Google has issued a warning to G Suite users after researchers discovered that thousands of organizations expose sensitive information through misconfigured Google Groups instances.
The Google Groups service allows users to create mailing lists, host internal discussions, and process support tickets. These types of communications can include highly sensitive information, which is why it’s important for companies to ensure that privacy and security settings are configured properly.
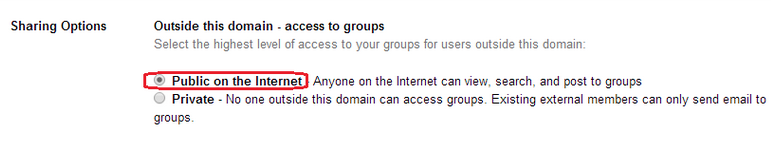
When a group is configured, its creator has to set sharing options for “Outside this domain – access to groups” to either “Private” or “Public on the Internet.” While the default option is “Private,” many organizations have set it to “Public on the Internet,” in many cases likely not realizing that anyone can access the group.
Researchers at Kenna Security have conducted an analysis of roughly 2.5 million domains and identified more than 9,600 organizations that had allowed public access to their groups. After taking a closer look at a random sample of 171 groups, the company estimated that nearly 3,000 of the over 9,600 companies leaked some type of sensitive information.
The impacted organizations include Fortune 500 companies, universities, hospitals, media firms, financial institutions, and even government agencies.
The exposed information includes financial data, passwords, and documents containing confidential information.
“Given the sensitive nature of this information, possible implications include spear-phishing, account takeover, and a wide variety of case-specific fraud and abuse,” Kenna Security said in a blog post.
The company notified some of the organizations leaking highly sensitive data and pointed out that the “views” counter was in a vast majority of cases at zero, which indicates that no one had seen the information.
Kenna has also notified Google, but since this is not an actual vulnerability, the issue cannot be addressed with a patch. The tech giant did say, however, that it’s always reviewing its products to “help users make decisions that are appropriate for their organizations.”
Google has also published a post on its G Suite blog, providing advice on how users can configure their Google Groups settings to better protect their data.
This is not the first time researchers have warned about the risks associated with misconfigured Google Groups instances. Last year, cloud security firm RedLock warned that hundreds of organizations were likely exposing sensitive data through Google Groups. At the time, the company found names, email and home addresses, employee salary data, sales pipeline data, and customer passwords in the exposed groups.
Related: Misconfigured Jenkins Servers Leak Sensitive Data
Related: 1.5 Billion Sensitive Documents on Open Internet
Related: Republican Party Contractor Exposes Details of 198 Million American Voters













