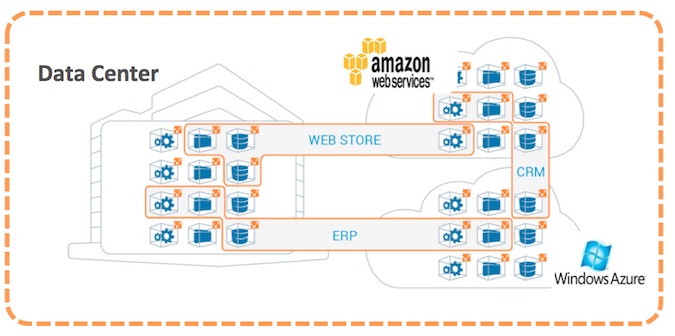
Following is a three-step process for better segmentation of high-value assets:
Step 1. Comprehensively understand your compute environment – You cannot secure what you cannot see. Better security requires a comprehensive mapping of all workloads and network flows. Moreover, this is not a one-time activity, but rather a continuous requirement. Security leadership must move rapidly toward continuous monitoring of compute and network activity.
Step 2. Create a segmentation model that ringfences high-value assets – While all data is important, not all information assets are created equal. If you are a bank, a breach of the cell phone numbers of key employees would be an uncomfortable exposure. Access to top customer accounts and passwords would be dramatically more severe. Security teams must first put the most focus on locking down critical assets from more general compute resources.
Step 3. Create a zero-trust model for high-value assets – Traditional network segmentation models are fairly coarse-grain and create an enormous attack surface for bad actors. If there are 100 hosts on a VLAN, compromising one would lead to a “Typhoid Mary” scenario where the other 99 are exposed. Traditional network segmentation schema—including firewall blacklists, and VLANs/zones—are difficult to maintain in dynamic environments and leave too much attack surface available to hackers. More-focused whitelist models and encryption within and across the data center and cloud can support a zero-trust model for server-to-server communications.
Rethinking security for the interior of your data center (or public cloud) could reduce the trade-offs you’re making between security posture and agility while helping your organization adapt to the new realities of dynamic computing and cyber risk. At the end of the day, catching bank robbers is far less valuable than preventing them.














