Vulnerabilities discovered by a researcher at industrial cybersecurity firm Claroty in Opto 22’s SoftPAC virtual programmable automation controller (PAC) expose operational technology (OT) networks to attacks.
SoftPAC is a software-based automation controller that can be hosted on a Windows device, which, according to the vendor, makes it particularly useful for applications that require more file storage, computing power, or frequent access to files.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) says the product is used worldwide in sectors such as transportation, IT, critical manufacturing and commercial facilities. Claroty has also seen it being used often in the power generation sector.
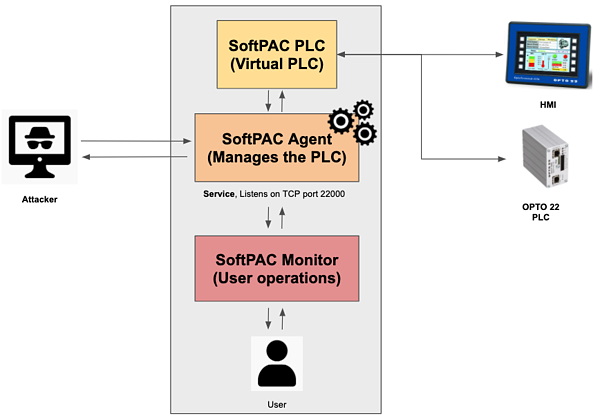
SoftPAC has three main components: Monitor, Agent and the virtual controller itself. The Monitor allows users to start and stop the PAC service and update the SoftPAC firmware. The Agent acts as an intermediary between the Monitor and the PAC.
Claroty researcher Mashav Sapir discovered a total of five vulnerabilities related to the lack of sanitization for firmware update file names, the lack of checks for firmware file signatures, communications over an open port, an uncontrolled search path that allows DLL hijacking, and the lack of authentication or authorization mechanisms.
The flaws can allow a remote attacker who can gain access to the SoftPAC Agent to send start or stop commands to the PAC or update its firmware. Claroty warned that these types of virtual controllers can serve as an entry point to OT networks.
Learn more about vulnerabilities in industrial systems at SecurityWeek’s 2020 ICS Cyber Security Conference and SecurityWeek’s Security Summits virtual event series
“Since the protocol used by SoftPAC Agent does not require any form of authentication, a remote attacker could potentially mimic SoftPAC Monitor, establish a remote connection, and execute start/stop service or firmware update commands. While an attacker could use start/stop commands to cause costly and potentially dangerous operational changes, the firmware update command is an area of even greater concern,” Claroty explained in a blog post.
According to Claroty, an attacker can achieve arbitrary code execution on the targeted system by combining the firmware update vulnerabilities with DLL hijacking. The company has shared a description of an attack conducted in its lab.
“After initiating a connection with SoftPAC Agent, Claroty researchers used this connection to check whether SoftPAC PLC was currently running,” Claroty said. “Next, they sent a stop command to SoftPAC Agent to stop SoftPAC PLC. After stopping the PLC, they sent a firmware update command containing a network path to a malicious zip file. SoftPAC Agent extracted the zip file and dropped the malicious dynamic-link library (DLL) file it contained and placed in the same directory as SoftPAC’s executable. After delivering the malicious file, Claroty researchers sent a command to restart SoftPAC PLC, causing the malicious DLL to load, thus executing the code with SYSTEM privileges.”
Opto 22 patched the vulnerabilities with the release of version 10.3. Version 9.6 and earlier are affected, Claroty and CISA said.
Related: Industrial Controllers Still Vulnerable to Stuxnet-Style Attacks
Related: Many Phoenix Contact PLCs Still Vulnerable Months After Researcher Issues Warning
Related: Another Stuxnet-Style Vulnerability Found in Schneider Electric Software














