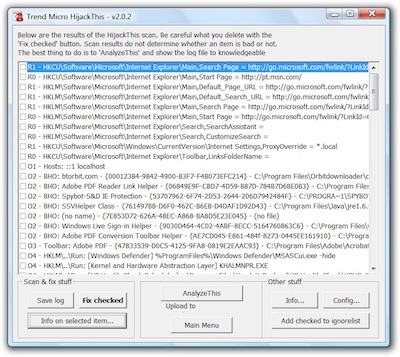
Trend Micro today announced that is has open sourced the code to its popular free security tool, HijackThis. The tool scans systems to find settings that may have been modified by spyware, malware or other programs that have wiggled their way onto a system and caused problems.
HijackThis generates reports to help users analyze and fix an infected or problemed computer. But the tool is not designed for novices – and doesn’t actually determine what’s good or bad. That’s up to you, but it is a good way to keep an eye on things and possibly locate anomalies that may have been missed by other security products. Trend Micro warns that if you don’t know what you’re doing, it’s probably not a good idea to make any changes to your computer settings and system files.
 Cupertino, California based Trend Micro acquired the tool from creator Merijn Bellekom in 2007, and has offered it for free ever since, but now is making the code available to the public. The code, originally written in Visual Basic, is now officially available at Sourceforge here.
Cupertino, California based Trend Micro acquired the tool from creator Merijn Bellekom in 2007, and has offered it for free ever since, but now is making the code available to the public. The code, originally written in Visual Basic, is now officially available at Sourceforge here.
Commenting on the move to open source, Bellekom says users will now be able to improve their anti-malware tools. “This means that other people can build on a solid base to create or improve their own anti-malware tools,” he said.
The tool has been popular in several online security forums, and its common for users of HijackThis to post a log file in order to get feedback from others on what steps to take in the event someone has an infected system.
“The OSS framework provides people with an opportunity to help others in a rich and diverse environment, and this ensures that HijackThis will continue building on its strength in serving the community,” said Paul Laudanski founder of Castlecops.com, a security oriented community that has since shut down.
HijackThis been downloaded well over 10 million times, but Trend Micro hopes the move to open source will bring a new level of interest and further push the tool to the next level.
Trend Micro says it will continue to maintain the original source code and will update the base code on SourceForge as developers make modifications that are essential and positive to the continued improvement of this code.
“As new malicious code is released faster than ever before, the need for analyzing log data to identify new malicious code is more important than ever,” the company said in a statement. “Through this offer to the open source community, the product has the opportunity to develop and become an even better solution to quickly identify new malicious code.”
















