Verizon Data Breach Investigations Report Indicated Cybercriminals Shifting to Smaller, More Opportunistic Attacks; External Attacks and Hacking on the Rise
 Verizon today released its “Verizon 2011 Data Breach Investigations Report“, a comprehensive study that now spans seven years and more than 1,700 breaches involving more than 900 million compromised records. The 74-page report should be required reading for any IT Security, Risk, and compliance professional.
Verizon today released its “Verizon 2011 Data Breach Investigations Report“, a comprehensive study that now spans seven years and more than 1,700 breaches involving more than 900 million compromised records. The 74-page report should be required reading for any IT Security, Risk, and compliance professional.
For the second year in a row, the U.S. Secret Service collaborated with Verizon to produce the report. The National High Tech Crime Unit of the Netherlands Policy Agency (KLPD) also joined the team this year, providing more insight into cases originating in Europe. Approximately one-third of the cases originated in either Europe or the Asia-Pacific region, reflecting the global nature of data breaches.
The Data Breach Investigation Report (DBIR) revealed that data loss through cyber attacks decreased sharply in 2010, but the total number of breaches was higher than ever. Interestingly, the number of compromised records involved in data breaches investigated by Verizon and the U.S. Secret Service dropped from 144 million in 2009 to only 4 million in 2010, representing the lowest volume of data loss since the report’s launch in 2008. Yet this year’s report covers approximately 760 data breaches, the largest caseload to date.
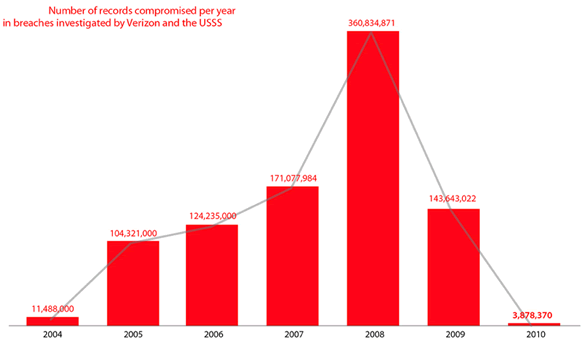
According to the report, the apparent contradiction between the low data loss and the high number of breaches likely stems from a significant decline in large-scale breaches, caused by a change in tactics by attackers. It seems as though cybercriminals are going toward the low-hanging fruit, rather than large-scale, difficult attacks and are finding success using relatively unsophisticated methods to penetrate organizations. For example, only 3 percent of breaches were considered unavoidable without extremely difficult or expensive corrective action.
The report suggests that cybercriminals may be making a classic risk vs. reward decision and opting to “play it safe” in light of recent arrests and prosecutions. Numerous smaller strikes on hotels, restaurants, and retailers represent a lower-risk alternative, and cybercriminals appear to be taking greater advantage of that option.
Outsiders were responsible for 92 percent of breaches, a significant increase from the 2010 findings. Although the percentage of insider attacks decreased significantly over the previous year (16 percent versus 49 percent), this is largely due to the huge increase in smaller external attacks.
Hacking (50% of breaches, 89% of records) and malware (49% of breaches, 79% of records) were the most prominent types of attack, with many of those attacks involving weak or stolen credentials and passwords. For the first time, physical attacks — such as compromising ATMs — appeared as one of the three most common ways to steal information, and constituted 29 percent of all cases investigated.
In a trend that continues, the most common malware infection pathway is installation or injection by a remote attacker. This covers scenarios where an attacker breaches a system and then deploys malware or injects code via SQL injection or other web application input functionality. Attackers are moving up the stack and targeting the application layer, indicating that incorporating a Security Development Life-Cycle (SDLC) approach for application development is becoming more important than ever.
The report showed that nearly two-thirds of malware investigated was customized—the highest the DBIR team has seen. Additionally, most of the records stolen by malware were taken in breaches where customized forms were observed. The extent of customization found in a piece of malware can range from a simple repack of existing malware to avoid AV detection to code written from the ground up for a specific attack. The report showed that in 2010 the majority of customized code had shifted to a level of effort that falls in between these two extremes.
Key Findings of the Verizon DBIR 2011 Report
• Large-scale breaches dropped dramatically while small attacks increased. The report notes there are several possible reasons for this trend, including the fact that small to medium-sized businesses represent prime attack targets for many hackers, who favor highly automated, repeatable attacks against these more vulnerable targets, possibly because criminals are opting to play it safe in light of recent arrests and prosecutions of high-profile hackers.
• Most organizations suffering payment card breaches were not validated as compliant with PCI DSS at the time of the breach. (89%) suffering payment card breaches had not been validated compliant with PCI DSS at the time of the breach
• Outsiders are responsible for most data breaches. Ninety-two percent of data breaches were caused by external sources. Contrary to the malicious-employee stereotype, insiders were responsible for only 16 percent of attacks. Partner-related attacks continued to decline, and business partners accounted for less than 1 percent of breaches.
• Physical attacks are on the rise. After doubling as a percentage of all breaches in 2009, attacks involving physical actions doubled again in 2010, and included manipulating common credit-card devices such as ATMs, gas pumps and point-of-sale terminals. The data indicates that organized crime groups are responsible for most of these card-skimming schemes.
• Malware is being increasingly customized. Nearly two-thirds of malware investigated in the Verizon caseload was customized. In a year that includes more breaches than ever, the increased proportion of customized isn’t a good sign. It means that even the majority of highly-automated and non-targeted attacks against small organizations utlize customized malware, showing that the cost and difficulty of customization is relatively low.
• Stolen passwords and credentials pose major threat. Ineffective, weak or stolen credentials continue to wreak havoc on enterprise security. Failure to change default credentials remains an issue, particularly in the financial services, retail and hospitality industries.
“This year, we witnessed highly automated and prolific external attacks, low and slow attacks, intricate internal fraud rings, countrywide device-tampering schemes, cunning social engineering plots and more,” said Peter Tippett, Verizon’s vice president of security and industry solutions. “It is important to remember that data breaches can happen to any business — regardless of size or industry — or consumer, at any place in the world,” Tipped added. “A good offense remains the best defense. It is imperative to implement essential security measures broadly throughout your security infrastructure, whether that is a small home setup or an expansive enterprise infrastructure.”
A complete copy of the “2011 Data Breach Investigations Report” is available here as a free download.













