As we see from the headlines and from all the FUD, there are many threats out there attacking from many different angles. New attacks, old attacks revisited, sophisticated attacks with numerous obfuscation layers, and simple attacks based on age-old social engineering.
As the saying goes, it’s not about what you do IF you’re attacked, it’s what to do WHEN you’re attacked – or worse, when you’re breached. And with more interconnectivity across business, government, users and suppliers, cyber attackers have a vast, data-rich environment to target.
Data breaches happen. As such, incident response is an important component of your overall cybersecurity program. It’s about preparation for when something bad goes down so that you can respond faster and minimize the damage that is done to your business, your customers, your brand… your bottom line. I’m making a fairly safe assumption here in that I bet you could use more resources on incident response when it all goes down.
Traditionally, cyber threat intelligence (CTI) has been used at the tactical level by defenders, but recently we’re starting to see more use cases of strategic and operational level CTI being plugged into incident response. IR is all about preparation and planning – not only does it help you prevent bad things from happening in the first place, it also informs response scenarios if an incident occurs.
Below I’ve reflected the four primary phases of escalation that I used in my previous role as a CISO for a major transport authority. Of the areas I’ve called out, each would have an assortment of sub-processes that would begin when an issue moves from one phase to another.
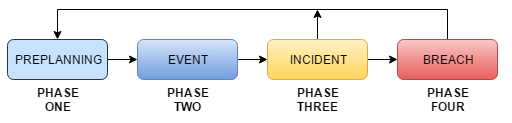
Phase 1: Pre-planning
You cannot respond well when disaster strikes if you haven’t planned for it. Incident response teams typically practice test runs and scenarios to ensure the plan is sound. Strategic and operational threat intelligence can help this aspect of incident response in several ways.
Knowing your adversaries can help in terms of pre-planning. What do I mean by this? What groups would target your business and why? What are they targeting? What is their intent? What are their capabilities? And then tie that to your business to identify what their opportunity is? What are the possible attack scenarios?
CTI not only provides the insights to answer these types of questions, it can help give you a roadmap for a faster, more effective incident response plan. Your pre-planning efforts can be broken down into two areas:
1. Incident Response – Operational cyber threat intelligence would be used here in the form of Threat Scenarios. What I mean by this is that intel would help identify the top threats as well the techniques, tactics and procedures (TTP’s). The identified TTP’s would then translate into incident responder workflows. If one of those threats became a reality for your environment, the defenders would already have the tools, procedures and workflow to address that threat.
2. Breach Response – This is similar to incident response, except this takes more of a business risk management approach. Breach response is where the CIO, CISO, PR/Crisis Management, Risk Management, Counsel and other stakeholders would craft a plan for how to address business risk if a breach occurred, and what the communication would be to customers, regulators, and the general public. Operational and strategic CTI helps inform this process by answering the “So what” question.
Phase 2: Event
Any organization with a security operations center (SOC) has some sort of an alerting engine when an anomaly is detected. This is initially classified as an event of interest. It may have merit, or it just may be noise and a false positive. (The thing to be weary of in general when it comes to event alerting is alert fatigue – too much unevaluated threat data actually can hurt, not help you. If you’re taking in as much data as you can, but not putting reasonable filters on it in terms of relevance to your environment then your incident response team will end up spending a ton of time and money researching things that are irrelevant. Not only is it time wasted, it also takes your eye off the ball when it comes to threats that you should be focusing on.)
Whether it’s your SIEM or a host of other tools that sends the alert, operational and tactical CTI helps provide context. This type of information includes IOCs such as malware, IP addresses, devices, domains, URLs, files, phishing messages, traffic patterns, and adversary TTPs – all of which can help you determine if an event escalates into an incident.
Phase 3: Incident
An event escalates into an incident if it is determined that an adversary established a level of presence within the environment. This is where the pre-planned scenarios kick off. Once an incident has been contained, operational threat intelligence gives defenders more clarity on the campaign, actor motivations, past incidents. For example operational CTI will help you understand what the threat is, who’s behind it, what it’s going after, how it propagates and executes, and what obfuscation techniques used.
More simply put, operational CTI puts the incident through the lens of the Threat Triangle – what is the adversary’s capability, intent and opportunity. Armed with this intel, you can make smarter decisions to minimize this threat, identify the risks that need to be shored up, and kick off the right response procedures.
Phase 4: Breach
An incident escalates into a breach when the organization deems it necessary to report it. Typically this occurs when data exfiltration has occurred and the organization must report it to regulators, customers or employees. In simple terms, Incident Response is how the organization responds internally, and Breach Response is how the organization responds externally.
Post-mortem on a breach is another place where strategic and operational CTI can play an important role. This is where you look back at everything and determine:
• What happened?
• How and why did the breach occur?
• What future steps need to be taken to not face a bad Groundhog Day experience?
CTI adds context here, but not only that – the intel you gain can and should be fed back into your cyber threat intelligence process as well as with your incident response.
At the end of the day, incident response is all about reacting faster and better. The faster and better you can respond, the smaller the impact to your organization. Cyber threat intelligence can help further optimize your incident response processes so that you can not only respond faster and better, but also reduce adversary opportunity and in turn go through fewer incident response fire drills.















