Verizon has published its widely anticipated 2016 Data Breach Investigations Report (DBIR), compiled by Verizon with the support of 67 contributing partners. This year’s report includes analysis of more than 100,000 security incidents and 2,260 confirmed data breaches across 82 different countries.
While the industry is flooded with self-serving reports and survey data almost daily, Verizon’s annual DBIR is a must-read report, along with the annual M-Trends report from FireEye-owned Mandiant, and less than a handful of others.
While it should be considered required reading, this year’s Verizon DBIR doesn’t contain many surprises for anyone that keeps tabs on industry trends and the overall threat landscape—but the report and its takeaways are important.
 Not surprisingly, humans were found to be the weakest link across a vast majority of data breaches investigated by Verizon and its partners throughout 2015.
Not surprisingly, humans were found to be the weakest link across a vast majority of data breaches investigated by Verizon and its partners throughout 2015.
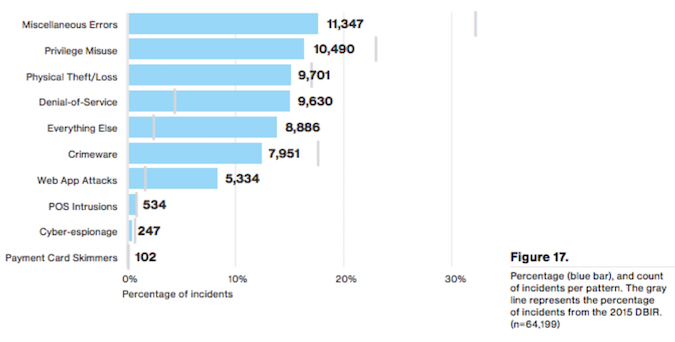
According to the report authors, cybercriminals are continuing to exploit human nature as they rely on familiar attack patterns such as phishing. However, ‘Miscellaneous errors’ by end users of an organization took the top spot for security incidents in this year’s report.
“These can include improper disposal of company information, misconfiguration of IT systems, and lost and stolen assets such as laptops and smartphones,” Verizon said. The report found that 26 percent of these errors involved people mistakenly sending sensitive information to the wrong person. “You might say our findings boil down to one common theme — the human element,” said Bryan Sartin, executive director of global security services, Verizon Enterprise Solutions. “Despite advances in information security research and cyber detection solutions and tools, we continue to see many of the same errors we’ve known about for more than a decade now. How do you reconcile that?”
Credentials in hand make an easy in
When analyzing the 2,260 confirmed data breaches, it was determined that 63 percent involved leveraging a weak, default or stolen password.
“The use of stolen, weak or default credentials in breaches is not new, is not bleeding edge, is not glamorous, but boy howdy it works,” the DBIR says. “Static authentication mechanisms have been attacked for as long as we can remember. Password guessing from an InfoSec perspective has been around at least as long as the Morris worm, and has evolved to prominent malware families like Dyre and Zeus that are designed to (among other bad things) capture keystrokes from an infected device.”
Additionally, in 93 percent of cases, it took attackers minutes or less to compromise systems, the report said. “Organizations, meanwhile, took weeks or more to discover that a breach had even occurred—and it was typically customers or law enforcement that sounded the alarm, not their own security measures.”
The report covers many areas which we could dive into here, but because every security professional should read the report themselves, we will highlight a few key takeaways that stood out.
Zero-Days Not Used Frequently – While advanced attacks leveraging zero-day exploits make for a fascinating headline, Verizon found that most attacks exploit known vulnerabilities that have never been patched despite patches being available for months, or even years. According to the 2016 DBIR, top 10 known vulnerabilities accounted for 85 percent of successful exploits.
Web Application Attacks Hurt – Web application attacks accounted for a total of 5,334 total incidents (19,389 additional with secondary motivation) and 908 were responsible for confirmed data disclosure. According to Verizon, 95 percent of the confirmed web app breaches were financially motivated. “The greater complexity, including the web application code and underlying business logic, and their potential as a vector to sensitive data in storage, or in process, makes web application servers an obvious target for attackers,” the report explained.
Phishing is still a prime attack vector – Its popularity has risen because it is an amazingly effective technique and offers attackers a number of advantages such as a very quick time to compromise and the ability to target specific individuals and organizations.
Mobile and IoT are an unproven attack vector – As SecurityWeek reported when covering last year’s DBIR, mobile and Internet of Things (IoT) attacks continue to play little or no role in today’s enterprise attacks.
“For those looking for proclamations about this being the year that mobile attacks bring us to our knees or that the Internet of Things (IoT) is coming to kill us all, you will be disappointed,” the report notes. “We still do not have significant real-world data on these technologies as the vector of attack on organizations.” Verizon did remind readers, however, that mobile and and IoT threats should not be ignored, and should be considered in your risk management decision-making process. “Proof of concept exploits are real and it’s only a matter of time before a large scale breach impacts mobile and IoT devices,” Verizon said, “which means organizations should continue to be vigilant about protecting smartphones and IoT devices.”
The rise of the three-pronged attack – Verizon has highlighted the rise of a “new three-pronged attack” that they say is being repeated over and over again by cybercriminals. Verizon explained the three-prongs as:
• Sending a phishing email with a link pointing to the malicious website, or a malicious attachment.
• Malware is downloaded onto a targeted individuals PC that establishes an initial compromise and allow for additional malware to be used to target sensitive information
• Use of the credentials for further attacks, for example, to log into third-party websites like banking or retail sites.
In terms of actionable takeaways, Verizon’s team leaves us with these key initiatives that organizations should put into action to significantly reduce their risk profile:
• Know what attack patterns are
most common for your industry.
• Utilize two-factor authentication for your systems and other applications, such as popular social networking sites.
• Patch promptly.
• Monitor all inputs: Review all logs to help identify malicious activity.
• Encrypt your data: If stolen devices are encrypted, it’s much harder for attackers to access the data.
• Train your staff: Developing security awareness within your organization is critical especially with the rise in phishing attacks.
• Know your data and protect it accordingly. Also limit who has access to it.
“This year’s report once again demonstrates that there is no such thing as an impenetrable system, but often times even a basic defense will deter cybercriminals who will move on to look for an easier target,” Sartin concluded.
Sartin’s comments are spot on. In fact, Verizon itself was the victim of a breach, when hackers reportedly stole the details of 1.5 million Verizon Enterprise customers after exploiting a vulnerability in the company’s website.
The 85-page 2016 Verizon DBIR is packed with statistics, incident overviews, and actionable items that you can take back to your security team. Security organization leaders should be sure to read (and digest) the report, and encourage their staff to do the same. Both an executive summary (PDF) and the full report (PDF) are available directly from Verizon in PDF format and no registration is required.
Related: Learn More at the 2016 CISO Forum












