The U.S. government has reissued an alert warning organizations about Conti ransomware attacks as the cybercrime group deals with the recent leaks.
An alert originally released in September 2021 was reissued recently by CISA, FBI, NSA and the U.S. Secret Service. The alert contains technical details on Conti attacks, as well as indicators of compromise (IoCs) that can be useful to defenders.
Shortly after Russia launched an invasion of Ukraine, the Conti group announced its support for Russia, threatening to attack the critical infrastructure of “enemies.” They later revised their statement to say that they condemned the war, but the threat to launch cyber operations in response to the West’s actions remained.
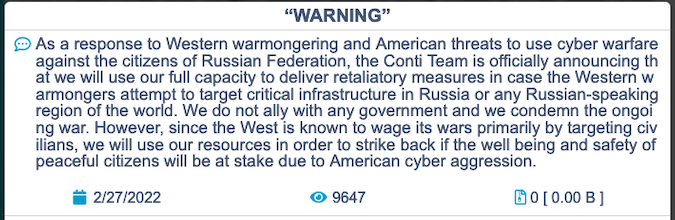
A few days after Conti made the announcement, an individual — a Ukrainian security researcher or possibly a rogue member of the Conti group — started leaking files related to the gang’s operations. The leaks started with some chat logs on February 27 and continued with other files, including Conti ransomware source code, on March 1.
The U.S. government said in its updated alert that the Conti threat actors appeared to remain active, with its victim count rising to more than 1,000.
MDR company eSentire this week reported that the Conti group announced attacks against more than 50 organizations between November 27, 2021, and February 28, 2022.
Conti continues to announce new victims on its website, with nine new targets named this week alone, including two on March 10.
On the other hand, the data leak appears to have had at least some impact on Conti, which, as the leaked files show, operates just like a company, with contractors, employees and HR problems.
The leaked files have enabled researchers to conduct a detailed analysis of the group’s tools, methods and projects. Incident response company BreachQuest has published a report describing Conti leadership and hierarchy, organizational infrastructure, Bitcoin transactions, malware and other tools.
BreachQuest’s analysis of the leaked files showed that Conti spent roughly $6 million on employee salaries, tooling and professional services in the past year alone.
Threat intelligence company Cyberint has also conducted an analysis of the leaked files. Its researchers said that while Conti initially appeared unaffected by the leaks, the group’s senior management “decided to mitigate the damage and tried to cover any tracks that might lead to any members of the group.” It’s worth noting that the person who leaked the Conti files has also made public the identity of an individual allegedly involved in malware development.
“After the main leaks, the last conversations that were leaked showed that the decision was made to go off the grid for some time,” Cyberint researchers said. “It seems that the key members of the group are making efforts to ensure that all relevant files are deleted, all links shared within the conversations are dead, all servers used for the organization’s infrastructure are down.”
Based on chatter between members of the cybercrime organization, Cyberint said, a rogue member is believed to be behind the leak.
According to the cybersecurity firm, it’s unclear if the victims named recently on the Conti website are new or if they were compromised before the leak.
“One way or another, Conti will turn their efforts in the coming days or weeks to rebuilding their infrastructure and relocating all their communication channels and sources very carefully, so the Ukrainian research does not infiltrate this infrastructure as well,” Cyberint said.
Related: Conti Ransomware ‘Acquires’ TrickBot as It Thrives Amid Crackdowns















